Author: Kong&Thinking
Editor: Liz
Background
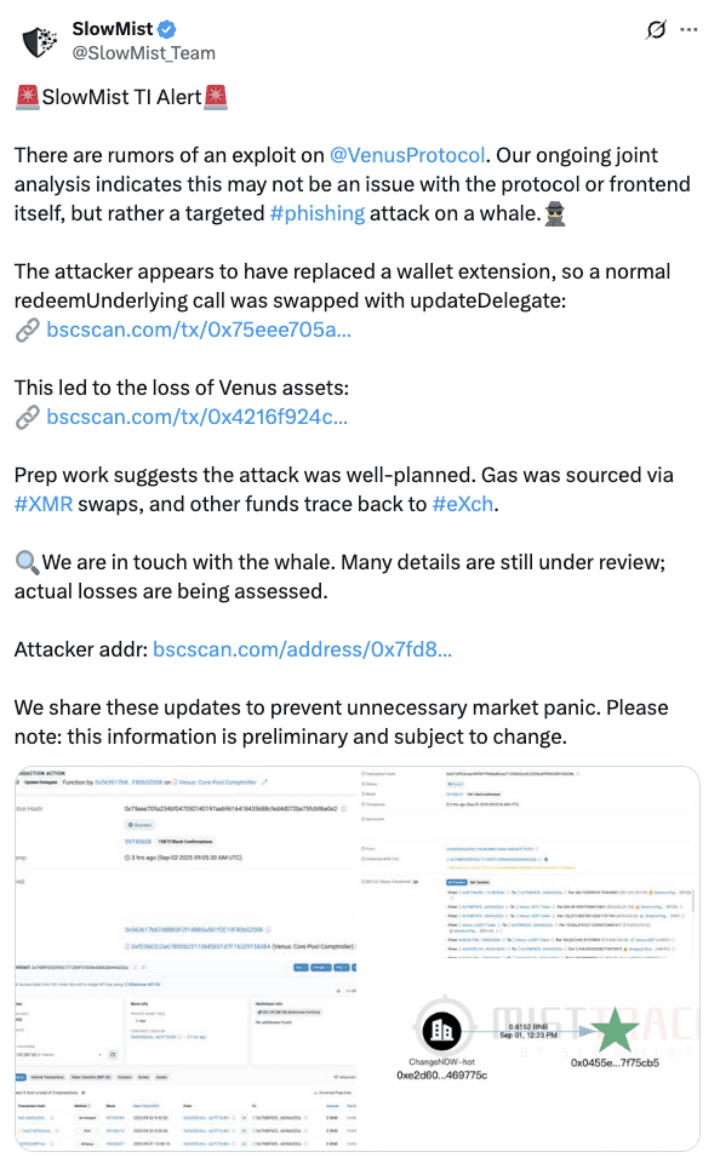
On September 2, 2025, community user @KuanSun1990 encountered an attack, resulting in the transfer of multiple positions on the Venus protocol and a loss of approximately 13 million dollars. SlowMist's independently developed Web3 threat intelligence and dynamic security monitoring tool MistEye successfully captured the anomaly and assisted the user in analysis. Below are the specific analysis details.
 (https://x.com/SlowMist_Team/status/1962854755585429877)
(https://x.com/SlowMist_Team/status/1962854755585429877)
Root Cause
Victimized users mistakenly entered attackers' fraudulent Zoom online meeting links and, under the guidance of that fake website, ran malicious code on their computers, resulting in device control. Due to the deletion of relevant records, the analysis work faces significant challenges. According to the victim's recollection, he was using a well-known official extension wallet at the time and suspected that the attacker had tampered with the extension wallet code on his computer. As a result, the Venus asset redemption operation originally initiated by the user through a hardware wallet was altered to a Venus position delegation operation, ultimately leading to the takeover of his position on Venus by the attacker.
