
Summary
With the rapid expansion of stablecoins in cross-border payments, decentralized finance (DeFi), and the digital asset market, anti-money laundering (AML) and counter-terrorism financing (CFT) compliance have gradually become the focus of regulators and industry participants. Traditional AML frameworks face numerous challenges in on-chain environments: on-chain transactions, while transparent, possess anonymity, and off-chain identity information, although complete, suffers from decentralization, creating significant barriers to risk monitoring and compliance enforcement. Against this backdrop, the Hong Kong Virtual Asset Industry Association (HKVAIA) supports the establishment of the Digital Asset Anti-Money Laundering Professional Committee (DAAMC), gathering diverse founding members including SlowMist, Round Coin Innovation Technology Co., Ltd., HashKey Group, and Beosin, dedicated to promoting the compliant issuance of stablecoins and the establishment of industry standards.
This report, one of the important achievements of DAAMC in promoting industry research and knowledge sharing, was written by SlowMist. Combining the team's long-term experience in on-chain tracking, threat intelligence, and compliance practices, it systematically sorts out the technical path of stablecoin AML, covering regulatory background, smart contract layer compliance, address risk management, on-chain and off-chain data integration, AI/ML model application and compliance implementation. It also proposes future trends and industry recommendations, hoping to provide reference for regulators, stablecoin issuers, and virtual asset service providers (VASPs), and promote the sustainable and healthy development of the stablecoin ecosystem in compliance and innovation.
You can view and download the PDF version online. Click the end of the article to read the original text and jump directly to: https://www.slowmist.com/report/SlowMist-2025-Stablecoin-AML-Compliance-Tech-Report-v1.0-CN.pdf
1. Background and Overview
1. Overview of Stablecoins
(1) Definition
Stablecoins are cryptoassets that maintain a relatively stable value by being pegged to fiat currencies, commodities, or other financial assets. Their core objective is to alleviate the trading and payment inconveniences associated with the volatile price fluctuations of traditional cryptocurrencies. In the blockchain ecosystem, stablecoins are not only widely used for payment and settlement, but are also becoming critical infrastructure for cross-border liquidity management and digital financial innovation. As their application expands, they are attracting significant attention from global regulators and technology governance.
(2) Function
From a functional perspective, stablecoins typically serve three purposes. The first is value anchoring. With their relatively stable price performance, they can serve as a unit of account and pricing tool in the cryptoeconomy, helping users and institutions mitigate risk in volatile market environments. The second is cross-border payment and settlement. With their peer-to-peer nature and global accessibility, stablecoins offer potential advantages in efficiency and cost, attracting attention in scenarios such as cross-border trade, remittances, and inter-institutional funds transfers. The third is compliance coordination. As some jurisdictions gradually establish specialized frameworks, stablecoins are beginning to be incorporated into licensing and disclosure systems, becoming increasingly recognized as an integral part of the payment and settlement system, providing a testing ground for the future evolution of on-chain financial infrastructure.
(3) Market capitalization and mainstream stablecoins
After understanding the basic form and functions of stablecoins, their development dynamics can be more intuitively understood in light of the current market landscape. According to the latest data from DeFiLlama (https://defillama.com/stablecoins), as of August 19th, the total market capitalization of the stablecoin market was approximately $276.809 billion. In terms of market share and market capitalization distribution, USDT maintains its leading position, with a market capitalization exceeding $166.3 billion, and has shown a relatively stable growth trend over the past period. USDC ranks second with $67.918 billion, and its market capitalization trend is relatively stable, but there is still a significant gap between it and USDT. Other stablecoins have limited overall scale and relatively mild market capitalization fluctuations.
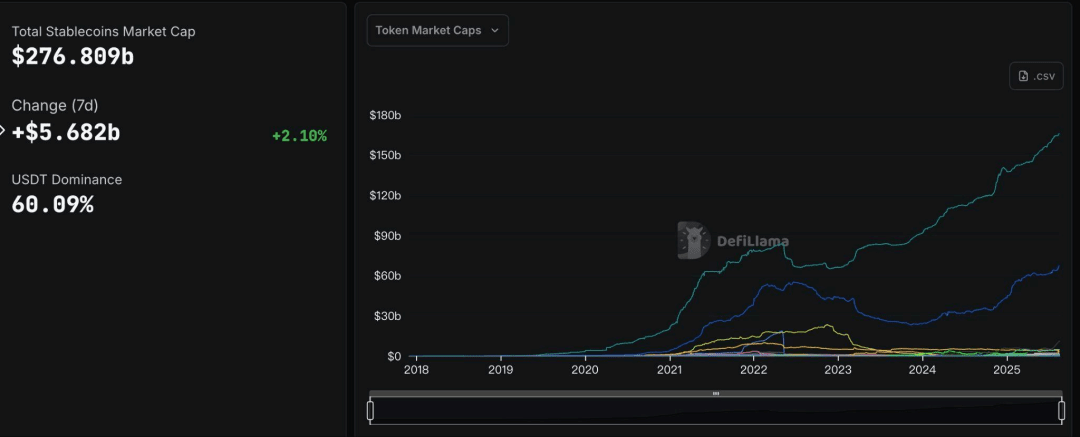 (Total stablecoin market capitalization, source: DeFiLlama)
(Total stablecoin market capitalization, source: DeFiLlama)
In terms of market share, USDT accounts for approximately 60.14%, USDC accounts for 24.56%, and USDe ranks third with 4.13%.
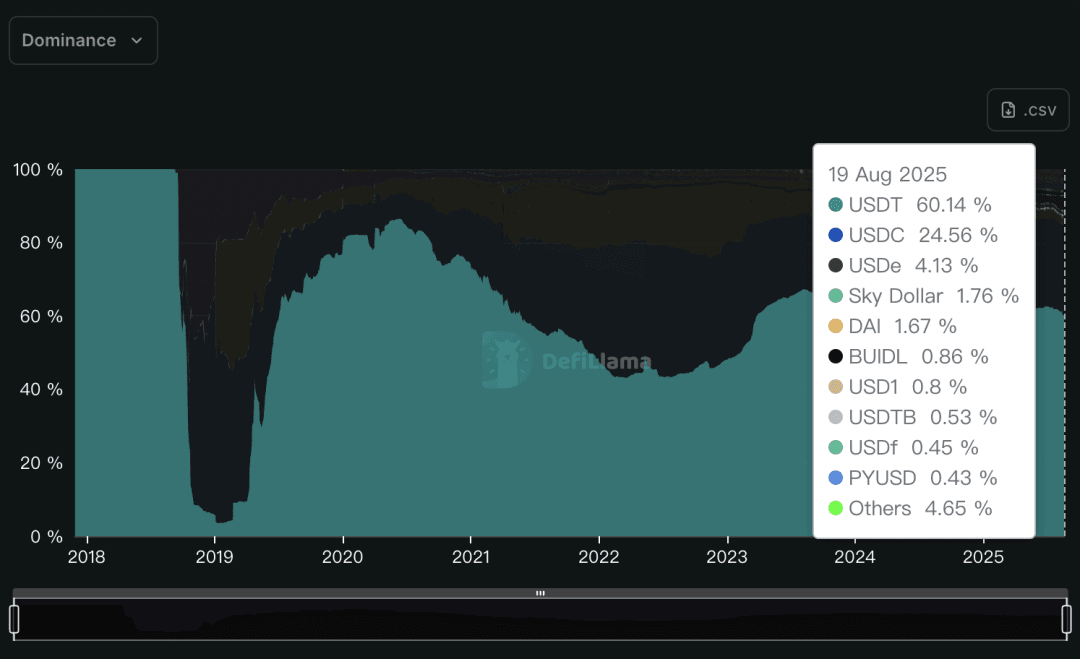 (Proportion of each stablecoin, source: DeFiLlama)
(Proportion of each stablecoin, source: DeFiLlama)
An examination of the top ten stablecoins by market capitalization reveals that fiat-collateralized stablecoins, including USDT, USDC, BUIDL, USD1, USDf, and PYUSD, still dominate. These stablecoins rely on traditional financial assets like fiat or government bonds as reserves, resulting in high compliance and market acceptance. Among decentralized crypto-collateralized stablecoins, only DAI has made it into the top ten. Meanwhile, some algorithmic or hybrid stablecoins are also emerging, such as USDe, which utilizes a synthetic dollar plus hedging model; USDS, which combines algorithms with partial collateralization; and USDTB, which continues the synthetic dollar plus hedging model. While the fiat-collateralized stablecoin market remains dominant, new technological paths and experimental mechanisms are constantly being explored.
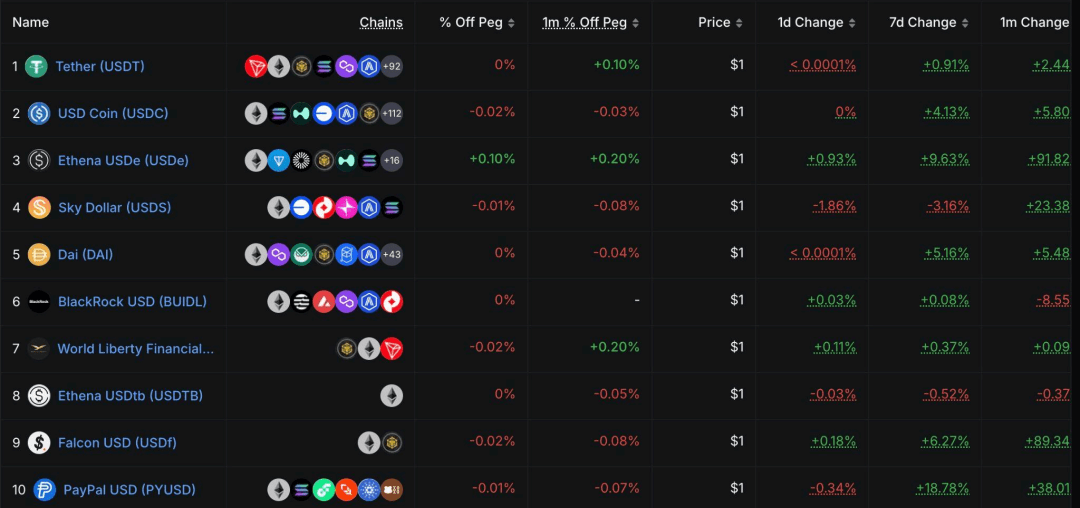 (Top 10 Stablecoins, Source: DeFiLlama)
(Top 10 Stablecoins, Source: DeFiLlama)
(4) Compliance and regulatory challenges brought by stablecoins
As the market scale expands, the AML compliance risks and regulatory requirements associated with stablecoins are gradually gaining attention. Different jurisdictions have varying regulatory approaches and approaches to stablecoins. These differences mean that stablecoins are both a driving force for financial innovation globally and a key target for cross-border regulatory coordination. It's important to note that the "stability" of stablecoins doesn't automatically reduce AML risks. On the contrary, in certain scenarios, their characteristics may increase the scope for exploitation by high-risk actors. For example, their high liquidity enables stablecoins like USDT and USDC to transfer large amounts of funds across borders in a short period of time. Their composability, through exchanges, cross-chain bridges, and aggregators, allows for rapid fund splitting and migration, increasing the complexity of on-chain tracking. Furthermore, the on-chain and off-chain exchange process can present challenges for monitoring. For example, in over-the-counter (OTC) transactions, stablecoins directly connect to cash or bank accounts, creating "breakpoints" that are difficult for on-chain data to cover. Therefore, relying solely on on-chain data is generally insufficient for AML risk control; it requires integrating data and identity elements from the off-chain financial system to achieve end-to-end tracking and monitoring.
Overall, stablecoins have played a crucial role in the global financial ecosystem, potentially boosting payment efficiency and financial innovation. However, they also introduce cross-border AML risks and technical challenges. To better understand the regulatory compliance challenges, this report first examines the different classifications and technical implementation paths for stablecoins.
2. Classification and technical implementation
The classification and implementation of stablecoins directly determine their performance characteristics in payment, settlement, and compliance monitoring, and also affect their traceability and risk level in anti-money laundering technology. The industry generally divides stablecoins into the following three main categories:
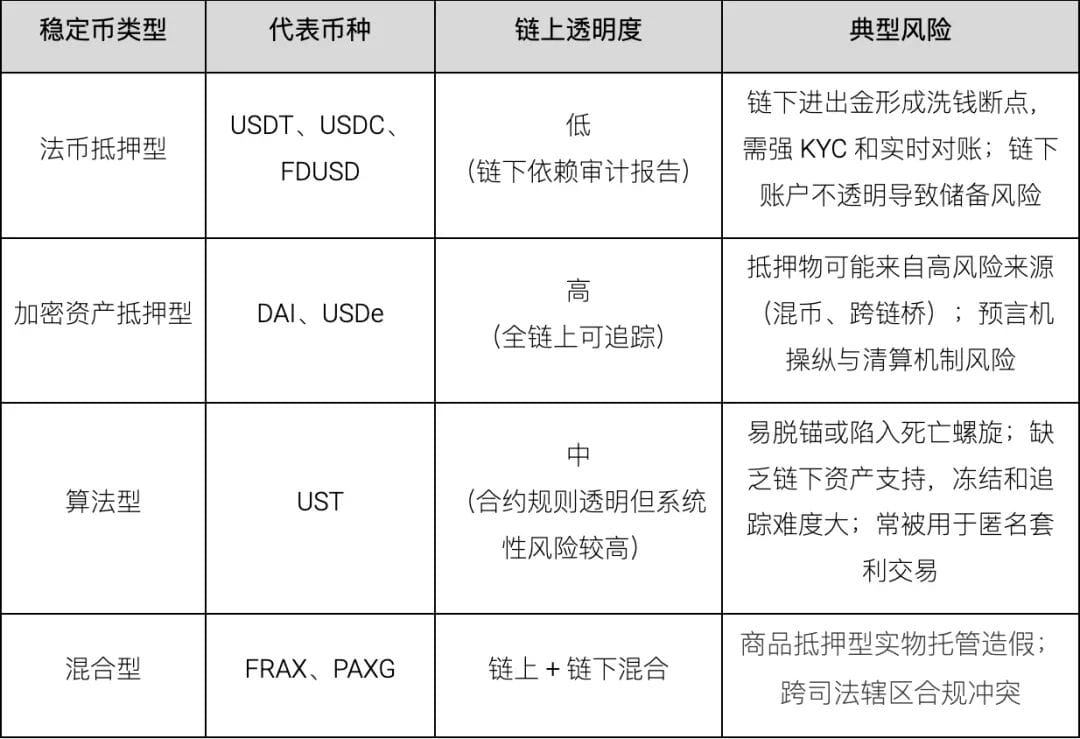 (1) Fiat currency collateral
(1) Fiat currency collateral
Representatives: USDT, USDC, FDUSD
Introduction: This type of stablecoin is created by the issuer, who deposits an equivalent amount of fiat currency in a bank or trust institution as a reserve. The issuance and redemption of this type of stablecoin are achieved on-chain through smart contracts, maintaining a 1:1 mapping relationship. Its advantages lie in its clear value anchor, high user trust, and strong compliance capabilities, making it the most mainstream form under the current regulatory framework.
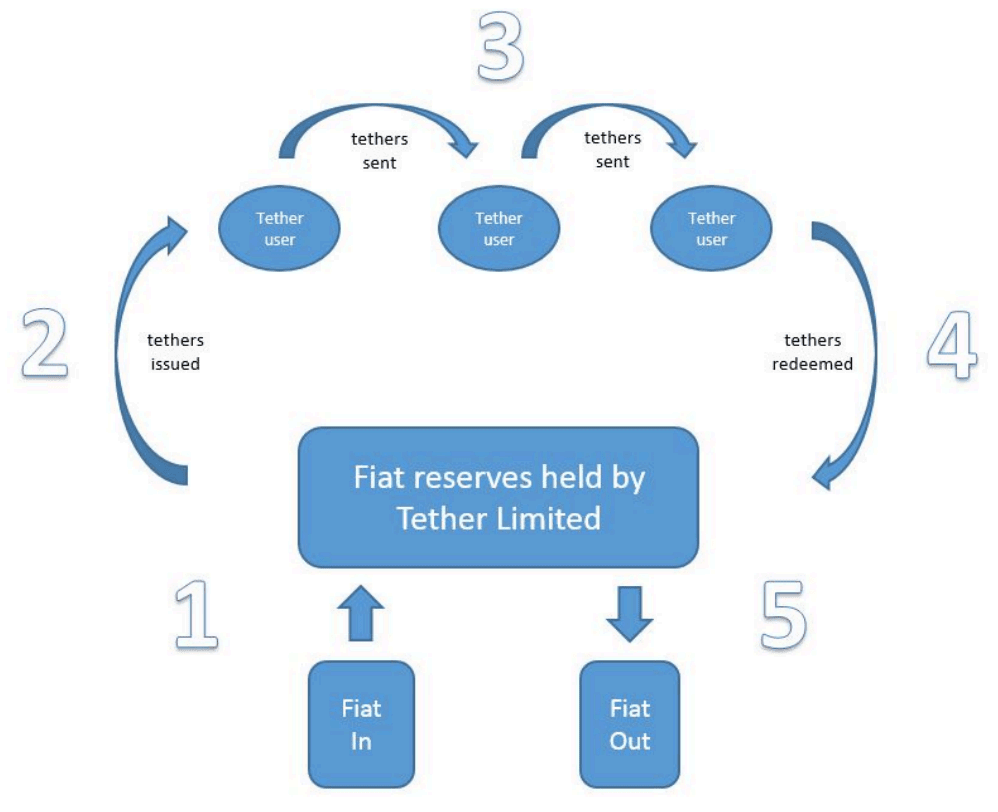 (Tether life cycle diagram, source: Tether official website)
(Tether life cycle diagram, source: Tether official website)
Taking USDT (issued by Tether) and USDC (issued by Circle) as examples, these stablecoins rely on centralized issuer management and have multiple compliance control functions built into their smart contracts, such as:
Freeze/Blacklist: The issuer can freeze tokens at a specific address to prevent on-chain transfers, in order to address sanctions or money laundering risks.
