Recently, the cryptocurrency exchange BTCTurk announced that it was hacked, with over $48 million in funds flowing out abnormally from multiple on-chain hot wallets. The Beosin security team analyzed this incident and tracked the funds, sharing the results as follows:
The following hot wallet addresses have been found to have transferred funds:
0xde2faca4bbc0aca08ff04d387c39b6f6325bf82a
0x2cea0297bfb1b55ff37126b677d78e2b1fd2e856
0xb5a46bc8b76fd2825aeb43db9c9e89e89158ecde
Involving chains such as Bitcoin, Ethereum (ETH), Avalanche (AVAX), Arbitrum (ARB), Base (BASE), Optimism (OP), and Polygon (POL).
Currently detected related hacker transit addresses are as follows:
0xa041feb3a8297c5689fee180083164a061a17fd6
0xb4b537626e21df5386cf167d1e654b38785056cc
0x7d91d1ebeba91257733a523409125aedac5d8b6e
The hacker's sedimentation addresses are as follows:
0x0fe41fe8786329fb6bd8f2baa73aa55e770f0951
0x95ab53305bc71d0e6e2d46f2e62690599cbc87fc
0xddfa0884f32d0d210597a996060fbdb5b068b0ea
bc1q3xgyvmfk6mw6zvhjklsw7v8wl2dk0xtm35ulut