Detailed analysis
The attacker used social engineering tactics, masquerading as a business partner, to lure the target user into a Zoom online meeting and sent the meeting link via Telegram (since relevant chat records have been deleted, the entire process cannot be fully restored). The victim clicked the link and joined the meeting.
At that time, the victim hurriedly entered the meeting due to a schedule conflict with another meeting and did not carefully check whether the browser domain was the official Zoom domain. Meanwhile, the attacker, disguised as a business negotiator, continuously urged the victim in the meeting, causing the victim to fail to discern whether the upgrade prompts on the website contained malicious behavior under the pressing circumstances.
In the end, the victim's computer was controlled by the attacker. For specific details on how the computer was compromised, refer to the complete practice challenge provided in the Web3 phishing drill platform Unphishable (https://unphishable.io/) #NO.0x0036.
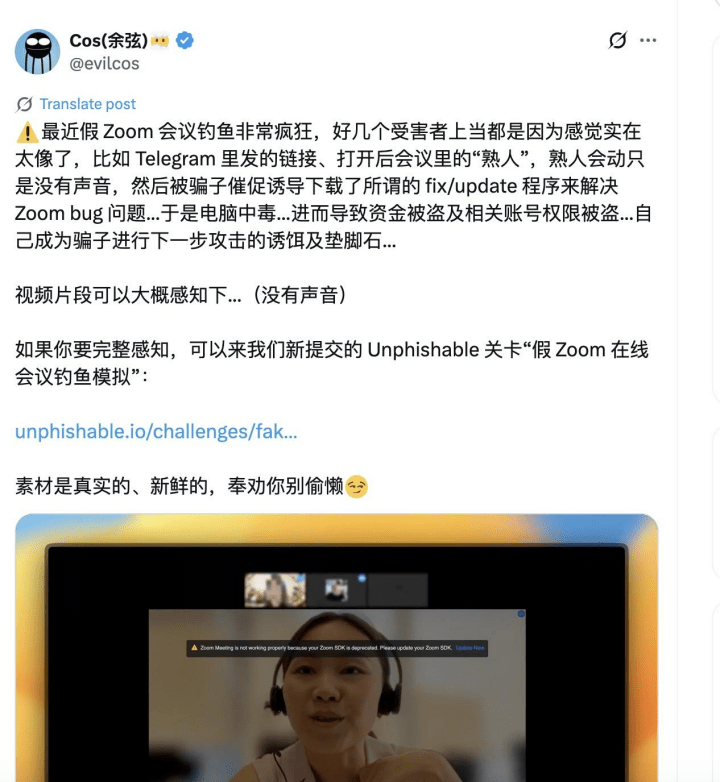 After gaining control of the victim's computer, the attacker modified the wallet code of the browser extension on the victim's computer in some way, allowing them to hijack and replace the original transaction data of the victim. Because the hardware wallet used by the victim lacked a complete 'what you see is what you sign' verification mechanism, it ultimately led to the victim signing a tampered transaction.
After gaining control of the victim's computer, the attacker modified the wallet code of the browser extension on the victim's computer in some way, allowing them to hijack and replace the original transaction data of the victim. Because the hardware wallet used by the victim lacked a complete 'what you see is what you sign' verification mechanism, it ultimately led to the victim signing a tampered transaction.
So how did the attacker modify the code of the browser extension wallet?
We know that Chrome has a set of security mechanisms. If an extension is downloaded from the Chrome store, as long as the code is modified, the browser will prompt that the extension is corrupted and unusable; furthermore, this integrity check cannot be disabled.
Therefore, we once suspected that the attacker might not be modifying the code of a well-known official browser extension wallet but rather adopting other attack methods. Due to the cleaning of many attack traces on the victim's computer, the truth is difficult to fully restore. However, through in-depth research and communication with partners in the threat intelligence network, we confirmed that the browser extension ID used by the attacker to tamper with transactions is consistent with the official extension ID.
Therefore, we began to explore how to maintain the consistency of the browser extension ID with the official one while allowing the code to be modified.