Burn: Tokens can be destroyed after freezing, usually to synchronize with fiat currency reserves or dispose of abnormal funds to maintain the consistency of the reserve chain;
Minting: Issuing new tokens to be redeemed with matching fiat currency, which must be accompanied by audits and reserve verification to maintain system transparency;
Unfreeze: After the compliance review is completed, the address's transfer capability can be restored. This type of operation is rare and is usually handled with caution.
These mechanisms provide fiat-collateralized stablecoins with practical on-chain compliance measures and a degree of flexibility in regulatory collaboration. However, this highly centralized control model has also created a tension between compliance and decentralization, a core topic of discussion within the industry.
(2) Crypto asset collateral
Representatives: DAI, USDe
Introduction: This model avoids reliance on centralized fiat currency custody by collateralizing crypto assets like ETH and BTC on-chain and setting an over-collateralization ratio. This model enhances decentralization, but also introduces risks of collateral price volatility and complex liquidation mechanisms. Its implementation relies on price data provided by oracles and automated liquidation logic. If the collateralization ratio falls below zero, the smart contract will force liquidation of the collateral to maintain the peg. From an AML perspective, this model offers the advantage of complete on-chain transparency of fund flows, but its disadvantage is that the legitimacy of the source of funds can be difficult to verify, especially when collateral may come from mixing services, cross-chain bridges, or other high-risk channels. Technical countermeasures include on-chain address clustering, behavioral pattern recognition, and labeling and filtering of high-risk inflow sources. Oracle security and contract audits must also be combined to prevent abnormal fund flows caused by vulnerabilities or price manipulation.
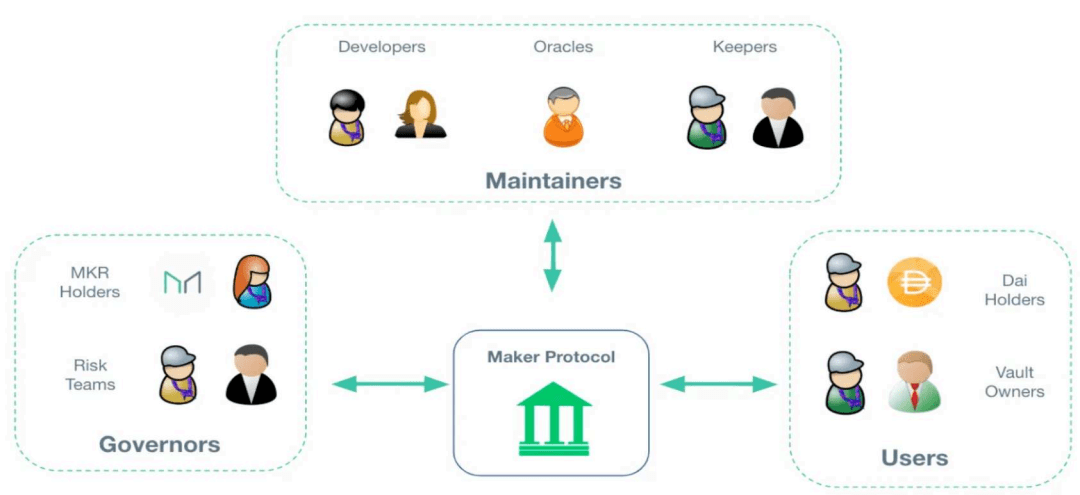 (Image of Maker Protocol participants, source: Maker official website)
(Image of Maker Protocol participants, source: Maker official website)
(3) Algorithm type
Representative: UST
Introduction: This model maintains price stability through token supply and demand adjustments, without relying on real-world asset collateral. It typically employs a dual-token model, with one token absorbing price fluctuations and the other serving as a stablecoin. Its technical core relies on regulating minting and burning through contract-encoded monetary rules, leveraging market arbitrage to maintain stability. However, under extreme market conditions, this model is prone to depegging and even "death spirals," as exemplified by the TerraUSD collapse in 2022. From an AML perspective, these stablecoins are often used for high-risk arbitrage and anonymous transactions due to their lack of physical backing and the difficulty of freezing and tracing them. Monitoring their fund flows requires greater reliance on transaction pattern analysis and machine learning models to identify anomalous behavior and potential money laundering pathways.
In addition to the three major models, other types of stablecoins have emerged in recent years. For example, partially collateralized stablecoins, such as FRAX (partial fiat currency reserves + partial algorithmic regulation), and commodity-collateralized stablecoins, such as PAXG (pegged to gold), require monitoring of physical assets under off-chain custody.
These classification differences not only impact the technical implementation of stablecoins but also determine the differences in their AML risk profiles: Fiat-collateralized stablecoins focus on KYC and auditing of off-chain accounts and minting processes, crypto-collateralized stablecoins rely on on-chain traceability and complex collateral mechanisms, and algorithmic stablecoins place higher demands on monitoring abnormal trading patterns and systemic risks. As stablecoin models continue to evolve, how to build a flexible and unified AML monitoring framework across different technical approaches has become a common challenge for global regulators and industry compliance teams.
3. Global AML Regulation
As different types of stablecoin models continue to evolve, how to constrain and guide them through regulatory frameworks has become a key issue. The following is a summary of the international and major jurisdictions regarding stablecoin regulation:
(1) FATF Travel Rule
At the international level, the Financial Action Task Force (FATF), the global anti-money laundering (AML) standard setter, has included stablecoins in its virtual asset regulatory framework. The FATF's Travel Rule requires virtual asset service providers (VASPs) to collect and share sender and receiver information in transactions to prevent money laundering and terrorist financing risks. The rule applies to transfers of virtual assets, including stablecoins, and emphasizes real-time information exchange to enhance transparency. As of June 2025, the FATF's targeted update report indicated that 99 jurisdictions had passed or were in the process of passing legislation implementing the Travel Rule, which aims to ensure transparency of cross-border payment information. Since the 2024 targeted update, the use of stablecoins by various illicit actors, including those from the Democratic People's Republic of Korea (DPRK), terrorist financiers, and drug traffickers, has continued to increase, with the majority of on-chain illicit activity now involving stablecoins. The large-scale adoption of stablecoins or virtual assets (VAs) could exacerbate illicit financing risks, particularly if implementation of the FATF standards for VAs/VASPs is uneven; the FATF plans to publish short reports on stablecoins, offshore VASPs, and DeFi between October 2025 and June 2026 to further support jurisdictional implementation, including strengthening supervision and risk management.
(2) Hong Kong, China
On August 1, 2025, the Stablecoin Ordinance officially came into effect, introducing a licensing system for stablecoin issuers. The Ordinance focuses on fiat-pegged stablecoins (FRSs), requiring issuers to obtain a license from the Hong Kong Monetary Authority (HKMA) and adhere to strict AML/CFT guidelines, including customer due diligence (CDD) and suspicious transaction reporting. Issuers must identify each stablecoin holder to prevent money laundering risks and maintain segregated and regularly audited reserve assets. The Ordinance prohibits the issuance of unlicensed stablecoins.
(3) United States
On July 17, 2025, the US Congress passed the GENIUS Act, marking the official implementation of the nation's first federal regulatory framework for stablecoins. The act restricts stablecoin issuance to "permitted stablecoin issuers" and requires them to comply with the Bank Secrecy Act (BSA) and FinCEN's AML rules, including the application of the Travel Rule. Issuers are required to implement Know Your Customer (KYC) procedures, monitor transactions, and report suspicious activity. Interest payments to stablecoin holders are also prohibited. FinCEN is responsible for developing specific AML rules for stablecoins to promote innovative approaches such as on-chain verification while ensuring the secure segregation of reserve assets. The framework aims to unify state and federal regulations and strengthen mitigation against money laundering risks.
(4) European Union
The stablecoin regulations in the Markets in Crypto-Assets Regulation (MiCA) will become fully applicable from June 30, 2024. The regulation classifies stablecoins as asset-backed tokens (ARTs) and electronic money tokens (EMTs), requiring issuers to obtain authorization from EU member state regulators and comply with EU AML regulations, including the implementation of the Travel Rule. Cryptoasset service providers (CASPs) must conduct customer due diligence, monitor transactions, and report suspicious activity, while ensuring the segregation and liquidity of reserve assets. MiCA integrates with the Anti-Money Laundering Regulation (AMLR) and the Transfer Funds Regulation (TFR), emphasizing cross-member consistency. It also sets a licensing application period for CASPs starting in January 2025 to mitigate money laundering risks associated with stablecoins.
(5) Singapore
The Monetary Authority of Singapore (MAS) released a regulatory framework for stablecoins in August 2023 and updated its AML/CFT guidelines in July 2025. This framework targets single-currency-pegged stablecoins (SCSs), requiring issuers to hold a MAS license and comply with AML requirements under the Payment Services Act (PSA), including customer due diligence, transaction monitoring, and the application of the travel rule. Stablecoins must be backed by low-risk, highly liquid reserve assets and ensure their value stability through regular audits. Only stablecoins that meet all requirements can be labeled "MAS-regulated stablecoins." MAS emphasizes strict scrutiny of algorithmically pegged or non-reserve-backed stablecoins to mitigate money laundering risks.
(6) Japan
Japan's Financial Services Agency (FSA) is regulating stablecoins through amendments to the Payment Services Act (PSA), which will take effect in 2023 and be further updated in 2025. Stablecoin issuance is limited to banks, trust companies, and money transfer operators, requiring compliance with strict AML/KYC rules, including customer identification and suspicious transaction reporting. In August 2025, Japan is preparing to launch its first yen-pegged stablecoin (JPYC), emphasizing domestic custody and segregation of reserve assets to prevent money laundering risks.
(7) South Korea
In 2024, the Virtual Asset User Protection Act officially came into effect, requiring virtual asset service providers (VASPs) to comply with AML regulations, including the travel rule and customer due diligence. The Financial Intelligence Unit (FIU) began restructuring AML protocols in August 2025 to strengthen stablecoin oversight and research global standards to prevent money laundering and terrorist financing risks. The Financial Supervisory Commission (FSC) plans to submit a bill to regulate won-pegged stablecoins to the National Assembly in October 2025. The bill will establish a legal framework for stablecoins for the first time, focusing on issuance rules, reserve management, and internal risk controls.
AML/CFT regulations for stablecoins are gradually tightening internationally and across major jurisdictions, presenting a landscape of "international framework guidance coupled with local variations in implementation." While the FATF provides overarching standards, regional differences persist in the progress and depth of implementation of the travel rule, reserve management, and cross-border information sharing. The resulting regulatory fragmentation and technological challenges necessitate a balance between ensuring innovation and mitigating risks. These regulatory requirements not only define the compliance boundaries for stablecoins but also provide a reference for subsequent technical approaches and practical exploration.
II. Risk Situation Analysis
1. Risk characteristics of stablecoins
Stablecoins were originally designed to provide a relatively stable value carrier for payments, clearing, and cross-border capital flows. However, from an AML perspective, the "stability" of stablecoins does not necessarily reduce risk. On the contrary, their high liquidity, cross-border convenience, and the combination of on-chain transparency and anonymity create new compliance challenges.
From a technical and financial perspective, stablecoins present risks related to their peg mechanisms and systemic vulnerabilities. Algorithmic stablecoins can fail completely in extreme circumstances. A case study with global repercussions is the collapse of TerraUSD (UST), which directly posed a death spiral for algorithmic stablecoins. UST maintained price stability through a dual-token model (linked to LUNA), but under market pressure, it decoupled from its peg, resulting in significant losses for investors. This incident highlighted the weaknesses of algorithmic stablecoins, which lack physical backing and are susceptible to market fluctuations, posing a challenge to their regulatory compliance.
Secondly, stablecoins offer both transparency and anonymity. On the one hand, on-chain transactions are traceable, providing an analytical data foundation for AML systems. On the other hand, without supporting off-chain KYC data, the phenomenon of "transparency without attribution" is highly likely to occur. In reality, stablecoin issuers have repeatedly frozen funds linked to criminal activity. For example, according to Cointelegraph, Tether blacklisted over $374,000 worth of stolen funds in November 2023, while three of the four major stablecoin issuers have blacklisted $3.4 million worth of funds from a cluster of addresses linked to Lazarus. This demonstrates that while the transparency of stablecoins facilitates AML monitoring, without identifying information, they can still be widely used for money laundering and terrorist financing.
Regarding the risks of illegal activities, stablecoins, due to their convenience and widespread acceptance, are frequently used for cross-border money laundering and illegal remittances. The North Korean Lazarus hacker group is a prime example of this threat. Active since 2009, the group had stolen over $3 billion in crypto assets by 2023. The fund flow reveals that stablecoins are a key component of their money laundering tools. Lazarus is adept at leveraging the TRON network and unregulated over-the-counter (OTC) channels to layer and anonymously transfer funds. Typical incidents include the $1.46 billion theft from Bybit. Meanwhile, recently exposed cases reveal how Southeast Asian fraud rings are exploiting Hong Kong's OTC channels for industrialized operations. Mainland university students were hired as "runners," taking orders on second-hand trading platforms. They then exchanged RMB transferred by others for Hong Kong dollars, purchased USDT, and transferred the funds to designated wallets. Later, they discovered that the funds were stolen from telecom fraud schemes, and their bank accounts were frozen by the police, unwittingly becoming "drivers" in the money laundering chain. On-chain tracking reveals that the USDT involved ultimately flowed into Southeast Asian guarantee platforms (such as Huiwang Guarantee and Xinbi Guarantee), which have long provided services for gambling, online fraud, and other illicit activities. Their core model is known as "card-for-USD," whereby illicit funds are collected through "cannons," quickly converted into cryptocurrency, and transferred through tiered channels, with commissions exceeding 30%. Investigations revealed that this money laundering network laundered over $310,000 in three months. Operated by a Southeast Asian organized crime group, it has formed a highly specialized, cross-border money laundering industry chain with a clear division of labor. This case highlights the vulnerability of Hong Kong's OTC channels to the stablecoin AML system and demonstrates that the traditional "cash-for-USD" model has evolved into a hybrid money laundering scheme that combines cross-border capital flows, online fraud, and rapid on-chain transfers.
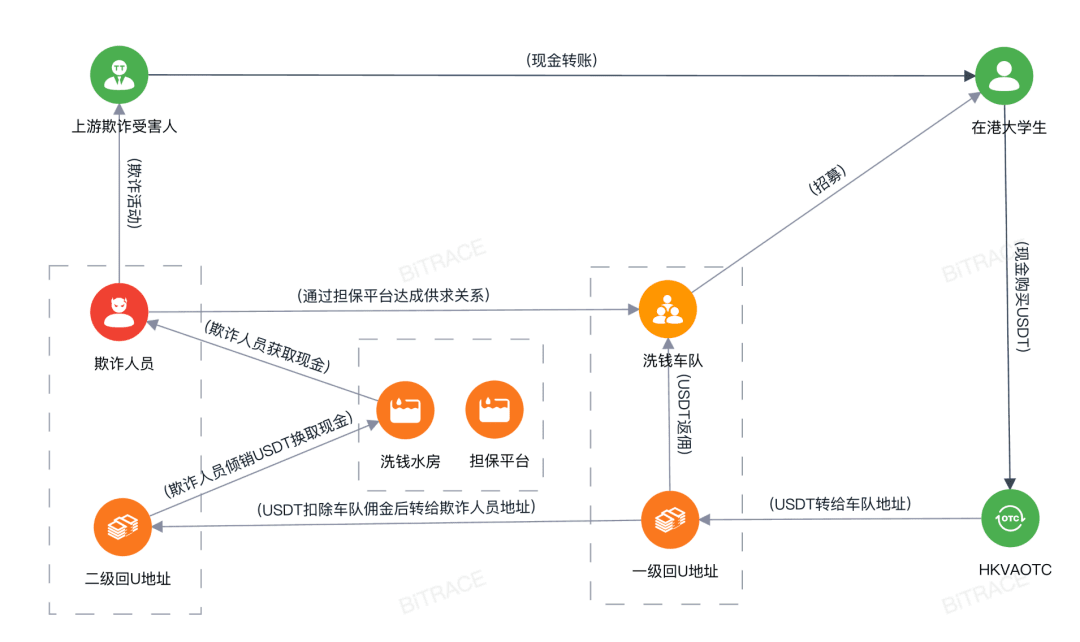 (Event flow chart, source: Bitrace)
(Event flow chart, source: Bitrace)
Similar risks are also on the rise in mainland China: Recent cases disclosed by judicial authorities in various regions reveal that virtual currencies, such as Tether (USDT), are becoming a core tool for cross-border "counter-trading" (illegal cross-border foreign exchange transactions). In one case, the amount involved in Yang's illegal foreign exchange transactions reached 6.5 billion RMB. Criminals used stablecoins and cross-border "counter-trading" to launder and transfer funds required for domestic and international exchange transactions. The inclusion of virtual currencies in traditional "counter-trading" transactions further enhances the secrecy of illegal foreign exchange transactions, increasing the scale of these high-value cross-border exchange cases.