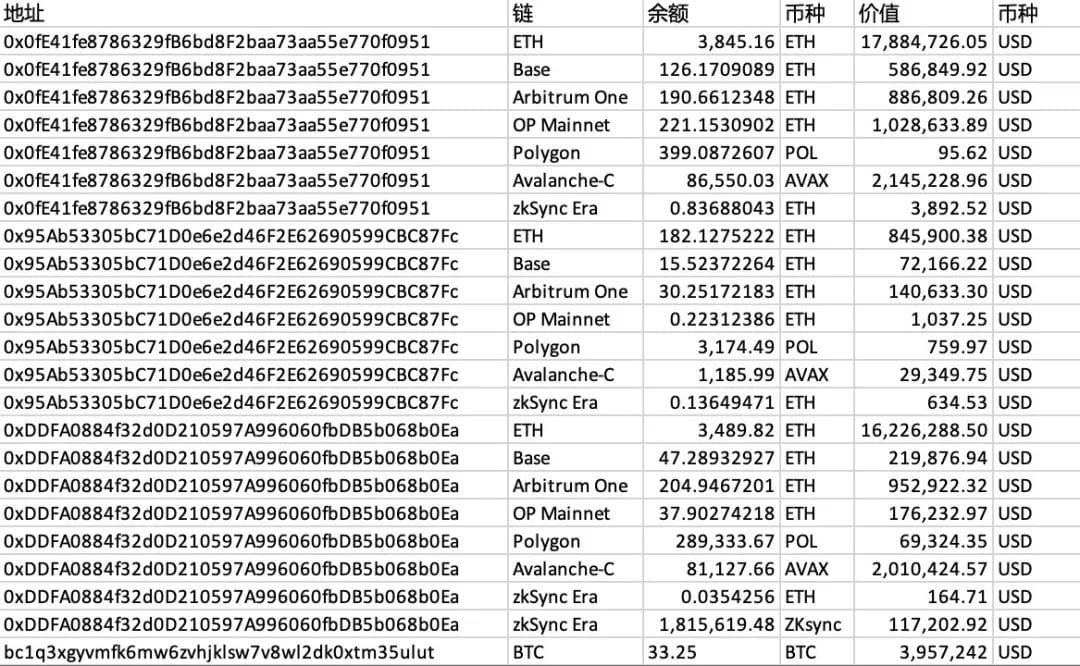
Using the Beosin Trace tool to track the stolen funds, the following flow charts of the main stolen funds on the EVM and Bitcoin chains can be obtained:
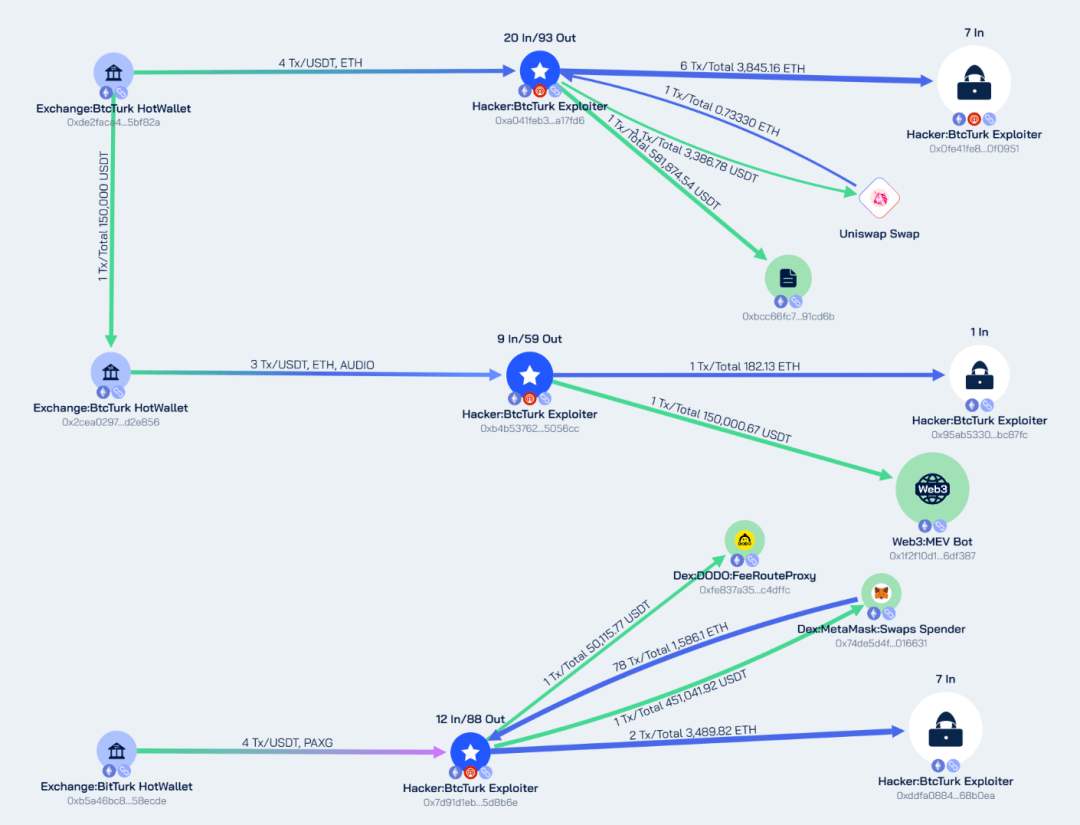
Beosin Trace EVM chain fund analysis chart
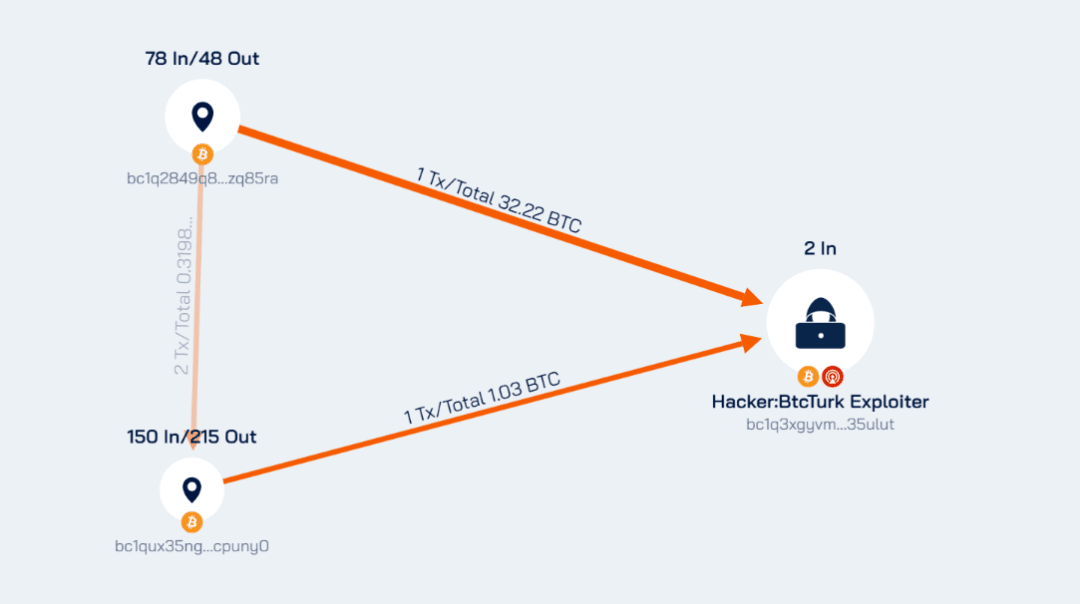
Beosin Trace Bitcoin chain fund analysis chart
Currently, the reason for the attack on BTCTurk's hot wallet has not been disclosed. Multiple aspects need to be investigated for evidence, including the internal operational security of the exchange, the security of signing devices, mnemonic management, and the security of the signing environment. Similar security incidents at exchanges have occurred multiple times before.
Exchange security remains a significant challenge in the Web3 ecosystem, requiring continuous efforts and cooperation from exchanges, security companies, regulatory and law enforcement agencies. Beosin Trace has added the hacker-related addresses from this incident to the blacklist and will continue to track them.