In the case where developer mode is enabled on the browser extension page, one can make an additional copy of the official original extension file and import it into the browser, thus obtaining a new extension that can modify the code while maintaining the same official extension ID. This is because Chrome generates the extension ID based on the key in the manifest.json file. As long as the key in the manifest.json file of the extension is the same as the official one (having the same key is the key to the extension having the same ID), one can modify the code in this new extension (ID consistent with the official one) without triggering the integrity check.
By patching Chrome's function regarding content validation of browser extensions, one can globally disable the content integrity check of the extensions. Of course, on macOS, this part of the operation needs to be re-signed to ensure the program is usable.
The above describes two possible attack methods identified by our research. Currently, there is no more concrete information to support this, so the above methods only represent the internal research and speculation of the Slow Fog security team and do not imply that the attacker actually used these techniques.
Before the attack officially began, the attacker raised approximately 21.18 BTCB and 205,000 XRP using their own funds on September 1, to prepare for taking over the victim user's position in Venus.
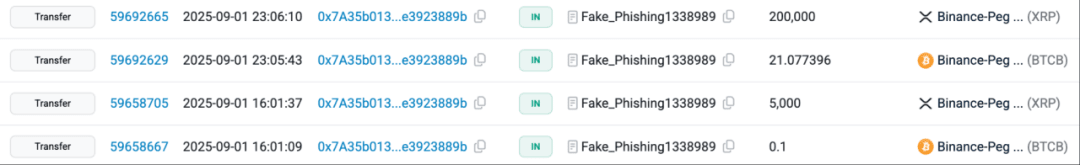 After about 10 hours of waiting, the attacker finally got the opportunity to operate the victim user's wallet. At this point, the victim user connected a hardware wallet to the extension wallet installed on their Chrome browser and accessed the correct Venus official website.
After about 10 hours of waiting, the attacker finally got the opportunity to operate the victim user's wallet. At this point, the victim user connected a hardware wallet to the extension wallet installed on their Chrome browser and accessed the correct Venus official website.