While stablecoins are inherently neutral instruments, when integrated with infrastructure such as privacy protocols and exchanges, compliance risks often increase. For example, in 2022, the US OFAC added the Tornado Cash contract to its sanctions list. The sanctions statement stated that Tornado Cash had processed over $7 billion in cryptocurrency transactions since 2019. Although OFAC's sanctions directly targeted Tornado Cash's smart contract address, not the stablecoin itself, the move had an indirect impact on the stablecoin ecosystem. For example, following the sanctions, Circle (the issuer of USDC) froze approximately 75,000 USDC in addresses associated with Tornado Cash to comply with OFAC's sanctions requirements. Another case study is the Garantex exchange. In 2025, the US Department of Justice, in conjunction with German and Finnish law enforcement, cracked down on the cryptocurrency exchange Garantex, shutting down its online infrastructure for suspected money laundering for transnational criminal and terrorist organizations. Garantex is understood to have processed at least $96 billion in transactions since its inception, including services for the Lazarus Group, Russian oligarchs, and multiple ransomware gangs. Following an on-chain freeze executed by US law enforcement in collaboration with Tether, Garantex services were forcibly halted, freezing a significant amount of USDT in transit.
In terms of compliance and judicial practice, stablecoins also face challenges with cross-border differences and enforcement timelines. Inconsistent regulatory standards across countries and regions mean that the same stablecoin transaction may be deemed compliant in Country A but trigger AML risks in Country B. This fragmented regulation hinders efficient cross-border monitoring and law enforcement collaboration. Furthermore, the immediacy of stablecoin transfers often delays judicial freezes and cross-border enforcement, resulting in the unbundling and transfer of large amounts of suspicious funds before measures are implemented, significantly increasing the difficulty of recovering them.
Both historical and recent cases demonstrate that the risk characteristics of stablecoins stem not from a single factor but rather from a complex interplay of technology, markets, and institutions. They can trigger systemic capital outflows due to technical design flaws or market events, or they can become tools for cross-border money laundering through deliberate manipulation by high-risk entities. Therefore, an effective stablecoin AML system must combine on-chain transparency with off-chain compliance information, and establish a dynamic prevention and control mechanism covering the entire lifecycle.
2. Typical money laundering methods
(1) OTC foreign exchange transactions bypass KYC
Over-the-counter (OTC) currency swaps are a significant source of AML (anti-money laundering) risk for stablecoins. Through unregulated or underserved OTC platforms lacking rigorous KYC (know your customer) procedures, traders can convert fiat currencies into stablecoins, circumventing regulation and scrutiny to a certain extent. These transactions often involve large cross-border transfers of funds, making on-chain tracing more difficult. Funds from illicit and gray market actors often enter the OTC market in cash or illicit fiat currencies and are then directly exchanged for stablecoins like USDT and USDC. Due to the widespread lack of comprehensive KYC/AML procedures among OTC merchants, this process becomes a hidden channel for funds to enter the blockchain. On-chain monitoring can identify potentially risky funds by clustering fund flows and comparing them with high-risk OTC wallet tags.
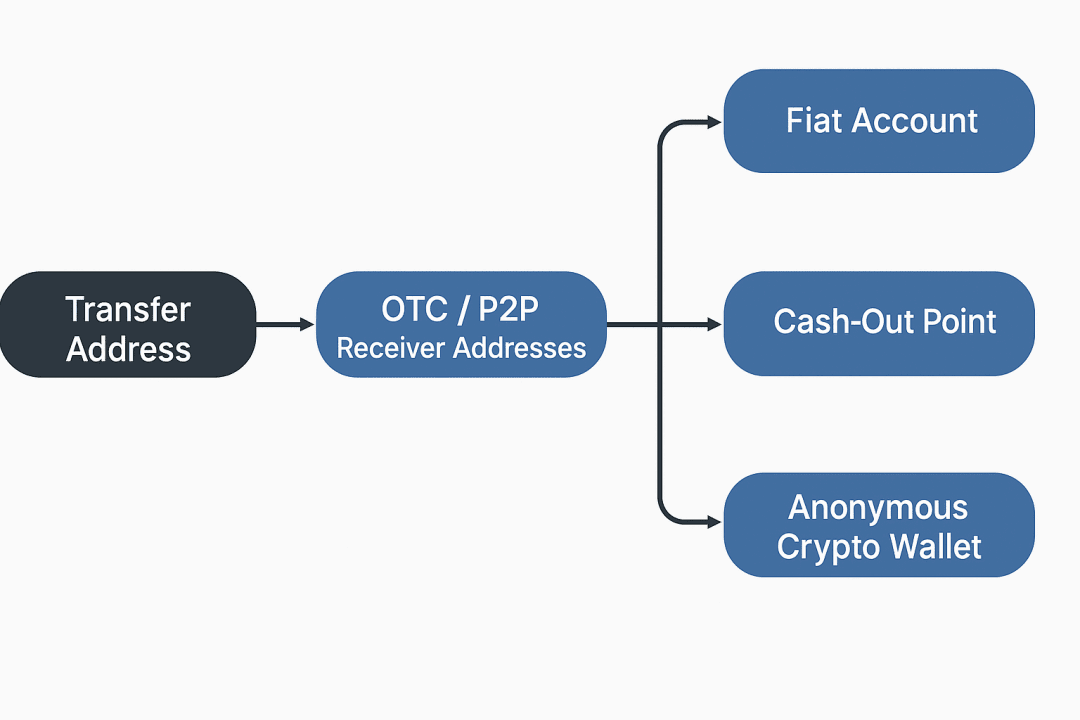 (2) On-chain splitting and stratification
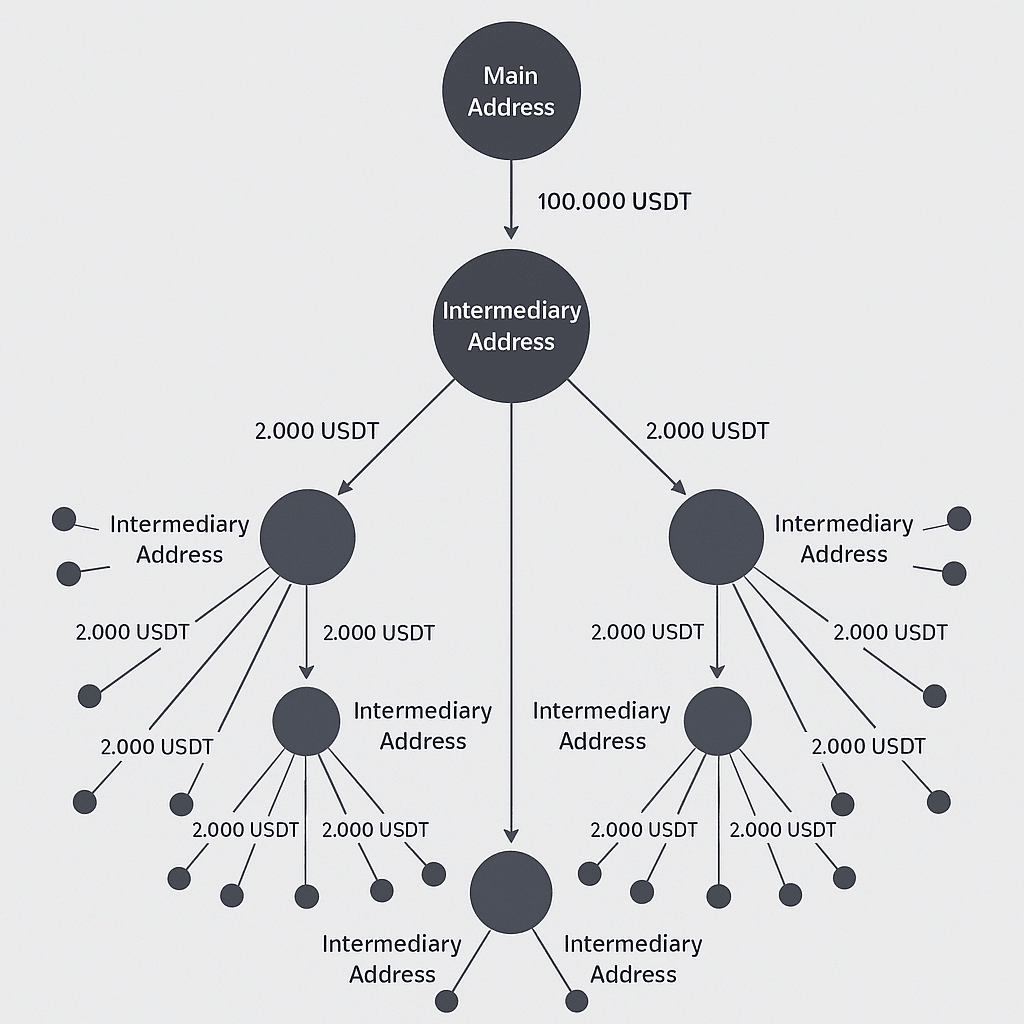
(2) On-chain splitting and stratification
After acquiring stablecoins, money launderers typically split large sums into multiple smaller transactions, distributing them across multiple newly generated addresses to conceal the source and size of the funds. These funds may then be redeemed through various decentralized exchanges (DEXs) or transferred across blockchains before being repatriated to the target account. Technically, potentially suspicious patterns can be identified by analyzing transaction network complexity, abnormal inflow/outflow ratios, and hop count statistics. Similar patterns often occur in hacker attacks or fund theft incidents. For example, stolen stablecoins are often split dozens of times on-chain in a short period of time, making them more difficult to freeze and track.
 (3) Cross-chain bridge + privacy tools
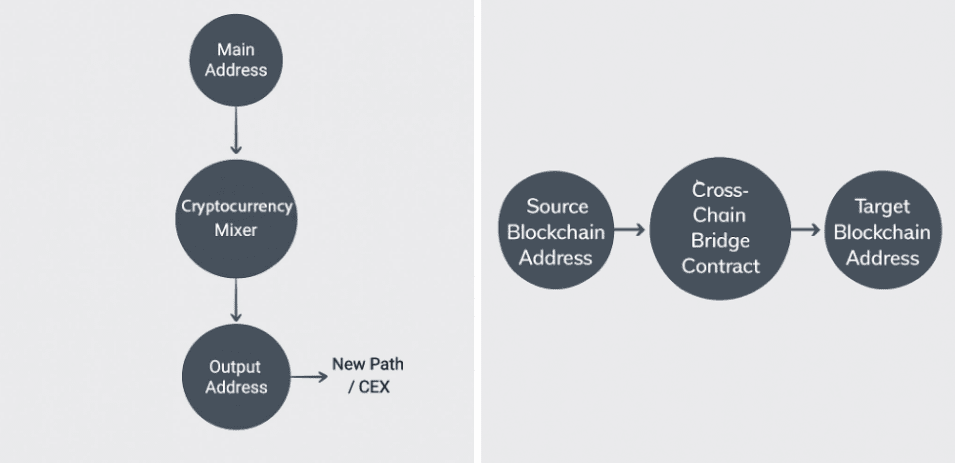
(3) Cross-chain bridge + privacy tools
Cross-chain bridges, combined with privacy tools, are another common money laundering route. Traders typically transfer stablecoins to different blockchains using a cross-chain bridge, then convert USDT/USDC into assets like ETH and BTC, ultimately using a mixing service like Tornado Cash to disrupt fund traceability. Graph network analysis and transaction pattern recognition can pinpoint potentially suspicious fund flows. After multiple splits and merges through mixing protocols and cross-chain bridges, funds may ultimately end up on centralized exchanges, creating complex fund paths and increasing the difficulty of AML tracking.
 (4) DeFi arbitrage and short-term withdrawals
(4) DeFi arbitrage and short-term withdrawals
Arbitrage and flash loans on DeFi platforms are also typical short-term money laundering methods. Users exploit price fluctuations or flash loans to conduct large stablecoin transactions within a short period of time, profiting from cross-protocol arbitrage and then withdrawing funds. These operations often involve multiple transactions nested within the same block or multiple blocks, generating a large amount of on-chain data in a short period of time, posing challenges for AML monitoring. In practice, law enforcement agencies can use on-chain analytical tools to track the flow of arbitrage funds and, combined with transaction anomaly detection, identify high-risk transactions and initiate freezing measures to recover funds.
(5) Nested account operations
Attackers control multiple accounts and execute circular transfers within the same exchange, splitting large sums of money into multiple small transactions. This creates a complex transaction network that can be difficult to identify with traditional AML screening. On-chain monitoring technology, combined with address risk tags, transaction amount distribution, and counterparty behavior analysis, can effectively identify such nested transactions and provide clues to potentially suspicious transactions.
3. Cross-border and judicial challenges
As the technological foundation for cross-border payments and clearing, stablecoins naturally transcend the national boundaries of the traditional banking system. This characteristic presents both an advantage in terms of compliance and a significant challenge for anti-money laundering. International cases have demonstrated that when funds flow across borders via stablecoins, their speed and anonymity often exceed the responsiveness of existing compliance systems, creating the dual challenges of both time and space in AML regulation.
(1) Judicial differences and difficulties in implementing the travel rule
Although the FATF proposed global standards for virtual assets and VASPs in 2019 and has repeatedly emphasized the AML risks of stablecoins since then, regional variations exist in their implementation. As mentioned in the "Global AML Regulation" section, these institutional differences can easily create regulatory vacuums when stablecoin funds cross multiple jurisdictions. For example, if a USDT transaction flows from a regulated region to a jurisdiction with weaker compliance requirements, relevant institutions will struggle to obtain complete identity information off-chain, creating an AML loophole. Only through cross-border collaboration and the simultaneous development of on-chain technologies can we disrupt the criminal capital chain.
From a technical perspective, implementing the Travel Rule requires message transmission protocols, encrypted communications, and cross-platform compatibility. While there are attempts within the industry to implement protocols like TRISA and IVMS101, global interoperability has yet to be achieved, resulting in a "half-compatible, half-island" problem. This prevents cross-border funds from being fully matched across different compliance systems. For example, when compliant entities interact with non-compliant parties, Travel Rule information may not be effectively transmitted or verified, thus weakening AML effectiveness.
(2) Cross-chain and multi-chain judicial breakpoints
Stablecoins can flow across multiple public chains, significantly increasing the complexity of AML. Some networks, due to their low transaction costs and high transaction speeds, are more susceptible to misuse of funds, and cross-chain tools further enhance this concealment. While cross-chain visualization and monitoring methods exist, these often rely on large-scale data access and computing power, making them virtually impossible for regulators in a single jurisdiction to implement independently. Therefore, effective cross-chain AML relies on international collaboration and third-party technology providers. The Hong Kong Monetary Authority has also stated that licensed stablecoin issuers need to collaborate with analytical firms with cross-chain tracing capabilities to strengthen their AML technical protections in multi-chain scenarios.
(3) Cross-border law enforcement collaboration and timeliness challenges
Even if on-chain fund paths can be traced, discrepancies in off-chain enforcement timelines can render AML ineffective. For example, if funds are transferred multiple times across multiple platforms and decentralized exchanges within a matter of hours, the funds may have already entered high-risk jurisdictions where freezing is difficult before law enforcement can complete a request for judicial cooperation. Historical cases have shown that jurisdictions that respond promptly are able to freeze some funds, while jurisdictions that lag behind may lose the opportunity to recover them entirely. The core of cross-border AML lies not only in the alignment of compliance systems but also in the real-time nature and collaborative nature of law enforcement.
The common feature of these challenges is that the traditional AML framework is built on a financial system with national boundaries, while the characteristics of stablecoins transcend national borders and links. The real difficulty lies in how to build a global real-time monitoring, cross-chain tracking and judicial mutual trust system, rather than just meeting local compliance requirements.
3. Path to Technical Compliance
1. Smart Contract Layer Compliance Mechanism
This section explores how stablecoin smart contracts can embed anti-money laundering (AML) and counter-terrorist financing (CFT) compliance requirements by extending existing token standards and promoting on-chain automated compliance processes to the extent feasible.
(1) Enhanced token standards and protocol layer support
Traditional token standards, such as ERC-20, lack native support for complex compliance requirements. Relying solely on off-chain solutions makes it difficult to audit and verify the compliance of every transaction. Therefore, this report recommends designing a new smart contract standard that extends ERC-20 with core modules, including Pausable (global pause), Freezable (account freezing), Whitelist (whitelist restriction), Blacklist (blacklist ban), and AccessControl (role-based access control). These modules emphasize operational security, controllable permissions, and risk traceability. It is recommended that these functional extensions be based on extensively audited standard libraries, such as OpenZeppelin, to maximize security.
(2) Core roles and role-based access control
To mitigate the risk of single points of failure and internal abuse, role-based access control (RBAC) can be introduced. Compared to a single "administrator" model, RBAC provides better separation of duties. A set of clear roles can be defined and assigned to different entities or employees controlled by a multi-signature wallet to minimize the risk of single points of failure or collusion. Each role should be limited to a specific function, and all actions require multi-signature authorization, ensuring that no single employee holds multiple high-risk roles simultaneously. All actions should be logged and subject to regular third-party audits, and permission assignments can be overseen by administrators or a board of directors.
In addition to roles such as MINTER_ROLE (responsible for minting), BURNER_ROLE (responsible for burning), PAUSER_ROLE (responsible for global suspension), RESUME_ROLE (responsible for recovery), FREEZER_ROLE (responsible for freezing specific accounts), WHITELISTER_ROLE (responsible for managing whitelists), BLACKLISTER_ROLE (responsible for managing blacklists), and UPGRADER_ROLE (responsible for contract upgrades), we recommend introducing a key new role, ATTESTER_ROLE. This role is granted to licensed VASPs or other trusted compliant entities to provide on-chain proof of the off-chain exchange of "transfer rules" information when transfers occur.
(3) Whitelist mechanism and customer due diligence
The whitelist model provides a high level of AML/CFT controls, enabling proactive prevention. It is a closed-loop, "default closed" model, meaning no address can hold or receive tokens unless it has been explicitly whitelisted after due diligence by the issuer.
Off-chain processes
Users first need to open an account with a licensed VASP (such as a licensed exchange or the stablecoin issuer itself);
The VASP performs comprehensive CDD on users in accordance with compliance requirements. This includes collecting and verifying the user’s identification documents, proof of address, and understanding their account opening purpose and source of funds.
On-chain execution
After approval by the compliance team, an authorized operator can call the smart contract's whitelistAdd(address attester, address account) function through a multi-signature wallet holding the WHITELISTER_ROLE role;
The smart contract executes this function, sets the value of isWhitelisted[_account] to true, and records the address of the caller (i.e., the VASP) in the attesterOf[_account] mapping. This creates an important attribution, indicating which VASP introduced the user to the system.
It also supports the whitelistRemoved(address _account) function to remove an address from the whitelist.
(4) Transfer rule assertion mechanism
In order to comply with the requirements of the “transfer rules”, that is, the information of both parties to the transfer must be recorded and transmitted, it is recommended to introduce an on-chain assertion mechanism.
Off-chain processes
When user A (with VASP-1) wishes to transfer funds to user B (with VASP-2), VASP-1 and VASP-2 can securely exchange user A and B’s identity information (name, address, etc.) off-chain.
If VASP-2 passes the verification and risk assessment, it sends a confirmation receipt to VASP-1. At this point, both parties have reached an agreement on the information exchanged regarding the "transfer rules";
The VASP-1 and VASP-2 systems then independently calculate a unique hash value for the agreed-upon data package (including both parties' user information) using the same algorithm. This hash value is known as the travelRuleHash. Because the input data and algorithm are identical, the hash values calculated by both parties must also be identical.
On-chain proof
Before executing the on-chain transfer, the initiator, VASP-1 (i.e., User A's organization), uses its multi-signature wallet holding the ATTESTER_ROLE role to call the smart contract's submitTravelRule function, submitting the travelRuleHash calculated off-chain. The contract then queries the attesterOf[_from] mapping to verify that the caller is User A's official "authenticator." If verified, the contract creates a record in the travelRuleAttestations mapping.
Receiver VASP-2 (i.e., User B's institution) also calls the confirmTravelRule function through its ATTESTER_ROLE multisig wallet to confirm the customer transfer information submitted by initiator VASP-1. This proves on-chain that both licensed institutions have reached an agreement and jointly endorsed the "transfer rule" requirements for a specific transaction.
After both VASPs have completed the on-chain assertion, the system now allows the actual token transfer to be executed. This is typically done by the initiator, User A (or VASP-1 acting on User A’s behalf), calling the smart contract’s transfer or transferFrom function.
To this end, the following data structures and events can be defined in the smart contract:
Transfer status enumeration: enum TravelRuleStatus{None, Submitted, Confirmed, Transferred};
Travel Rule hash and necessary transfer status information structure: struct TravelRuleData, including originatorVASP, beneficiaryVASP, travelRuleHash, from, to, amount, expiry, and status;
Mapping: isWhitelisted (stores the user's whitelist status), attesterOf (stores which attester the user is authenticated by), travelRuleAttestations (stores the Travel Rule hash and necessary transfer status information);
事件:WhitelistAdd、WhitelistRemoved、SubmitTravelRule、ConfirmTravelRule、TransferTravelRule。
(5) Compliance expansion of core token operations
To support compliance requirements, it is recommended that stablecoin smart contracts expand on the basic ERC-20 functions and integrate a series of core management functions.
Coinage mechanism
Issuance should be “prudent and robust”, with minting “matched with a corresponding increase in the relevant reserve asset pool”, and issuers can issue to their customers after receiving funds and valid issuance requests;
The smart contract itself does not need to enforce the "full reserve" requirement, but the right to mint coins is a key control point. The on-chain minting function can be designed to be callable only by a trusted entity (i.e., the issuer itself) that can verify that the off-chain conditions have been met.
Pre-check: Before executing the minting function, the function should check whether the target address to is in the blacklist or frozen state;
Operational process: The customer completes all required off-chain KYC and CDD processes; the customer transfers the equivalent amount of fiat currency funds to the issuer's designated bank account; the issuer's internal system confirms receipt of the funds and updates the reserve asset record; the operations team creates and signs a multi-signature transaction, calls the smart contract's token minting function, and sends the newly minted stablecoins to the customer's pre-registered and verified wallet address.
Redemption/destruction mechanism
The issuer may process a valid redemption request as soon as practicable after receiving it. The withdrawal of reserve assets may be matched by a corresponding reduction in the nominal value of the designated stablecoin in circulation;
Redemption is a two-step process involving both on-chain and off-chain interactions. To avoid the risk of fiat currency transfer failure, token destruction should be performed after fiat currency settlement is confirmed.
Redemption Preparation: Users first need to transfer the tokens to be redeemed to a designated address controlled by the issuer;
Operational process: The user submits an off-chain redemption request through the platform and performs CDD; the issuer system verifies the validity of the request and checks the on-chain token transfer; the issuer transfers the equivalent fiat currency to the user's pre-registered bank account; after confirming the success of the fiat currency transfer, the multi-signature wallet holding the BURNER_ROLE calls the burn function.
Emergency Control: Pause and Freeze
The contract can support operations such as pause, resume, blacklist, remove blacklist, freeze, and unfreeze, which are key components of the event management framework;
Pause: A global "kill switch" designed to immediately halt core contract functions (transfers, minting, and burning). This is called by a multi-signature wallet holding the PAUSER_ROLE. This is typically triggered when an abnormal event is detected (e.g., contract exploitation, reserve asset mismatch). Resume functionality is handled by a separate RESUME_ROLE.
Freeze: An account-level restriction that prevents a specific address from sending or receiving tokens, without affecting the normal activity of other addresses in the network. This restriction is invoked by a multisig wallet holding the FREEZER_ROLE and is triggered by suspicious activity (such as an AML alert or court order).
Address screening and blacklist mechanism
Issuers can take measures such as “blacklisting wallet addresses identified as sanctioned or associated with illegal activity.” This can serve as an on-chain enforcement mechanism, as off-chain warnings alone are insufficient.
Function implementation: This function implements the blacklist addition and removal functions, and is only called by the multi-signature wallet holding the BLACKLISTER_ROLE;
Transfer restrictions: blacklisted addresses are prohibited from transferring/receiving tokens;
Operational process: The analysis tool issues an alert, triggering an internal compliance review. After the compliance team reviews and confirms, the BLACKLISTER_ROLE multi-signature wallet initiates a blacklist addition transaction.
Upgradability of smart contracts
All smart contract architectures related to stablecoins may adopt “upgradeability.” This allows issuers to update logic without disrupting the existing contract state to address bug fixes, feature expansions, or regulatory changes.
Proxy model: For EVM-type smart contracts, the mature ERC-1967 proxy model can be adopted to achieve upgradeability;
Permission control: The upgrade function can only be called by a multi-signature wallet holding UPGRADER_ROLE;
Change Management Process: Before any upgrade is proposed, a rigorous change management process is completed, which includes a comprehensive, independent, third-party security audit of the new logic contract.
On-chain event log for analysis and reporting
Issuers can establish robust “information and accounting systems” to “record all business activities, including both on-chain and off-chain information, in a timely and accurate manner” and “maintain appropriate audit trails”;
Smart contracts can emit detailed events for every significant state change, allowing off-chain systems to log, monitor, and generate reports. These events create an immutable and permanent log on the blockchain, serving as the primary data source for all off-chain monitoring, accounting, and reporting systems.
In addition to the Transfer and Approval events required by the ERC-20 standard, contracts can define and emit custom events for all management actions and state changes: token minting/burning (Minted/Burned) events, contract pause/resume (Paused/Resume) events, blacklist addition/removal (BlacklistAdded/BlacklistRemoved) events, whitelist addition/removal (WhitelistAdded/WhitelistRemoved) events, address freezing/unfreezing (AddressFrozen/AddressUnfrozen) events, privileged role change (RoleGranted/RoleRevoked) events, and contract upgrade (Upgraded) events.
(6) Key management and deployment and operation security
It is recommended that traditional finance-level security posture be applied to crypto-native operations. Implementing this level of key management should be a core operational part of any issuer.
Key generation: This can be done through a well-documented "key ceremony" in a physically secure, air-gapped environment that is completely isolated from the outside world.
Key Storage: All administrative roles can be controlled by a multi-signature wallet. The private keys used by the signers of these multi-signature wallets can be stored in an HSM (Hardware Security Module) or other secure hardware wallet. For the most critical roles, their corresponding keys are preferably stored in an air-gapped system, physically isolated from any online environment.
Key usage: Multi-signature policies can be enforced. For transactions involving "important private keys", the signature of the relevant personnel may need to be present in person;
Backup and Recovery: Backups of key shards or mnemonics can be stored in secure and geographically dispersed locations in a tamper-resistant packaging.
Deployment processes and runtime monitoring can serve as an extension of the technical risk management framework, emphasizing preventing vulnerabilities at their source and continuously monitoring operational risks. For example, before formal deployment, a "pre-deployment checklist" can be developed and executed: comprehensive testing (over 95% coverage), independent audits (by at least one, and preferably two, reputable auditing firms), code freeze (freeze code after the audit until it goes live), regression testing, compliance sign-offs, deployment drills, and authorized deployment. Post-deployment, appropriate monitoring measures can be implemented to promptly mitigate the use of privileged roles and emerging threats: on-chain activity monitoring (for example, using the SlowMist security monitoring system MistEye to add key role activity monitoring) and threat intelligence monitoring (for example, using the SlowMist security monitoring system MistEye's threat intelligence subscription).
(7) Exit mechanism
The stablecoin smart contract needs to consider its own "retirement" process from the beginning of its design. It needs to have states and mechanisms that can achieve orderly shutdown:
Develop a business exit plan: This plan should cover various scenarios that could lead to an orderly termination and include measures to monitor the actual or potential occurrence of these scenarios;
On-chain exit process: Smart contracts can be paused to stop all token transfers to maximize reserve asset liquidation returns and minimize the impact on overall market stability; relying on redemption and whitelist functions, stablecoin holders are assisted in submitting redemption applications.
2. On-chain transaction pattern recognition
Within the stablecoin anti-money laundering (AML) technology ecosystem, on-chain transaction pattern recognition is a fundamental and core capability. Stablecoin transactions are essentially verifiable updates to the blockchain ledger state, providing a transparent data foundation for AML technology. This allows for the extraction and analysis of fund flow characteristics to identify potentially high-risk activities. Global practice demonstrates that on-chain pattern recognition, through multi-dimensional data analysis, can not only identify anomalous fund flows but also provide law enforcement with actionable risk signals, thereby improving monitoring efficiency in cross-chain and cross-border scenarios.
From a technical perspective, on-chain transaction pattern recognition mainly relies on the following levels:
(1) Address clustering and behavioral profiling
Attackers typically don't just use a single address. A common method is behavioral clustering analysis, which involves aggregating addresses controlled by the same person or entity. For example, if an address is frequently active in the early morning hours, uses a specific trading platform, almost exclusively trades a certain stablecoin, and consistently uses the same cross-chain funds path, this pattern creates a relatively unique "on-chain fingerprint." If multiple addresses exhibit similar operating habits, interaction objects, and transaction rhythms, this can help establish an "on-chain fingerprint" and identify the actor:
Input characteristics: In a transaction, if multiple addresses jointly input assets (such as multiple inputs in the BTC UTXO model), it is often assumed that these addresses are controlled by the same entity;
Behavioral characteristics: Multiple addresses receiving funds from the same source address within a short period of time and performing behavioral responses within a similar timeframe (e.g., cross-chain, DEX transactions) may be controlled by the same operator.
Service characteristics: If multiple addresses call a specific contract (such as a Ponzi scheme platform or a black market token contract) and their behavior paths are highly similar, they can be considered a behavior cluster.
Transaction parameter characteristics: The gas limits, transaction slippage, and fee preferences set by some attacker addresses during transfers are repetitive and can be used as supplementary clustering features.
Address structure characteristics: Some groups create addresses with naming patterns. For example, Gonjeshke Darande, the hacker group claiming responsibility for the Nobitex attack, used multiple addresses with emotional and provocative words in the incident, such as TKFuckiRGCTerroristsNoBiTEXy2r7mNX, 0xffFFffFFFFFFFfFFFFFFFFFFFFFFFFFFFFFFDead, and 1FuckiRGCTerroristsNoBiTEXXXaAovLX.
(2) Transaction pattern feature extraction
Laundered funds often exhibit specific behavioral fingerprints on-chain, such as frequent small-amount splits, multi-hop transfers to newly generated addresses, concentrated flows into anonymizing services, or frequent exchanges on decentralized exchanges. By combining transaction graph structures with time series, it's possible to identify fund distribution hubs and unusual transfer behavior. For example, graph algorithms can be used to discover fund distribution nodes, while time-window-based frequency anomaly analysis can identify split transaction patterns. If a system possesses on-chain pattern recognition capabilities, timely flagging or intervention measures can be triggered.
(3) Suspicious patterns and law enforcement collaboration
The goal of on-chain transaction pattern recognition is to transform transparent ledgers into interpretable risk signals and support global compliance reporting and law enforcement collaboration. For example, when the system detects a group of stablecoin addresses exhibiting a typical "splitting + mixing + cross-chain" pattern, it can automatically generate a suspicious transaction report (STR) and submit it to the relevant financial intelligence unit. In SlowMist's practical experience, pattern recognition and law enforcement collaboration often require a "signal priority" mechanism. This means that even without complete confirmation of fund ownership, suspicious address groups are quickly identified through pattern characteristics, marked on-chain, and blocked at a point where freezing is possible, buying time for subsequent investigations.
3. Address risk management and blacklist system
In the anti-money laundering (AML) architecture of stablecoins, address risk management and blacklist systems often serve as a "firewall layer." They serve as a crucial means of blocking on-chain activities by known high-risk entities and provide the operational foundation for real-time monitoring, automated early warnings, and law enforcement responses. However, in real-world applications, their effectiveness often depends on data quality, update speed, and the degree of cross-institutional collaboration, making them unlikely to constitute a complete defense on their own.