Subsequently, the victim user prepared to redeem their USDT tokens on Venus. At this time, the victim user called the correct redeemUnderlying function. However, due to the tampering of the extension wallet, the operation sent to the hardware wallet for signature was replaced with an updateDelegate operation. The victim's hardware wallet does not support detailed signature data parsing and has enabled blind signing, which led the victim user to sign the updateDelegate operation without any defense and submit the transaction through the extension wallet. Ultimately, their Venus position was delegated to the attacker for management.
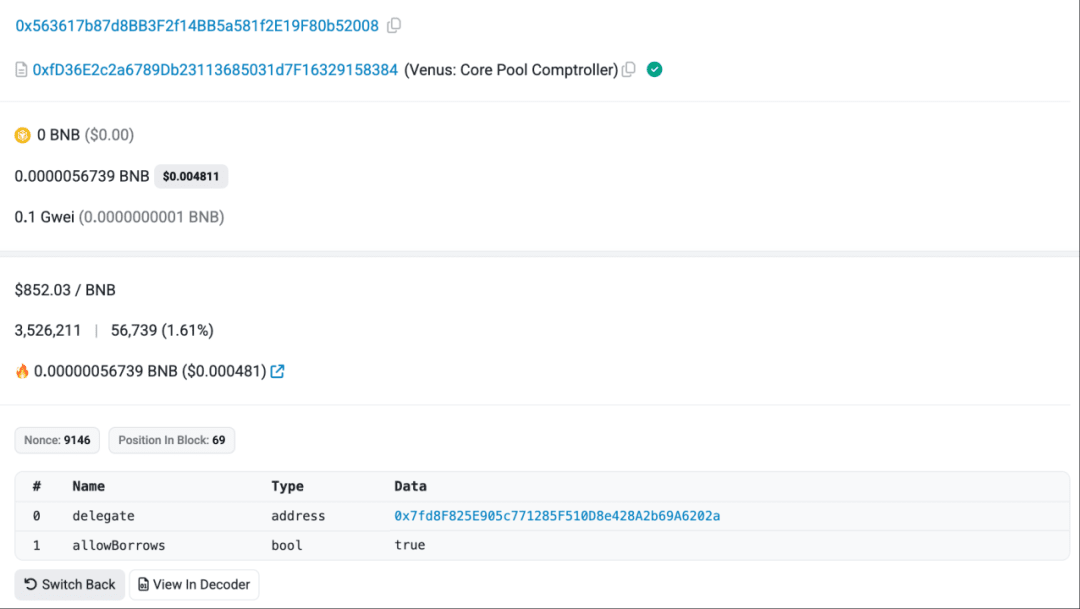 (https://bscscan.com/tx/0x75eee705a234bf047050140197aeb9616418435688cfed4d072be75fcb9be0e2)
(https://bscscan.com/tx/0x75eee705a234bf047050140197aeb9616418435688cfed4d072be75fcb9be0e2)
After the victim user completed the delegation, the attacker immediately launched an attack, borrowing about 285 BTCB through Lista flash loans, and using their own 21.18 BTCB and 205,000 XRP. Subsequently, the attacker repaid the victim user approximately 306.89 BTCB and 152,673.96 XRP in loans on Venus.
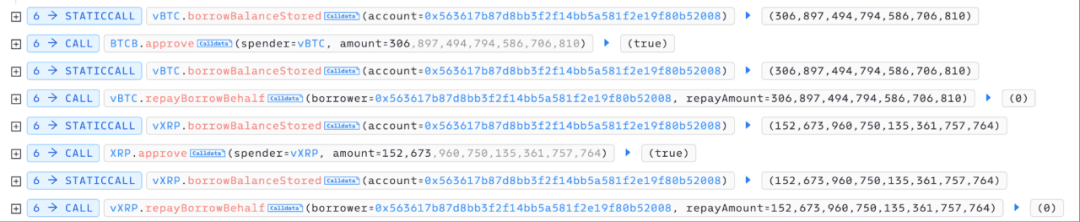 After completing the repayment for the victim user, the attacker immediately redeemed the victim user's collateral (USDT/USDC/WBETH/FDUSD/ETH) in Venus to an address under their control.
After completing the repayment for the victim user, the attacker immediately redeemed the victim user's collateral (USDT/USDC/WBETH/FDUSD/ETH) in Venus to an address under their control.
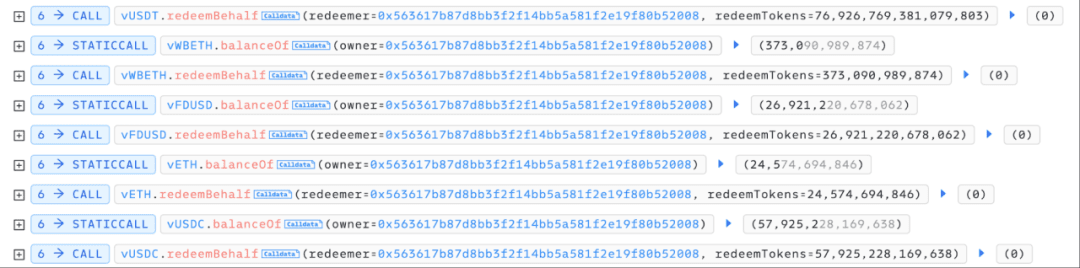 At this point, the attacker had completed the transfer of the victim user's position on Venus, and now only needed to repay about 285 BTCB borrowed from the Lista flash loan to realize profits. Since directly exchanging the collateral (USDT/USDC/WBETH/FDUSD/ETH) held by the attacker for BTCB in DEX is not cost-effective and may cause significant slippage, the attacker chose to redeposit these collaterals into Venus and borrow BTCB to repay the flash loan.