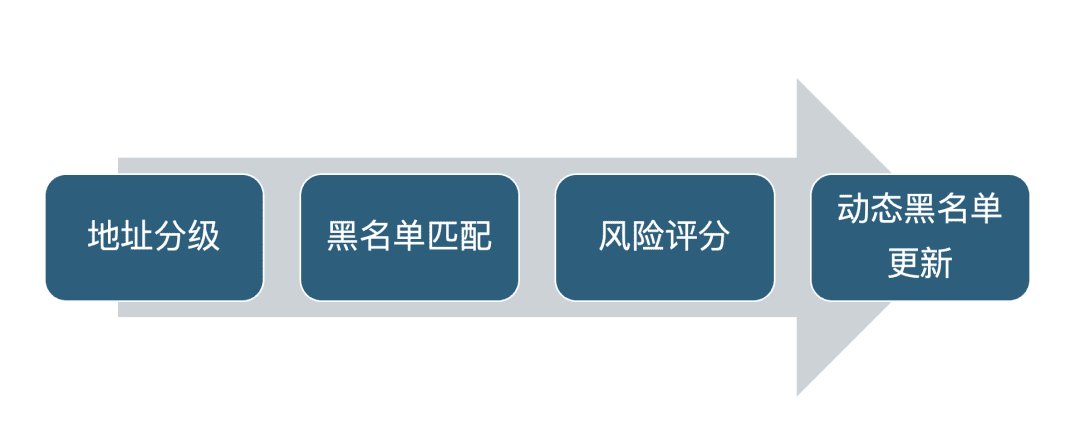
(1) The core logic of address risk management
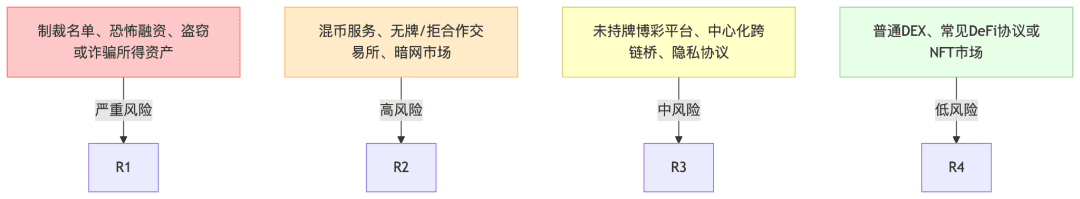
The key to address risk management lies in grading and dynamically profiling on-chain addresses so that differentiated controls can be implemented for different risk levels. Common stratification includes:
Serious risks: sanctions lists, terrorist financing, assets obtained through theft or fraud;
High risk: coin mixing services, unlicensed exchanges or those refusing to cooperate with law enforcement, darknet markets, etc.
Medium risk: unlicensed gambling platforms, centralized cross-chain bridges, privacy protocols, etc.
Low risk: regular DEX, common DeFi protocols, or NFT markets.
 This grading approach allows the AML system to tailor its rules to specific needs. For example, high-risk addresses may trigger a freeze or manual review, while medium-risk addresses may be placed under monitoring and observation. It's important to note that the grading standards are subject to adjustment based on institutional compliance requirements and jurisdictional differences and are not set in stone.
This grading approach allows the AML system to tailor its rules to specific needs. For example, high-risk addresses may trigger a freeze or manual review, while medium-risk addresses may be placed under monitoring and observation. It's important to note that the grading standards are subject to adjustment based on institutional compliance requirements and jurisdictional differences and are not set in stone.
(2) Technical implementation of the blacklist system
Traditional AML systems often rely on external sanctions lists (such as the OFAC sanctions list). However, in the blockchain scenario, this needs to be expanded to a dynamic on-chain blacklist. The core requirements include:
Real-time: When hacking incidents occur or international law enforcement agencies publish new risk addresses, the system can update the blacklist in a relatively short period of time.
Auditability: Blacklist updates and interception records need to be recorded on or off-chain to facilitate compliance and law enforcement tracing;
Interface and cross-institutional collaboration: Connect with external risk control providers or international databases through APIs to achieve cross-border data synchronization.
Blacklist systems are not just technical tools; they also carry institutional and compliance responsibilities. If licensed institutions fail to update their lists promptly, allowing funds to flow into high-risk entities could pose significant compliance risks. Therefore, blacklists must balance legal enforcement with automated protection capabilities.
 (3) Address labeling and risk intelligence sharing
(3) Address labeling and risk intelligence sharing
In practice, blacklisting is often supplemented by address labeling. Through on-chain behavioral analysis, fund flows, and open-source intelligence (OSINT) data, addresses can be associated with specific entities or behavioral patterns, such as "exchange deposit addresses," "fraud cluster wallets," "DeFi liquidity pools," or "ENS domain name holders." This allows for multi-dimensional identification of exchanges, wallet applications (such as MetaMask and imToken), and major DeFi users, helping compliance officers intuitively identify fund attributes. High-quality labeling is particularly important in scenarios where hacker funds are rapidly dispersed, significantly reducing response times. However, labeling carries the risk of being incomplete or outdated, necessitating integration with industry intelligence sharing networks.
(4) Dynamic blacklist and risk scoring model
Although fixed blacklists can cover known risks, they may lag behind in the face of new money laundering methods. Technically, a dynamic risk scoring model can be used to calculate a real-time updated risk score for each address. The score integrates the following key factors:
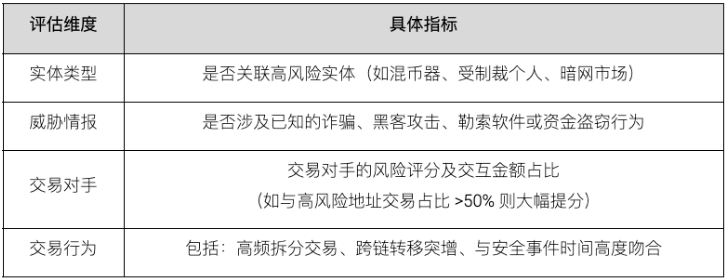 When the score exceeds a preset threshold, the system automatically places it on a "temporary blacklist," which can then be transferred to a "permanent blacklist" after manual review or law enforcement confirmation. This allows for a gradual transition from "passive blocking" to "active early warning," but its effectiveness depends on the quality of model training and intelligence coverage.
When the score exceeds a preset threshold, the system automatically places it on a "temporary blacklist," which can then be transferred to a "permanent blacklist" after manual review or law enforcement confirmation. This allows for a gradual transition from "passive blocking" to "active early warning," but its effectiveness depends on the quality of model training and intelligence coverage.
(5) Interface between compliance and law enforcement collaboration
An efficient blacklist system also requires global connectivity. This system requires a regulatory API interface. In cross-border AML collaboration, connecting with overseas VASPs through standardized protocols can form a distributed "address risk network" for global risk sharing and joint prevention and control. For example, in combating cross-chain money laundering or large-scale hacker groups like Lazarus, collaborative updates of blacklists and risk databases are crucial. However, cross-border information exchange is still subject to jurisdictional restrictions and data privacy compliance requirements, making implementation challenging.
(6) Response to “white to black”
In their anti-money laundering efforts, VASPs and stablecoin issuers often encounter the risk of addresses or tokens changing from “white” (low risk) to “black” (high risk). This is because regulatory policies and sanctions lists are constantly updated and evolving, causing the risk of transactions and tokens that have historically passed anti-money laundering screening to change.
While regulators generally "don't question the past," this doesn't equate to immunity. Most jurisdictions (such as the US OFAC and EU sanctions laws) require that once an entity is designated as a sanctioned entity, its downstream capital flows are subject to review. Even if a past blacklist is updated, historical transactions may be traced and identified as risky. This principle also applies to the cryptocurrency sector, as evidenced by historical sanctions from OFAC and other organizations.
The challenges of white-to-black transition mainly exist in the following two scenarios:
Scenario 1: New sanctions or intelligence release
For example, the U.S. Treasury Department's Financial Crimes Enforcement Network (FinCEN) announced sanctions against Huione Group on May 1, 2025. FinCEN alleged that Huione Group laundered over $4 billion in illicit funds between 2021 and 2025. Prior to FinCEN's sanctions, VASPs and stablecoin issuers (such as Tether) likely only knew that Huione Group's Huione Guarantee and Huione Pay businesses had deficiencies in their Know Your Customer (KYC) and Anti-Money Laundering (AML) implementation, placing some funds at risk, but not freezing all funds from Huione Group. Following FinCEN's sanctions against Huione Group, VASPs worldwide were required to re-evaluate their platform's historical deposits and withdrawals for AML purposes, identifying high-risk funds, restricting high-risk user accounts, or requiring users to provide additional KYC verification to clear any suspicion of contamination.
On the other hand, when global law enforcement agencies investigate cryptocurrency-related illegal activities, information is confidential and non-public. For VASPs and stablecoin issuers, only upon receiving freeze requests from law enforcement agencies can they identify certain deposit transactions on their platforms as suspected and high-risk. This can also lead to whitelists becoming blacklisted, and low-risk transactions becoming high-risk. For example, in an investment scam, victims withdraw funds from their exchanges to a standard address A (controlled by the scammers). Address A then continues to transfer funds, passing through multiple hops, to a VASP. This chain of events involves no token authorization or smart contract interaction; it's simply a standard transfer. Typically, the addresses on the chain are new and have no interaction with sanctions data. In this case, anti-money laundering software typically identifies this as low-risk. Only after gathering intelligence data from victims confirming that address A is a fraudulent address can they realize that the funds entering this VASP are illicit.
Scenario 2: The nature of the underlying assets or the project itself has fundamentally changed
For example, in 2022, the UST/LUNA on-chain algorithmic stablecoin model collapsed, and the FTX (and its platform token FTT) centralized exchange self-financing scam collapsed. The tokens involved, UST, LUNA, and FTT, were under a lack of oversight at the time, operating on the fringes of the law. Regulators in various countries only took action after the collapse, classifying the tokens as illegal securities and investment scams. Law enforcement agencies arrested those responsible, but remedying user losses (especially for users located in multiple countries and regions) proved challenging and progress was limited.
For example, some privacy coins, such as Monero (XMR), have been ordered offline by regulators (e.g., FATF/FinCEN). Because they cannot identify the source of funds or beneficiaries, they cannot comply with transaction traceability (a core requirement of anti-money laundering), and their transaction records are unreadable to regulators and law enforcement agencies. In other words, privacy coins violate the regulatory bottom line of "transparent finance" and "KYC/AML auditability."
This report combines industry practices and proposes the following response strategies:
Proactive Identification and Monitoring: We extensively collect data on cryptocurrency adoption globally, particularly in the Asia-Pacific region, to proactively identify and monitor high-risk money laundering services like Huione Group, as well as tokens identified by innovative or historical risk models. Before regulatory authorities take notice and issue sanctions, we leverage anti-money laundering software to configure risk rules for potential high-risk money laundering services, raising the bar and preventing potential high-risk funds from entering VASPs.
Establish broad intelligence cooperation alliances, such as the CDA Alliance, of which the SlowMist AML team is a member, and the InMist Threat Intelligence Cooperation Network, which it spearheaded. Through cross-regional, cross-institutional, and public-private sector data exchange and cooperation mechanisms, we can share intelligence data (such as hacker addresses and security vulnerabilities) immediately after a hacking incident occurs, collaborate with alliance members to monitor and intercept stolen funds, and assist alliance members in self-assessment to determine if they face the same risks.
Establish a community feedback mechanism: Leveraging security agencies, law firms, industry associations, and other organizations, we will collect information on incidents of fraud, theft, extortion, and pyramid schemes encountered by the community and the public. After verification and validation by authoritative organizations, we will extract wallet addresses where illegal funds are flowing, publicly mark them in the community and online, and dynamically monitor the whereabouts of illegal funds. This intelligence data and investigative reports will be simultaneously transmitted to law enforcement agencies to prevent the liquidation of illegal funds.
General strategic recommendations for dealing with the "day-to-night" scenario:
For VASPs: timely risk control is required, including freezing relevant accounts involved, requiring the accounts involved and their upstream and downstream partners to improve their KYC levels and provide supporting documents, placing risky tokens in the observation zone, suspending transactions, taking them offline, and rescuing and compensating for user losses.
For regulators: They need to collaborate with law enforcement agencies, VASPs, security agencies, law firms, industry associations, media, and other credible actors to establish dedicated working groups for specific cases. These teams will conduct investigations, responsible disclosure, and public opinion monitoring and guidance. Furthermore, contingency plans and standard operating procedures (SOPs) for post-event handling need to be established in advance. This can be led by regulators, with specialized committees spearheading the development of these SOPs to address potential future emergencies.
Overall, anti-money laundering efforts require a comprehensive response framework encompassing pre-, mid-, and post-event responses to avoid a reactive response post-event. Pre-emptive action requires regulatory-led contingency plans and standard operating procedures (SOPs), with multiple stakeholders, including law enforcement, VASPs, security agencies, law firms, industry associations, and the media, implementing their respective roles. During the process, real-time monitoring and intelligence sharing mechanisms are needed to identify and assess on-chain and community risks, providing a robust basis for post-event intervention. Within this framework, address risk management and blacklisting mechanisms play a crucial role in blocking high-risk capital flows. However, these mechanisms are not static "absolute lines of defense" but rather dynamic infrastructure requiring continuous updates, cross-border collaboration, and multi-party verification. As these mechanisms progress towards global interoperability and automated response, they are becoming a crucial pillar in addressing complex and rapidly evolving money laundering practices within the crypto ecosystem.
4. Liquidity Pool and Cross-Chain Monitoring
Risk management based solely on a single address remains insufficient to cover complex capital flows. With the development of DeFi, the scale of capital flows through decentralized exchanges (DEXs), automated market making (AMM) platforms, and cross-chain bridges continues to expand. These links, due to their anonymity, cross-chain nature, and high technical barriers, have become hotbeds for money laundering and terrorist financing. Therefore, achieving full-chain visualization and risk monitoring of liquidity pools and cross-chain transactions is technically necessary.
(1) Risk characteristics of liquidity pools
In a liquidity pool, users typically deposit assets into smart contracts for exchange with other traders or to earn liquidity benefits. On the surface, these transactions appear to be normal asset swaps, but in a compliance context, they present the following risks:
Anonymity and mixability: When users exchange tokens in the pool, the transaction path is highly obfuscated, making it difficult to track the source and destination of funds;
High-frequency cross-asset transfers: High-frequency cross-asset transfers are very common in AMM structures. Hackers and money launderers often use multiple pools and different tokens to conduct circular transactions, thereby evading the monitoring of a single chain.
Arbitrage and flash loans mask transactions: Flash loans and arbitrage transactions utilize instantaneous fund movements to quickly complete fund transfers, making it difficult for traditional AML systems to block them in real time.
Therefore, liquidity pool monitoring requires a combination of smart contract call parsing, transaction path reconstruction, and abnormal transaction pattern identification. For example, by parsing function calls such as swap, addLiquidity, and removeLiquidity and recording the corresponding fund flows, potential risks can be identified.
(2) Cross-chain bridge monitoring
Cross-chain bridges allow users to transfer assets from one chain to another (e.g., Ethereum → BSC/Polygon). While cross-chain mechanisms improve asset liquidity and interoperability, they also facilitate money laundering:
Multi-chain anonymity: A sum of money can be transferred from chain A to chain B via a cross-chain bridge, and then the path can be obfuscated through multiple transactions, complicating on-chain traceability.
Contract vulnerabilities and hacker exploitation: Historically, numerous cross-chain bridge hacking incidents have resulted in the theft of hundreds of millions of dollars in assets. If hackers rapidly disperse funds across multiple chains and liquidity pools through cross-chain operations, it becomes extremely difficult to freeze and track them afterwards.
Inter-chain time delay: Cross-chain transactions generally have confirmation delays. This time difference can be used for security, but in AML scenarios it means a smaller window for regulatory freezes and transaction interceptions.
To address these issues, it is technically necessary to establish a cross-chain transaction mapping table. By monitoring the core events of the cross-chain bridge contract (such as lock, mint, and burn), combined with on-chain capital flow data and high-risk address libraries, the capital path can be reconstructed to form a full-link cross-chain portrait.
(3) On-chain monitoring methods
For specific on-chain monitoring methods, reference can be made to industry practices. For example, through transaction graph analysis, a directed acyclic graph (DAG) or capital flow network can be constructed, node risk levels can be labeled, and circular transfers and decentralized capital flow patterns can be identified. Through behavioral pattern recognition, rule engines or machine learning models can be used to capture typical money laundering techniques, such as cross-pool arbitrage splits, cross-chain flash loan aggregation, and other abnormal behaviors. At the same time, liquidity pools and cross-chain addresses can be incorporated into dynamic risk scoring models, and a weighted calculation is performed on fund size, transaction frequency, historical behavior, and labeled results to form a comprehensive risk score, thereby enabling early warning and interception based on score thresholds. The key to liquidity pool and cross-chain monitoring lies in real-time and full-chain visualization, that is, the source and destination of each fund can be traced, and alerts or freezes can be triggered immediately when high-risk behavior occurs.
(4) Integration with compliance systems
At the compliance application level, liquidity pool and cross-chain monitoring aren't isolated modules; instead, they must be deeply integrated into the overall AML system. The technical architecture typically includes an on-chain event listener for real-time capture of transaction events related to liquidity pools and cross-chain bridges; an AML middleware platform that integrates these events with a high-risk address library, dynamic blacklists, and a trading rules engine to enable automated risk control decisions; and a visual risk control platform that supports manual analysis and regulatory reporting through fund flow tracking graphs, risk heat maps, and alert reports. This end-to-end design enables institutions to visualize the entire capital chain in a decentralized and cross-chain environment, helping to mitigate the risks of money laundering and terrorist financing.
5. AML Models for AI/ML
Traditional rule-based AML systems (such as blacklist matching, transaction limits, and frequency limits) have limitations in on-chain scenarios. Money launderers can circumvent these systems through methods like splitting, cross-chain transactions, and multi-hop transactions. Furthermore, static rule-based detection cannot cover all new evasive tactics. Therefore, AI/ML (artificial intelligence and machine learning) technologies are gradually playing a role in AML research and some practices. Through data-driven, pattern recognition, and anomaly detection, they help proactively identify potential risk patterns, thereby improving risk identification efficiency and coverage while maintaining regulatory compliance and transparency.
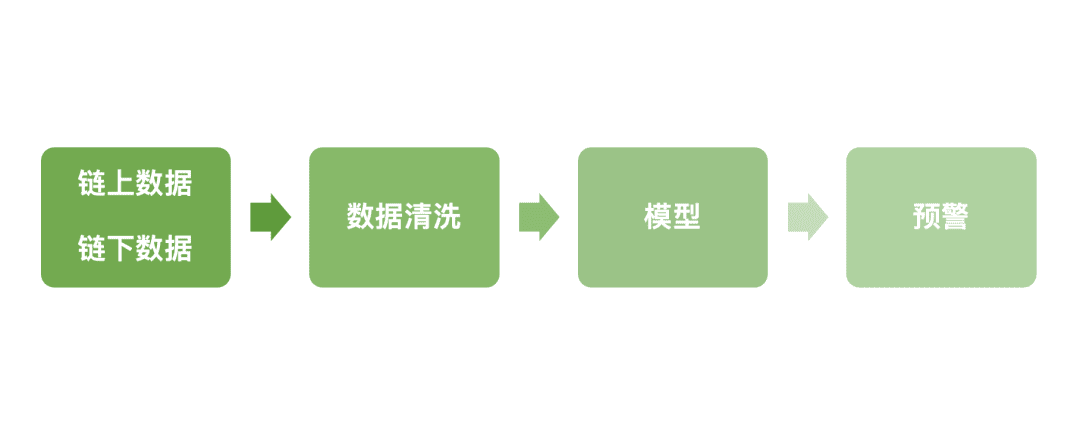 (1) Data source and data cleaning
(1) Data source and data cleaning
The key to AI/ML models lies first in the integration of multi-source data and feature design. On-chain data includes transaction metadata (timestamp, amount, sending and receiving addresses, smart contract calls), transaction graph features (address degree, funding path length, number of cycles, cross-chain jump characteristics), and address tag information (high-risk flags, exchange accounts, DeFi protocol addresses, etc.).
Off-chain data supplements identity and background information, such as KYC data, account history, judicial investigation results, sanctions lists, and open-source intelligence (OSINT). Through data cleaning and vectorization, this multidimensional data is transformed into model-recognizable features, such as address risk scores, transaction anomaly indices, and capital flow concentration indicators. Establishing a fusion relationship between high-dimensional on-chain behavior and off-chain identity attributes is key to building ML-based AML models.
(2) Anomaly detection and classification model
In terms of modeling methods, AI algorithms are generally used for two core tasks. The first is anomaly detection, with common methods including isolation forests, autoencoders, and, in recent years, graph neural networks (GNNs). These models have shown potential in research and selected scenarios for identifying unusual patterns such as fund splitting, flash loan arbitrage, and rapid cross-chain transfers. Their unique advantage lies in not relying solely on known "blacklists" of money laundering addresses, thus helping to uncover previously unidentified new risk tactics and offset the lag of traditional rule-based engines. The second is risk classification, which typically employs methods such as gradient boosting trees, random forests, or deep neural networks. These methods are trained on annotated historical data to assign risk levels to addresses or transactions. High-risk transactions may be automatically flagged as key concerns or submitted to manual review. The potential advantage of these models lies in their ability to learn nonlinear relationships between complex transaction characteristics and behavioral patterns, thereby improving the accuracy and coverage of risk identification.
(3) Graph Neural Networks and On-Chain Behavior Analysis
GNNs possess unique topological processing capabilities. In some research and practical applications, they have demonstrated potential for identifying complex money laundering patterns. For example, by analyzing the community structure of transaction networks, they can effectively identify the "hub-and-spoke" topology characteristic of coin mixing services—where large amounts of funds converge from dispersed peripheral addresses to a central node, where they are mixed and then redistributed to a new set of addresses. This pattern recognition capability enables the system to accurately identify potential risks even if the transaction behavior of a single address appears normal, as long as it is located in a dense subgraph of a high-risk cluster. In some explorations, combining GNNs with traditional machine learning models not only complements existing money laundering pattern recognition but also enhances the ability to detect new risky tactics.
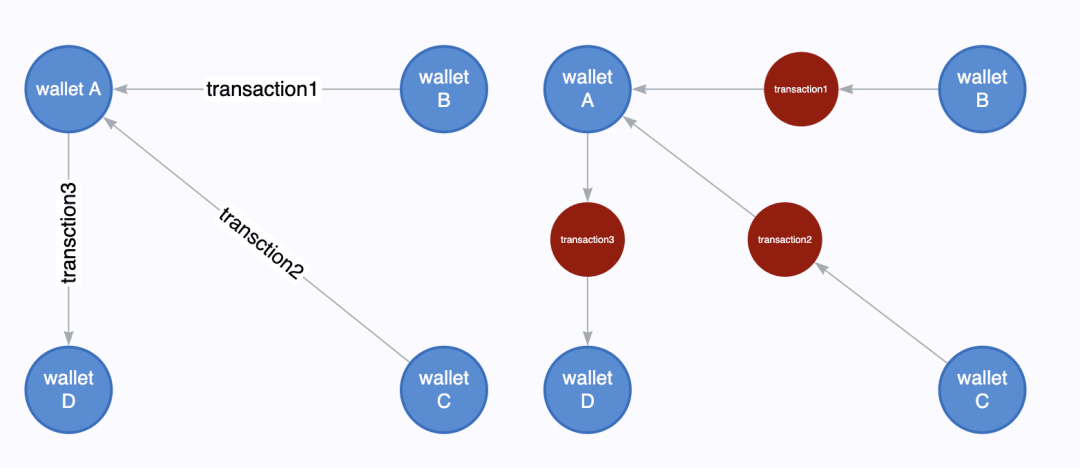 (Financial transaction chart, source: ML2)
(Financial transaction chart, source: ML2)
(4) Model deployment and real-time monitoring
At the technical implementation level, the full value of AML models can only be realized through real-time monitoring. The model must support real-time or near-real-time reasoning and be integrated with pre- and post-transaction monitoring systems. In the pre-transaction phase, the system can calculate risk scores as transactions are about to occur, triggering the fastest possible blocking or manual review of high-risk transactions. In the post-transaction phase, the system continuously scans the on-chain transaction network, identifying emerging high-risk addresses or behavioral patterns and dynamically adding them to blacklists and risk databases. Furthermore, the model must establish a self-learning and feedback loop. This means continuously optimizing parameters and feature design through manual review and feedback from law enforcement agencies to reduce false positives and false negatives, striving for increased accuracy with use.
A practical example is MistTrack MCP (https://mcp.so/server/misttrackmcp/slowmist). Users can directly use natural language to call MistTrack's on-chain analysis API in MCP-supported clients like Claude and Cursor. This allows for functions such as address profiling, risk scoring, and transaction graph construction, enabling blockchain asset tracking, risk assessment, and transaction analysis. This not only improves the efficiency of on-chain data analysis but also lowers the barrier to entry. For example, users can directly issue a request to an MCP-supported AI tool, such as "Please track the fund flow between this address and exchanges, with a depth of 2: [ETH_ADDRESS]." The AI tool will automatically initiate an API call through MistTrack MCP and return complete and readable analysis results.
 MistTrack MCP currently supports more than 10 on-chain analysis tools, covering multiple dimensions such as risk identification, address profiling, and transaction graph construction:
MistTrack MCP currently supports more than 10 on-chain analysis tools, covering multiple dimensions such as risk identification, address profiling, and transaction graph construction:
 This "AI + AML tool" combination model demonstrates the future development direction of AML technology: in a complex on-chain environment, using AI as an interaction layer and calling underlying professional analysis tools to achieve more intuitive and automated risk monitoring and compliance operations.
This "AI + AML tool" combination model demonstrates the future development direction of AML technology: in a complex on-chain environment, using AI as an interaction layer and calling underlying professional analysis tools to achieve more intuitive and automated risk monitoring and compliance operations.
(5) Compliance requirements and transparency
Compliance is another core challenge in the practical application of AI/ML AML models. For example, under Hong Kong's regulatory framework, all AI-based risk monitoring systems must meet explainability requirements. Transaction risk scores cannot be "black boxes" but must be able to explain their basis to auditors and regulators. Regarding data usage, off-chain data related to KYC and sanctions lists must comply with legal requirements for privacy protection and AML/CFT compliance. Data storage, access, and cross-border transfers require clear compliance mechanisms. Regarding system governance, model updates, feature selection, and test results must maintain auditable records to facilitate subsequent regulatory inspections or judicial review. While these requirements increase the complexity of technical implementation, they also ensure the legitimacy and transparency of AI/ML in AML.
AI/ML is gradually evolving from an auxiliary tool to a core engine for stablecoin AML. Not only do they offer potential advantages over traditional rule-based approaches in risk identification efficiency, they are also more adaptable to the challenges posed by complex scenarios such as cross-chain, DeFi, and anonymization. With increasing regulatory clarity on AI compliance and deepening global data collaboration, AI/ML models are poised to build a dynamic, scalable, and regulatory-compliant intelligent AML prevention and control network, supporting the safe circulation and compliant development of stablecoins.
4. Full-process prevention, control and governance framework
1. AML lifecycle prevention and control closed loop
If stablecoin anti-money laundering controls rely solely on a single link, loopholes are likely to emerge. A more practical approach is to cover the entire lifecycle of funds, from entry to circulation to disposal, gradually forming a dynamic, iterative closed loop, rather than fragmented, single-point protection. Industry practice typically divides this into three phases: pre-, mid-, and post-event. This closed-loop control is then complemented by a combination of technology and compliance mechanisms, gradually exploring a viable model.
(1) Beforehand: Source control and risk prevention
The pre-stage focuses on source control and risk prevention, with the emphasis on reducing risk exposure from the point of capital entry. Through strict customer due diligence and risk stratification, we ensure as much as possible that the identity of the entity entering the system is authentic and trustworthy, thereby reducing the compliance pressure in subsequent links.
KYC and Customer Due Diligence: Strict KYC (Customer Identity Verification) procedures are implemented at key source links such as user account opening, stablecoin minting, and fiat currency exchange. User information such as name and ID card are collected and verified to ensure the authenticity of the identity of the subject entering the system. At the same time, pre-screening is carried out in conjunction with sanctions lists and address tag libraries to identify high-risk entities and reduce their possibility of entering the system.
Risk stratification and rule constraints: Risk stratification of customers and users is performed based on KYC results, and different levels of monitoring intensity are assigned based on historical behavior, source of funds, and transaction patterns. At the same time, threshold conditions are set through the rule engine, such as the upper limit of a single transaction amount, transaction frequency limit, cross-chain path whitelist, etc., to build a risk "constraint network" in advance.
(2) During the event: real-time monitoring and rapid response
The in-process stage focuses on real-time monitoring and rapid response, promptly identifying and intercepting high-risk behaviors as much as possible during the flow of funds, while taking into account transaction efficiency and traceability.
Dynamic risk monitoring: Through on-chain graph analysis, transaction pattern recognition, and anomaly detection models, the system can identify high-risk behaviors during the flow of funds (such as high-frequency small-amount splits, concentrated inflows from mixing services, and multi-hop transfers across cross-chain bridges). At the same time, relying on cross-platform API docking, real-time risk signals are shared among different virtual asset service providers (VASPs) to avoid regulatory blind spots.
Transaction verification and risk interception: Multi-dimensional verification is initiated before the transaction is confirmed to check the integrity and legality of the initiator and recipient's KYC, verify whether the address is on the blacklist/high-risk list, and generate a risk score based on the transaction amount and historical behavior; if anomalies are found, such as the risk score exceeds the set threshold, the system can trigger automatic blocking or manual review. This process requires the AML system to have high concurrent processing capabilities to ensure compliance control without significantly affecting high-frequency transactions. The verification results and risk scores will be written to the audit database to facilitate real-time query and tracking by regulators.
The "Travel Rule" has been implemented: According to FATF Recommendation 16, financial institutions must collect, transmit, and verify the identities of both originators and recipients during large or cross-border fund transfers. Furthermore, stablecoin systems must securely embed off-chain KYC data into compliance processes when on-chain transactions occur. This means that stablecoin issuers must establish a reliable mapping between on-chain transactions and off-chain customer identity information to ensure traceability and transparency of cross-border and large-value fund flows. Furthermore, strong encryption and minimal disclosure are required during the transmission and verification process to prevent identity information from being exposed during on-chain transmission.
Technically, off-chain information is typically linked to transactions through public key encryption. Sensitive data is not written directly to the blockchain but instead stored in a compliant database, with authenticity and verifiability guaranteed through hash signatures or zero-knowledge proofs (ZKP). However, these methods are still constrained by computing power costs and maturity, requiring further validation in practice. Furthermore, large-value transactions often span different platforms or multiple links, placing higher demands on standardized information transmission and protocol interoperability. Some practices have referenced the ISO 20022 messaging standard used in traditional finance, while others have adopted customized JSON/XML protocols, routing and formatting information between different platforms and links through compliant middleware (system modules that support data exchange and verification) or relay nodes. However, issues such as inconsistent data formats and the risk of API abuse still need to be addressed.
In practice, the Travel Rule is feasible for on-chain transactions. For example, when a user initiates a $500,000 stablecoin transfer from Exchange A to Exchange B, the initiator's KYC information can be encrypted and attached to the transaction request. This information is then transmitted to Exchange B via a standardized protocol. The recipient can only complete the crediting process after verifying KYC integrity, checking sanctions lists, and assessing risk scores. Verification data throughout the entire process is stored in an off-chain database, and compliance reports can be generated according to regulatory requirements. Another scenario involves large cross-chain transfers (such as USDC from Ethereum to BSC). The compliance middleware must ensure that Travel Rule information is not lost during the cross-chain process. Encrypted transmission and verification mechanisms maintain link consistency, and advanced analytical models are used to identify suspicious behavior, providing regulators with a complete traceability of the capital flow.
(3) Afterwards: Evidence retention and feedback optimization
The post-event stage focuses on evidence retention, fund tracing and system optimization to form a "feedback loop", which not only meets the basic needs of compliance audits and law enforcement collaboration, but also provides a basis for subsequent improvements to the prevention and control system.
Evidence retention and traceability: All monitoring results, risk scores, and transaction records must be recorded in an unalterable manner, usually stored in an off-chain audit database, to ensure that the flow of funds can be fully traced to meet judicial investigation and compliance audit requirements.
Rapid law enforcement response: When receiving a freezing order from law enforcement, the system needs to respond quickly and lock suspicious funds in on-chain addresses or trading accounts as soon as possible to avoid escalating risks.
Feedback loop: Manual review results and law enforcement investigation results are fed back into the rule base and machine learning model to continuously optimize risk scoring parameters (combining on-chain data, cross-chain events, and liquidity pool monitoring results) to reduce false positives and missed negatives. Analysis results of cross-chain bridge vulnerabilities, protocol incompatibilities, and processing delays are used to improve system design and processes, driving the evolution of the AML system towards "real-time learning."
Compliance Reporting: The system generates compliance reports in accordance with regulatory requirements, including KYC verification records, transaction risk scores, and fund flow tracing information; it supports cross-jurisdictional data sharing and provides technical support for international law enforcement collaboration.
(4) Overall closed loop: dynamic learning and continuous optimization
The AML lifecycle closed loop is not a simple superposition of three stages, but a system of "dynamic iteration and continuous optimization" formed through the interaction of the three stages: before, during, and after.
Closed-loop operation: Following the cyclical logic of "risk discovery (identifying potential risks through on-chain monitoring and anomaly detection models) → early warning triggering (high-risk transactions trigger automatic response or manual intervention) → manual/regulatory review (compliance team or regulator reviews abnormal transactions) → law enforcement collaboration (sharing data with law enforcement agencies and responding to freeze orders) → model optimization (based on review and law enforcement results, iterating AI/ML models and rule bases to reduce false positives and false negatives)", the output of each link serves as the input of the next link, achieving closed-loop self-optimization of risk prevention and control.