At this point, the attacker had completed the transfer of the victim user's position on Venus, and now only needed to repay about 285 BTCB borrowed from the Lista flash loan to realize profits. Since directly exchanging the collateral (USDT/USDC/WBETH/FDUSD/ETH) held by the attacker for BTCB in DEX is not cost-effective and may cause significant slippage, the attacker chose to redeposit these collaterals into Venus and borrow BTCB to repay the flash loan.
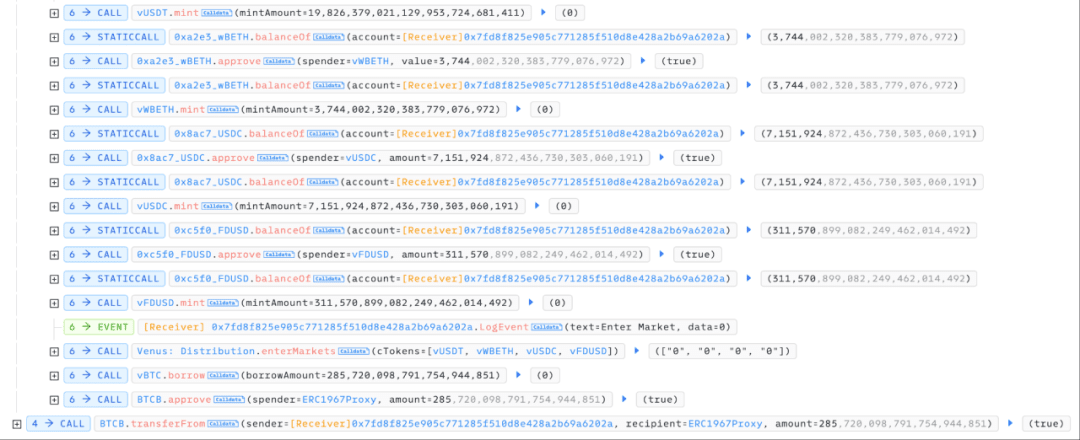 After completing the flash loan repayment, the attacker successfully took over the victim user's Venus position, which was initially a cleverly executed phishing attack case. However, while the attacker held the Venus position and had not taken further action, the Venus team reacted quickly, immediately pausing the protocol and later suspending all market EXIT_MARKET operations.
After completing the flash loan repayment, the attacker successfully took over the victim user's Venus position, which was initially a cleverly executed phishing attack case. However, while the attacker held the Venus position and had not taken further action, the Venus team reacted quickly, immediately pausing the protocol and later suspending all market EXIT_MARKET operations.
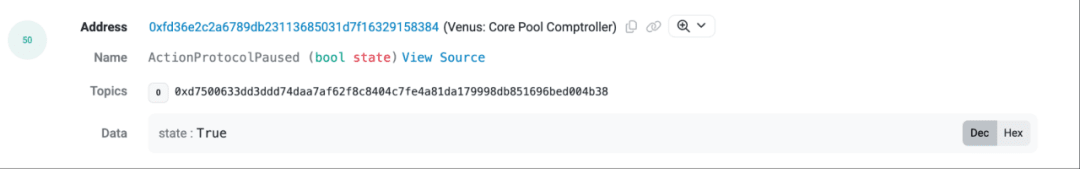 (https://bscscan.com/tx/0xe4a66f370ef2bc098d5f6bf2a532179eea400e00e4be8ea5654fa9e8aeee65bf#eventlog)
(https://bscscan.com/tx/0xe4a66f370ef2bc098d5f6bf2a532179eea400e00e4be8ea5654fa9e8aeee65bf#eventlog)
This measure blocked the attacker from further operating their position to gain profits. Subsequently, the Venus team initiated an emergency proposal vote to ensure the safety of the protocol's recovery while attempting to recover the user's stolen funds.