AML middle-office architecture: With the AML middle-office as the core of the architecture, it realizes three major functions: data aggregation and standardization (aggregating on-chain transactions, smart contract events, cross-chain bridge records and liquidity pool operation data; unifying off-chain KYC information, blacklists, sanctions lists, law enforcement feedback, etc. into a standardized format for easy use by models and rule engines); unified risk assessment engine (combining rule engines, AI/ML models and graph analysis results to generate comprehensive risk scores for transactions or addresses; the score can consider factors such as capital scale, transaction frequency, path complexity, cross-chain operations and historical tags); strategy execution and event triggering (high-risk transactions can trigger automatic restrictions or manual review, depending on the regulations of the jurisdiction; abnormal transactions can generate early warnings, feedback to the compliance team, and report to regulators when necessary), ensuring real-time and traceability, so that data in each monitoring link can be reviewed.
Through the deep integration of on-chain and off-chain technologies (such as zero-knowledge proofs, encrypted transmission, and compliance databases) and systems (such as Know Your Customer (KYC) processes, implementation of the Travel Rule, and cross-platform collaboration mechanisms), stablecoin AML prevention and control can balance transaction efficiency and user experience while meeting regulatory requirements for traceability of large-scale and cross-border capital flows. If these modules operate in isolation, they often only provide a partial perspective and lack comprehensive protection capabilities. Therefore, an end-to-end management mechanism is necessary through technological integration, closed-loop processes, and law enforcement collaboration: proactive prevention to reduce risk exposure, in-process monitoring to mitigate immediate risks, and post-event review and optimization of models. The interaction of these three forms a "dynamically learning" AML system. This closed-loop mechanism not only improves compliance efficiency but also provides technical support for cross-border regulatory mutual recognition and international law enforcement collaboration, advancing stablecoin AML from fragmented, single-point protection to a systemic governance approach that is visual, traceable, and collaborative.
2. Pre-trade and post-trade monitoring
Beyond achieving multi-faceted integration, a stablecoin AML system must also cover different stages of the transaction lifecycle, such as pre-transaction prevention and post-transaction tracking, forming a closed-loop monitoring framework. Such a system can intercept risks before they occur while also enabling traceability and attribution after transactions are complete, achieving end-to-end risk prevention and control and compliance response. Technically, the core approach lies in integrating on-chain transaction behavior, off-chain identity information, real-time risk scoring, and global sanctions lists, while enabling timely responses through automated and intelligent means.
 (1) Pre-transaction monitoring
(1) Pre-transaction monitoring
Pre-transaction monitoring is mainly aimed at risk prevention and compliance blocking. The key points include:
The flow of funds undergoes identity verification and risk assessment before entering the blockchain;
With the help of KYC information collected under the Travel Rule, the system can verify the identities of the initiator and recipient;
Check if the address is involved in a high-risk history, blacklist, or sanctions list;
If the transaction involves cross-chain or cross-platform operations, the identity data of the other platform should be synchronized as much as possible through the compliance middle platform or relay node for inspection.
Risk scoring and automatic blocking
The system calculates a comprehensive risk score based on indicators such as address historical behavior, capital flow complexity, transaction amount and frequency;
High-risk transactions are automatically blocked or triggered for manual review to ensure that transactions are controlled before entering the blockchain;
AI/ML models can assist in analyzing more complex capital flow patterns and improve the ability to identify potential anomalies.
Transaction warning and regulatory reporting
For obviously abnormal transactions, the system generates an early warning and reports it to the regulatory interface in real time;
Early warnings include suspicious transaction paths, potential money laundering activities and large cross-border transactions, ensuring compliance with the transparency and real-time compliance requirements of various jurisdictions.
(2) Post-transaction monitoring
Post-transaction monitoring focuses on abnormal behavior analysis and on-chain tracing to identify potential risks and provide evidence for law enforcement:
Even if a transaction is not blocked in the previous stage, the system will still analyze its capital flow path through on-chain transaction maps and pattern analysis to identify complex patterns such as abnormal circular transfers, rapid splits, and cross-chain arbitrage;
Perform pattern recognition on complex transaction paths such as liquidity pool operations and DeFi aggregator transfers to enable cross-platform tracking.
Time series and behavioral pattern analysis
Conduct historical analysis of transaction frequency, amount distribution, and address associations to identify "slow bleaching" or "structured transfer" patterns in money laundering;
Utilize AI models with adaptive thresholds to continuously optimize detection capabilities and reduce the ratio of missed alerts and false positives.
Transaction attribution and law enforcement support
Generate a complete chain report for suspicious transactions, including transaction ID, address tag, timestamp, and associated KYC information (masked within compliance scope);
The report can be used by regulatory or law enforcement agencies for freezing, investigation and evidence collection.
Closed-loop feedback mechanism
Abnormal behavior discovered after a transaction can be fed back into pre-transaction monitoring rules and AI models for continuous optimization;
When a certain type of cross-chain bridge is identified as a high-risk path, the system will automatically update the list of suspicious addresses and paths, thereby blocking or marking similar risks in advance in subsequent pre-transaction monitoring.
(3) Key points for technology implementation
Real-time transaction control: Stablecoin transactions are often high-frequency and cross-border, so the monitoring system should combine on-chain event streams with off-chain data to complete risk assessments in the shortest possible time.
Graph visualization and analysis: Graph analysis and visualization technologies can help compliance personnel intuitively understand the multi-level relationships of capital flows and achieve panoramic tracking across chains and platforms.
Fusion of rules and AI: Static rules can effectively address known risks, while machine learning and graph neural networks can help discover potential new abnormal patterns. The combination of the two can improve detection accuracy while ensuring transparency and compliance.
Auditability: All pre- and post-trade data, scores, and reports must be stored in a traceable, compliant database, readily accessible to regulatory and law enforcement inquiries.
3. Emergency and response mechanisms
Even with established pre- and post-trade monitoring systems, unexpected events can occur, such as suspicious transactions exceeding established risk control thresholds, theft of funds through hacker attacks, or system failures. These situations are often sudden and high-risk. Without effective emergency response mechanisms, risks can spread rapidly, leading to systemic risks. Therefore, establishing an emergency response and disposal mechanism within the AML/CFT framework that integrates technology and processes is an essential component of a compliance system. Its goal is to rapidly respond, effectively isolate risks, and enable traceable reporting and optimization.
Emergency response mechanisms typically follow a four-tiered approach: monitoring and alerting – risk assessment – blocking and controlling – and incident review, forming a comprehensive, top-down response chain. When the system detects abnormal behavior, it triggers an alert as quickly as possible within a controllable link and automatically initiates the response process according to pre-set rules. This multi-tiered alert system prioritizes the source of the anomaly and the level of risk. Examples include high-risk events triggered by pre-transaction monitoring, unusual patterns discovered through on-chain graph analysis, and potential cross-chain money laundering identified with the assistance of AI models. The system can tailor responses to different risk levels, ranging from "red alerts" for immediate blocking to "yellow alerts" requiring manual review, ensuring both security and transactional fluidity. Unlike routine pre-transaction monitoring and blocking, emergency response mechanisms focus on rapid response after an incident occurs, including isolating abnormal fund flows, freezing cross-chain transactions, and intervening with multi-sig permissions.
 However, within the overall framework, events at different levels require differentiated responses based on a tiered strategy. When an alarm is triggered, the system must complete a risk assessment and categorize the event within a specific level within the shortest possible time. This assessment combines transaction amounts, frequency, historical behavior, cross-chain paths, and blacklist data to quickly calculate a comprehensive risk score. If the risk level is extremely high, the system can freeze the funds with permission, restricting fund movement within the controllable asset range through multi-signature wallets or smart contracts. Standard on-chain addresses can be marked and subsequently tracked. Low- and medium-risk events, on the other hand, undergo a manual review process, generating a chain analysis report to assist compliance personnel in their assessments. This tiered approach strikes a balance between efficiency and robustness, avoiding the compliance friction caused by a "one-size-fits-all" approach.
However, within the overall framework, events at different levels require differentiated responses based on a tiered strategy. When an alarm is triggered, the system must complete a risk assessment and categorize the event within a specific level within the shortest possible time. This assessment combines transaction amounts, frequency, historical behavior, cross-chain paths, and blacklist data to quickly calculate a comprehensive risk score. If the risk level is extremely high, the system can freeze the funds with permission, restricting fund movement within the controllable asset range through multi-signature wallets or smart contracts. Standard on-chain addresses can be marked and subsequently tracked. Low- and medium-risk events, on the other hand, undergo a manual review process, generating a chain analysis report to assist compliance personnel in their assessments. This tiered approach strikes a balance between efficiency and robustness, avoiding the compliance friction caused by a "one-size-fits-all" approach.
Another key element of the emergency response mechanism is incident recordkeeping and regulatory reporting. Each incident must generate complete chain information, including transaction IDs, on-chain transfer paths, off-chain KYC data (decrypted or shared within the scope of compliance), risk scores, and the final disposition. This information not only meets the incident response and recordkeeping requirements of regulators and law enforcement agencies, but also provides them with readily usable compliance reports.
From a technical implementation perspective, emergency response relies on several key capabilities. First, smart contracts and multi-signature control enable the immediate freezing or restriction of contract functionality within the controllable asset range upon identifying an anomaly, preventing hackers from exploiting time lags to transfer assets. Second, analytical tools such as graph neural networks have demonstrated their ability to assist in identifying potentially anomalous paths within complex capital flows. Third, auditable logging and data preservation ensure that every action taken during an emergency response must be fully documented for internal review and external compliance audits. Finally, closed-loop optimization ensures that every emergency response is not an isolated incident, but rather an opportunity for system learning and evolution, continuously improving the model's adaptability and accuracy through feedback.
In summary, stablecoin emergency response and disposal mechanisms are not only the "last line of defense" for risk management but also a dynamic pillar within AML/CFT compliance systems. However, in practice, relying solely on internal compliance and risk management teams can sometimes be insufficient to handle complex hacker attacks or cross-chain theft. Therefore, employing the emergency response services of professional security teams is a crucial supplement to regulatory compliance. For example, SlowMist's security emergency response service can rapidly assist project owners in emergency situations with fund containment, on-chain and off-chain intrusion analysis, hacker profiling, and stolen asset tracking. Furthermore, it integrates the AML blockchain anti-money laundering system and the InMist threat intelligence network to maximize the efficiency of fund tracing and freezing. The value of this service lies in helping project owners quickly restore order after black swan events. In conjunction with internal compliance systems, it provides a dual guarantee of "internal mechanisms + external support."
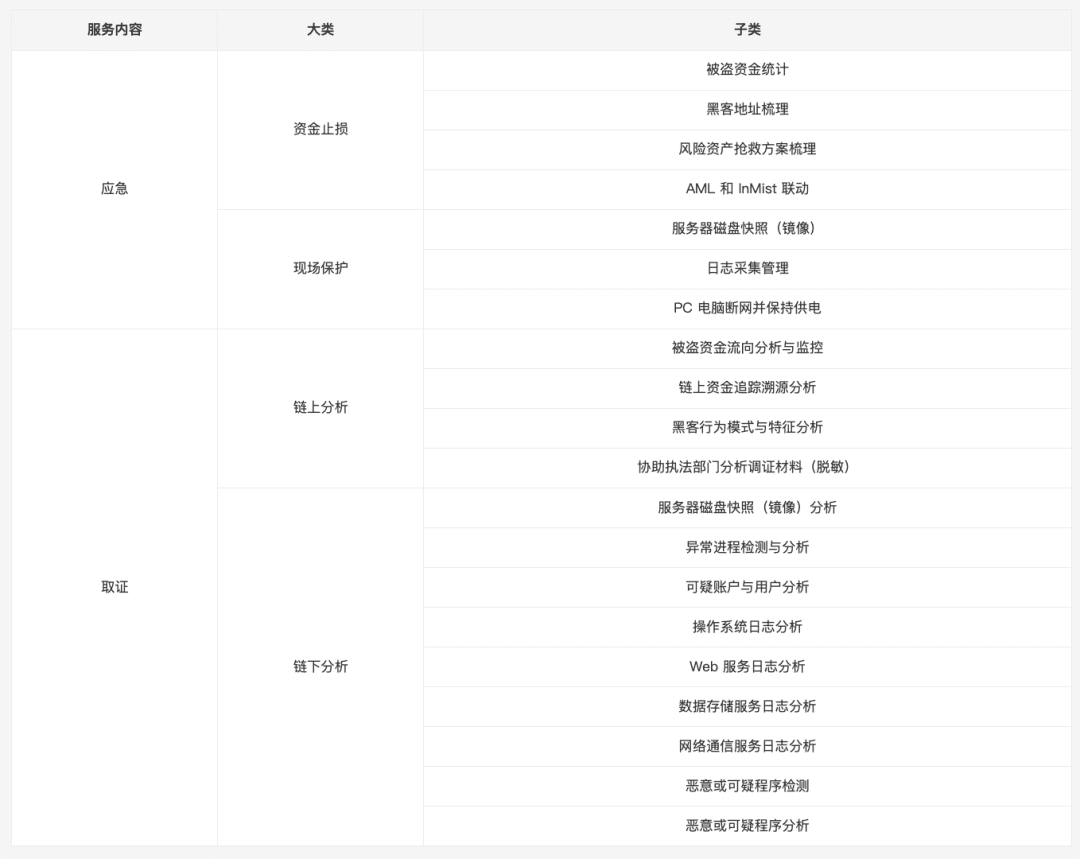 4. On-chain and off-chain data integration
4. On-chain and off-chain data integration
While on-chain data is inherently transparent, it also carries anonymity. While off-chain data can provide comprehensive identity and compliance information, it is often dispersed across different platforms and institutions. If these two types of data remain disconnected for extended periods, compliance systems are prone to developing monitoring blind spots.
On-chain, stablecoin-related transaction flows, contract events, and cross-chain migration paths are direct sources for risk monitoring. By continuously acquiring transaction hashes, addresses, amounts, timestamps, and contract calls through nodes or APIs, a foundational on-chain behavior database can be constructed. Furthermore, address tags and relationship mappings are established around this data, correlating addresses with potential identity types, historical transaction patterns, and risk levels. This creates a map of on-chain behavior, assisting in tracking the aggregation, splitting, and cross-chain migration of funds between different wallets and contracts, and supporting the identification of abnormal patterns.
Off-chain data complements the anonymity deficiencies of on-chain data. Pre-transaction KYC information, account risk records, historical suspicious transaction reports, and external blacklists and sanctions lists are all crucial references for AML risk assessment. By connecting with financial intelligence agencies, cross-border payment systems, and blockchain intelligence services, stablecoin issuers can obtain the latest high-risk address and transaction intelligence, compare it with local data, and improve the timeliness and accuracy of risk identification.
When on-chain and off-chain data are integrated into a unified data platform, compliance analysis can transcend traditional data barriers. A unified data model maps identity information, address tags, and transaction paths from different sources into a common risk framework. Combined with graph databases or graph analytics, this can reveal more subtle risk structures. For example, a seemingly normal small transaction, if highly coupled along its path with multiple historically high-risk addresses, could indicate money laundering or capital recycling. In this scenario, AI models can be used in conjunction with rule engines: the rule engine provides efficient filtering for known patterns, while the AI model helps uncover potential unknown risk patterns.
Security and privacy protection are always key prerequisites during the data integration process. Off-chain KYC and AML data must be encrypted, stored, and transmitted, with strict access control to prevent the misuse or leakage of sensitive information. Audit logs must be generated for all operations to ensure traceability for compliance teams and regulators. This balance between security and compliance not only meets regulatory requirements but also strengthens user trust in the system.
By integrating on-chain and off-chain data, the stablecoin compliance system can achieve more comprehensive risk visualization and multi-dimensional linkage monitoring, taking into account blockchain transparency and off-chain identity information, providing issuers with a more solid technical foundation and more resilient regulatory docking capabilities.
5. API interface and encrypted transmission
As mentioned above, the security of data interaction and regulatory information transmission is crucial. To achieve secure interoperability between on-chain and off-chain data, standardized interfaces and encrypted transmission become key support.
 (1) API interface design principles
(1) API interface design principles
Modularity and cross-platform compatibility
Functions such as pre-transaction monitoring, post-transaction analysis, address risk query, and blacklist comparison should be encapsulated as independent interfaces;
Ensure that the interface is compatible with internal monitoring systems, third-party intelligence systems and regulatory systems to facilitate rapid information exchange.
Security and access control
Interfaces should use strong authentication mechanisms to ensure that only authorized applications and personnel can access sensitive data;
Access rights should be managed in a refined manner, with data visibility strictly divided according to roles and functions to avoid "overstepping authority" issues;
All call records are saved in audit logs to provide a basis for subsequent tracing and meet regulatory review requirements.
(2) Encrypted transmission and data protection
Transport layer encryption
Whether it is API calls or data reporting, it is recommended to use TLS 1.3 or higher encryption protocol;
Sensitive fields such as ID number, wallet address mapping information, and transaction amount are end-to-end encrypted.
Data encryption and desensitization
Off-chain KYC/AML data is encrypted using AES-256 when stored in the database;
The data interface provided to the outside world needs to desensitize sensitive information, such as hashing addresses or partially hiding ID card information;
Reversible encryption and audit mechanisms should be supported so that the original data can be restored during regulatory or internal compliance audits.
(3) Cross-chain and third-party system interface
Connect to cross-chain bridges and other public chain networks, and obtain transaction flows, address activities, and smart contract events through encrypted interfaces;
Establish secure interfaces with third-party AML/CFT intelligence services and blacklist databases to enable risk matching and alert generation;
Supports asynchronous and batch call mechanisms to improve the efficiency of high-concurrency on-chain transaction data processing and off-chain queries, but delays and uncontrollable links still need to be considered.
(4) Automation and regulatory reporting interface
Build an automated regulatory reporting interface to submit abnormal transaction reports, suspicious transaction reports, and on-chain and off-chain integrated data in accordance with regulatory requirements;
The reporting process is encrypted and signed to ensure information integrity, non-tampering and traceability;
Supports formatted output (JSON, XML, CSV) and interface receipt confirmation to improve the efficiency of regulatory end in receiving and processing information.
(5) Key points for technology implementation
Standardized interface design: modular and cross-platform compatible, making it easy to connect with internal systems and regulatory systems;
Encrypted transmission and end-to-end protection: Ensure data security during transmission and storage, and desensitize sensitive information;
Permission and audit mechanism: strictly control interface access rights and record detailed operation logs;
Cross-chain and third-party integration: supports secure interaction of multi-source data on and off the chain to achieve risk comparison;
Automated regulatory reporting: Generates encrypted reports that meet regulatory requirements to ensure a closed-loop compliance system.
The value of API interfaces and encrypted transmission mechanisms lies in that they break down data silos between different systems, enabling compliance monitoring, intelligence matching, emergency response, and regulatory reporting to work together efficiently and robustly, thereby laying a solid foundation for cross-platform and cross-institutional compliance collaboration and forming a scalable stablecoin AML technology base.
5. Recommendations and Trends
The future development of stablecoin anti-money laundering (AML) depends not only on-chain technical tools and issuers' compliance practices, but also, more fundamentally, on the gradual maturity of cross-border collaboration, data integration, and intelligent methods. A review of past law enforcement cases and on-chain analysis reveals that measures that truly improve the efficiency of cross-border fund tracing and risk management often rely on information sharing and standardized mechanisms. Therefore, the relationship between regulators and the industry should not be simply a one-way process of rule-making and passive enforcement, but should gradually evolve into a model of dynamic collaboration and joint exploration. The effectiveness of stablecoin AML relies not only on the development of technology and systems, but also requires the collaborative efforts of industry participants, regulators, and users to form a multi-layered prevention and control ecosystem.
(1) Regulatory and law enforcement agencies
The main challenges facing regulators and law enforcement agencies are the secrecy surrounding cross-border capital flows and the complexity of new on-chain instruments. Improving risk prevention and control efficiency requires progress in cross-border collaboration and data standardization. Establishing regular information-sharing mechanisms across jurisdictions regarding high-risk addresses, sanctions lists, and suspicious transaction patterns will be more effective in identifying and blocking potential risks at an early stage. In recent years, the international community has explored various cross-border data transmission and identity verification frameworks. These efforts demonstrate that the transmission of necessary information under compliant conditions provides a practical basis for reducing the secrecy of cross-border money laundering and terrorist financing.
Unified data interfaces and format specifications are also key to improving regulatory efficiency. Whether it's KYC information, on-chain transaction flows, cross-chain operations, or exception reporting, if these can be exchanged in a common format, regulators can conduct automated analysis and risk modeling at the technical level, reducing information loss and response delays caused by differing standards.
Regulatory policies themselves also need to maintain a certain degree of flexibility, especially in rapidly evolving areas like DeFi, cross-chain bridges, and liquidity pools, where traditional static rules often struggle to address emerging risks. A more pragmatic approach might be to "parallelize policy frameworks with technical guidance": setting minimum compliance standards and security baselines while encouraging issuers and service providers to test new on-chain monitoring tools, contract security mechanisms, or intelligent risk detection mechanisms in a controlled environment, thereby achieving a workable balance between regulation and innovation.
At the law enforcement level, the value of a stablecoin AML system lies not only in internal risk control, but also in supporting regulatory and investigative work:
On-chain evidence preservation: Reconstruct the capital chain through transaction graphs, contract call logs and cross-chain events, and use hash signatures or on-chain evidence storage technology to ensure data integrity and tamper-proofing.
Law enforcement interfaces and reporting: Timely submission of high-risk transactions, suspicious addresses, and fund paths through standardized interfaces (such as APIs or encrypted messages); support for pre-emptive restriction requests or post-event tracking assistance where authorized;
Multi-party collaboration mechanism: In cross-chain or cross-border transaction investigations, the system can mark judicial differences and potential risks to assist law enforcement in evidence collection; within the compliance framework, it can share anonymized risk information with other licensed institutions or infrastructure parties to enhance overall risk awareness.
Compliance coordination and cross-departmental law enforcement cooperation are key to the success of stablecoin AML. Risk control by a single institution is unlikely to cover the entire cross-border capital chain, necessitating the establishment of a cross-platform, cross-institutional risk intelligence sharing mechanism. For example, if stablecoin issuers, exchanges, and on-chain analytics firms could exchange blacklists, suspicious transaction reports, and risk scoring results through standardized APIs, this could mitigate information silos. Regulators should also promote cross-departmental joint mechanisms to foster more efficient collaboration in judicial freezing, fund disposal, and cross-border investigations, avoiding missed freezing windows due to delayed responses. Some jurisdictions are exploring regulatory sandboxes and consortium mechanisms, which provide a testing ground for integrating technical approaches with regulatory rules and may warrant further exploration on a broader scale.
(2) Industry participants
In the context of stablecoin anti-money laundering compliance, relying solely on pre-transaction KYC or post-transaction reporting of suspicious transactions is no longer sufficient to address the risks posed by complex capital flows. A more practical approach is to gradually establish a comprehensive risk monitoring system, deeply integrating transparent on-chain transaction data with off-chain identity information, sanctions lists, and historical AML reports to form a dynamic, multi-dimensional risk profile. Leveraging methods such as graph databases, behavioral analytics, and machine learning, industry participants can identify and provide real-time early warning of complex patterns such as fund splitting, address rotation, and multi-chain arbitrage. Standardized interfaces and secure transmission mechanisms ensure data security while enabling efficient integration with regulators and third-party intelligence platforms. The core of this compliance architecture lies in a "closed loop": once the monitoring system detects a suspicious transaction, the platform should be able to trigger interception, reporting, and path tracing in a relatively short period of time. These results should then be fed back into the rules engine and pre-emptive monitoring models to drive system self-correction and iterative optimization. Through this continuous evolutionary approach, industry participants can gradually enhance the resilience of risk management in an environment of high-frequency trading and complex cross-chain interactions.
At the implementation level, all parties in the industry need to establish a division of labor and collaborate on responsibilities. Stablecoin issuers should maintain transparency of their reserve assets and incorporate freezing and auditing features into their smart contracts to mitigate the potential for large-scale token abuse. Exchanges and VASPs should deploy real-time monitoring systems and tiered risk engines to promptly restrict inflows to high-risk addresses and maintain smooth communication with law enforcement agencies. Security and risk control service providers should continuously update their address tag libraries and intelligence models, providing technical support and risk assessment to the industry and regulators. Through this multi-role collaborative model, the stablecoin ecosystem can gradually establish a compliance system with clear responsibilities, shared information, and robust feedback mechanisms. While it's difficult to eliminate all risks in the short term, this approach will help improve the overall effectiveness of AML across the industry and lay the foundation for future cross-border regulatory collaboration.
(3) User
While technology and regulations are undoubtedly the core of stablecoin AML, user education is equally crucial. Some risk events stem not from system vulnerabilities but rather from users' lack of awareness of blacklisted addresses, suspicious DEXs, and illicit OTC channels, allowing them to unknowingly channel funds. To address this, stablecoin issuers and trading platforms can implement risk warning mechanisms within their product interfaces, such as regularly sending alerts about high-risk addresses or displaying risk reminders before transaction confirmations. This can reduce the likelihood of users interacting with high-risk entities and mitigate opportunities for money laundering at the source.
The prevalence of fraud cases in the OTC market in Southeast Asia and Hong Kong demonstrates that regulatory oversight and institutional risk management alone cannot fully address risks. Lack of user awareness is often a key entry point for money laundering networks. If industry associations, trading platforms, and wallet applications can collaborate on educational initiatives—for example, by providing concise compliance guidance, designing intuitive risk warning interfaces, and regularly disseminating case alerts through social media and media channels—then users' risk identification skills can be gradually enhanced. Simultaneously, establishing community reporting and feedback mechanisms is equally important. If users can conveniently submit suspicious addresses or unusual transaction information, compliance systems can gain more first-hand intelligence, which, after verification, will be incorporated into risk databases, thus forming a multi-layered prevention and control network encompassing regulators, industry, and users. In this way, user education transcends mere information dissemination and gradually evolves into a risk-coordination mechanism. Under the policy guidance of regulators, if industry players can establish ongoing user education and feedback channels, the entire stablecoin ecosystem will likely gain stronger compliance support in preventing fraud, curbing money laundering, and enhancing public trust.
(4) Trend
In the long term, the AML prevention and control approach for stablecoins is gradually showing a trend of parallel advancements in intelligence and standardization. On the one hand, as the volume of on-chain and off-chain data continues to grow, artificial intelligence, intelligent analysis technologies, and zero-knowledge proofs are expected to further enhance monitoring accuracy and privacy protection. On the other hand, the industry's reliance on standardization is also increasing. Whether it's compliance modules, cross-border interfaces, or automated audits and security templates, future compliance systems are likely to be built on reusable, auditable modular designs to meet regulatory requirements while maintaining transaction efficiency.
On the regulatory front, the FATF framework and stablecoin regulations across major jurisdictions are gradually converging, potentially improving cross-border compliance recognition and collaboration in sanctions enforcement. Some regions are also exploring regulatory and data sandboxes, providing a testing environment for the industry to test new on-chain monitoring tools, contract security solutions, and intelligent risk control mechanisms. On the ecosystem level, compliance middleware, cross-chain risk control interfaces, and intelligent risk detection methods are gradually becoming integral to stablecoin infrastructure, enabling closer integration of AML monitoring with daily transaction execution.
Overall, the future of stablecoin AML is likely to evolve from the efforts of a single institution or technology to a collaborative network across jurisdictions and industries. The goal isn't simply to achieve comprehensive coverage, but rather to find a relatively sustainable balance between efficiency and compliance, and innovation and regulation, through flexible policy frameworks, intelligent technical tools, and international interface standards. This trend will not only contribute to the robust development of the stablecoin ecosystem itself, but also provide a new model for compliance cooperation in the global financial market.
VI. Summary
Stablecoins, as a key component of the cryptoasset ecosystem, were originally designed to provide a digital payment tool with relatively stable prices and cross-border circulation. However, in practice, they also introduce complex AML/CFT risks. This report examines the background and definition, risk landscape, technical monitoring methods, compliance implementation paths, and future trends. It argues that stablecoin AML/CFT compliance is not a single-dimensional technical issue, but rather a systematic project requiring a combination of technology, institutions, and cross-border collaboration. Dynamic regulatory policies and proactive compliance exploration by the industry are driving the maturity of relevant practices. The in-depth application of technologies such as AI and graph analytics has the potential to enhance the flexibility and intelligence of compliance systems. Cross-border information sharing and the gradual convergence of international standards are also expected to gradually reduce regulatory arbitrage opportunities, thereby strengthening global risk prevention and control collaboration.
In this process, the establishment of the DAAMC reflects Hong Kong's proactive exploration of stablecoin AML. As the lead author of this report, SlowMist hopes to provide technical references for stablecoin compliance systems in Hong Kong and globally through its research and practical experience, helping the industry find a sustainable balance between regulation and innovation. In the future, the development of stablecoin AML may no longer rely on a single entity, but rather form a dynamic ecosystem collaboratively formed by regulators, industry, and technology. Within this ecosystem, factors such as transparency and privacy protection, innovation and compliance, and efficiency and security will be constantly rebalanced. Through continuous evolution and cross-border collaboration, stablecoins are expected to achieve more sustainable and compliant adoption in the global financial system. This report hopes to be a practical exploration and contribution to this process.
References
1. Financial Action Task Force (FATF). The FATF Recommendations
2. Financial Action Task Force (FATF). Targeted Update on Implementation of the FATF Standards on Virtual Assets and Virtual Asset Service Providers
3. The U.S. Congress.Stablecoin Legislation: An Overview of S. 1582, GENIUS Act of 2025
4. European Union. Markets in Crypto-Assets Regulation (MiCA)
5. MAS. Response to Public Consultation on Proposed Regulatory Approach for Stablecoin-related Activities
6. MAS. Guidelines for MAS Notice FSM‑N27
7. FSA. Examination of the Regulatory Systems Related to Cryptoassets
8. The Korea Herald. The Enforcement Decree of the Virtual Asset User Protection Act Passes the Cabinet Meeting.
9. The U.S. Department of Justice. Garantex cryptocurrency exchange disrupted in international operation
10. The U.S. Department of the Treasury’s Office of Foreign Assets Control. U.S. Treasury Sanctions Notorious Virtual Currency Mixer Tornado Cash
11. 21st Century Business Herald. 6.5 billion yuan in cross-border arbitrage: Exposing illegal virtual currency exchange.
12. Cointelegraph. Tether blocks $12.3M in USDT tied to suspicious Tron addresses
13. The U.S. Department of the Treasury’s Financial Crimes Enforcement Network. FinCEN Finds Cambodia-Based Huione Group to be of Primary Money Laundering Concern, Proposes a Rule to Combat Cyber Scams and Heists
14. Hong Kong Monetary Authority (HKMA). (Stablecoin Regulation)
15. Hong Kong Monetary Authority (HKMA). (Guidelines for the Supervision of Licensed Stablecoin Issuers)
16. Hong Kong Monetary Authority (HKMA). (Guidelines on Combating Money Laundering and Terrorist Financing (Applicable to Licensed Stablecoin Issuers))
17. SlowMist. (Blockchain Crypto Asset Tracking Handbook)
18. SlowMist. (Smart Contract Implementation Guide for Hong Kong Stablecoin Issuers)
About SlowMist
 SlowMist Technology is a threat intelligence company focused on blockchain ecosystem security. Founded in January 2018, it was founded by a team with over a decade of frontline cybersecurity offense and defense experience, including members who have previously built world-class security projects. SlowMist Technology has become a leading international blockchain security company, serving numerous leading and well-known projects globally through its integrated, tailored security solutions, from threat discovery to threat defense. The company has thousands of commercial clients across more than a dozen major countries and regions.
SlowMist Technology is a threat intelligence company focused on blockchain ecosystem security. Founded in January 2018, it was founded by a team with over a decade of frontline cybersecurity offense and defense experience, including members who have previously built world-class security projects. SlowMist Technology has become a leading international blockchain security company, serving numerous leading and well-known projects globally through its integrated, tailored security solutions, from threat discovery to threat defense. The company has thousands of commercial clients across more than a dozen major countries and regions.
SlowMist Technology has actively participated in the promotion of industry, national, and international standards for blockchain security. It was one of the first domestic companies to be recognized by the Ministry of Industry and Information Technology (2018 China Blockchain Industry White Paper) and one of three member companies of the Guangdong-Hong Kong-Macao Greater Bay Area's "Blockchain and Cybersecurity Technology Joint Laboratory." Less than two years after its establishment, SlowMist Technology received National High-Tech Enterprise designation. SlowMist Technology is also one of the first collaborative development partners of the national digital cultural and creative industry governance ecosystem. SlowMist Technology has extensive experience in investigating emerging cryptocurrency crimes, and its research findings have been cited by numerous international organizations and government departments, including but not limited to the UN Security Council and the United Nations Office on Drugs and Crime.
SlowMist Technology's security solutions include security auditing, threat intelligence (BTI), and defense deployment services, complemented by SaaS-based security products such as cryptocurrency anti-money laundering (AML), fraudulent deposit vulnerability scanning, security monitoring (MistEye), hacked archives (SlowMist Hacked), and a smart contract firewall (FireWall.X). Leveraging its proven and effective security services and products, SlowMist Technology collaborates with top international security companies such as Akamai, BitDefender, RC², Tianji Youmeng, and IPIP, as well as renowned cryptocurrency projects domestically and internationally, forensic experts, and public security agencies. SlowMist Technology provides integrated, customized security solutions from threat discovery to threat defense. SlowMist Technology has independently discovered and publicized numerous common, high-risk blockchain security vulnerabilities, garnering widespread industry attention and recognition. Bringing a sense of security to the blockchain ecosystem is SlowMist Technology's mission.