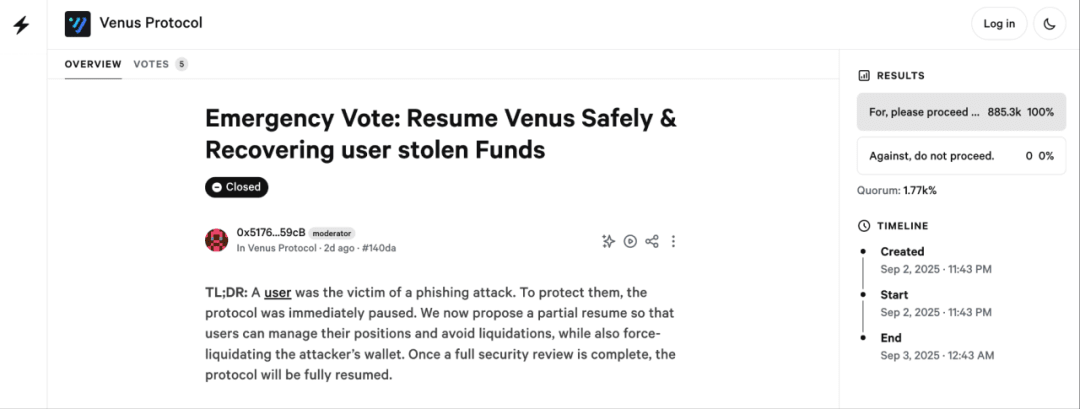 (https://snapshot.box/#/s:venus-xvs.eth/proposal/0x140da3dcb6dc711429700443d3b9f1def51eaae3b791f8b774664676f418a132)
(https://snapshot.box/#/s:venus-xvs.eth/proposal/0x140da3dcb6dc711429700443d3b9f1def51eaae3b791f8b774664676f418a132)
Ultimately, the Venus team recovered the stolen funds for the victim user by forcibly liquidating the attacker's position.
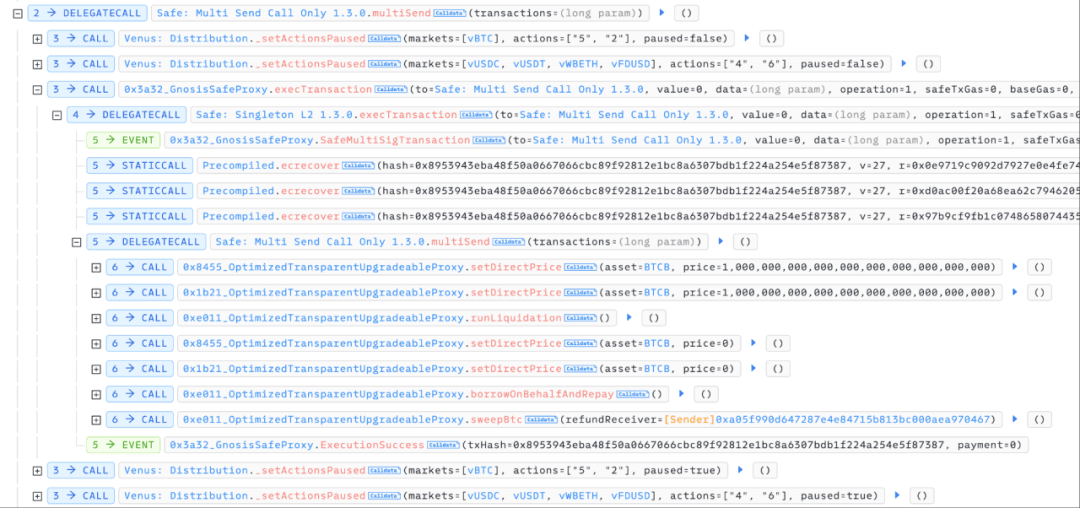 (https://bscscan.com/tx/0xee9928b8d1a212f4d7b7e9dca97598394005a7b8fef56856e52351bc7921be43)
(https://bscscan.com/tx/0xee9928b8d1a212f4d7b7e9dca97598394005a7b8fef56856e52351bc7921be43)
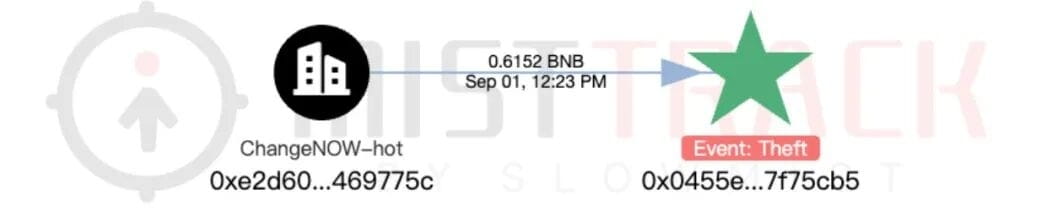
In addition, according to the analysis by the on-chain anti-money laundering tracking tool MistTrack, addresses associated with the attacker had withdrawn funds from ChangeNOW:
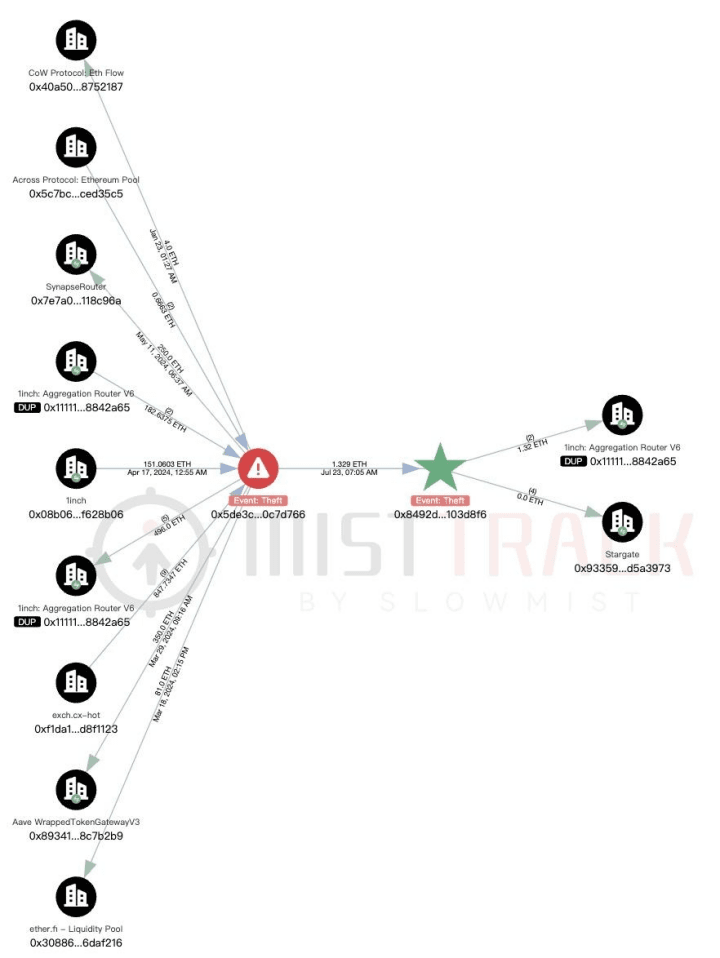
 Other related addresses had interacted with multiple exchange platforms (such as 1inch), cross-chain platforms (such as Across Protocol), and sanctioned exchanges (such as eXch):
Other related addresses had interacted with multiple exchange platforms (such as 1inch), cross-chain platforms (such as Across Protocol), and sanctioned exchanges (such as eXch):
 Summary
Summary
This incident is a carefully planned phishing attack. The attacker controlled the user's device through a malicious Zoom client and exploited the features of Chrome Developer Mode to tamper with the wallet extension, cleverly replacing the user's asset redemption operation with a position delegation operation, using extremely sophisticated methods. Fortunately, the Venus team demonstrated excellent emergency response capabilities, ultimately helping the user mitigate risks through collaborative and rapid response, avoiding potential massive losses.






