Written by: Chainalysis
Compiled by: AididiaoJP, Foresight News
Core Findings
Stolen funds
From 2025 to date, cryptocurrency services have suffered over $2.17 billion in fund theft, a figure far exceeding the total for all of 2024. Among these, North Korea's $1.5 billion hack of ByBit (the largest single theft in cryptocurrency history) accounts for the majority of the losses.
As of the end of June 2025, the total amount of stolen funds is 17% higher than that of the worst year previously, 2022. If current trends continue, funds stolen from service platforms may exceed $4 billion by the end of the year.
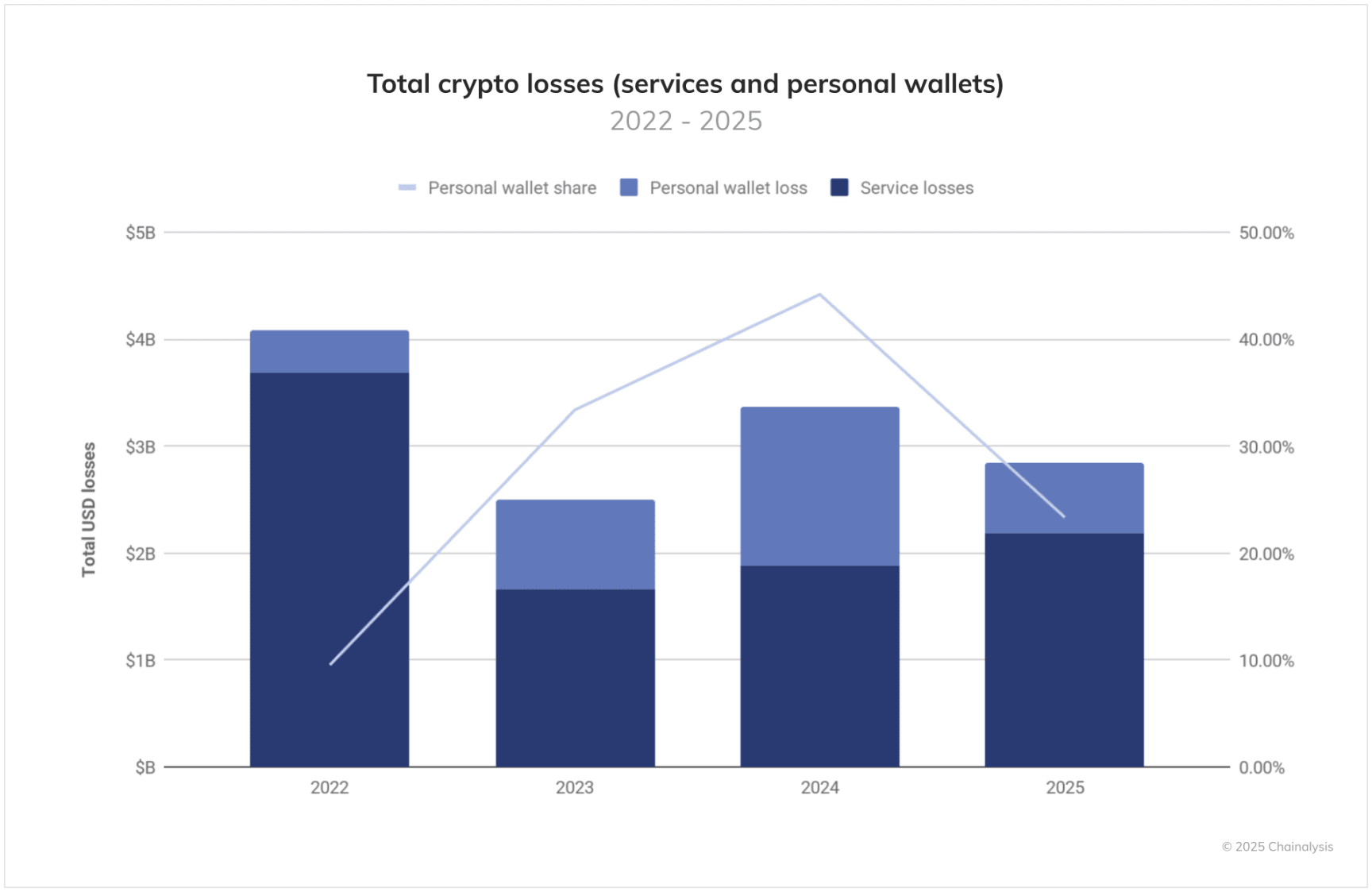
The proportion of personal wallets stolen in the overall ecosystem theft is gradually rising, with attackers increasingly targeting individual users. From 2025 to date, such cases account for 23.35% of all stolen funds activities.
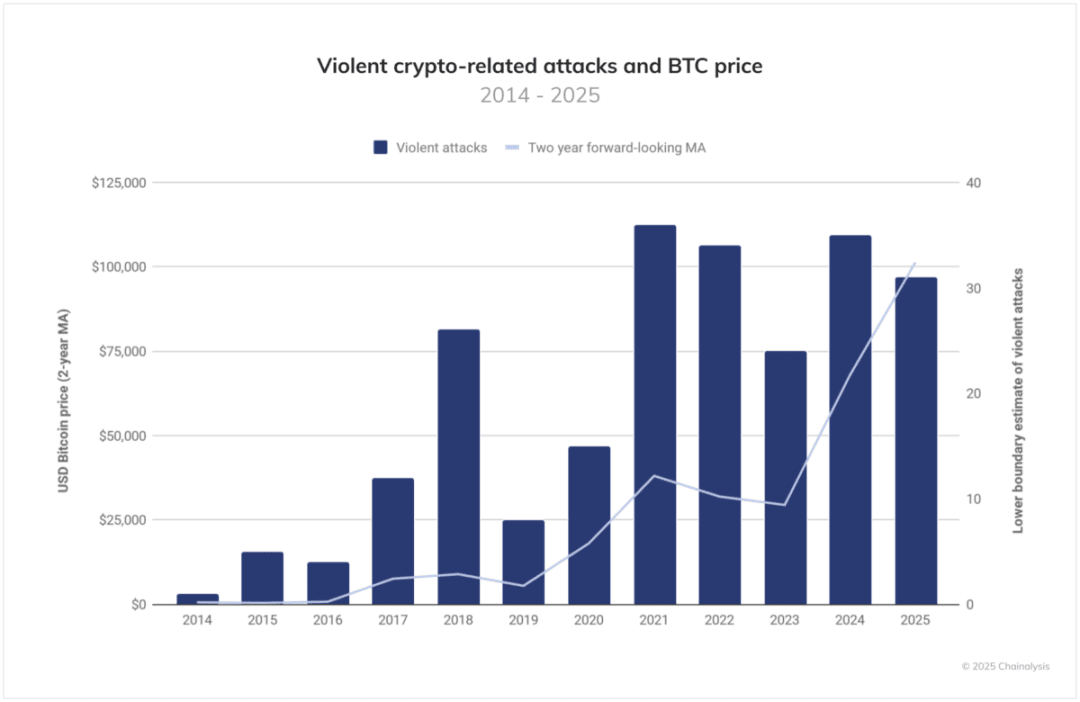
‘Wrench attacks’ (violent or coercive actions against cryptocurrency holders) correlate with Bitcoin price fluctuations, indicating that attackers are more likely to strike during periods of high asset value.
Regional Trends
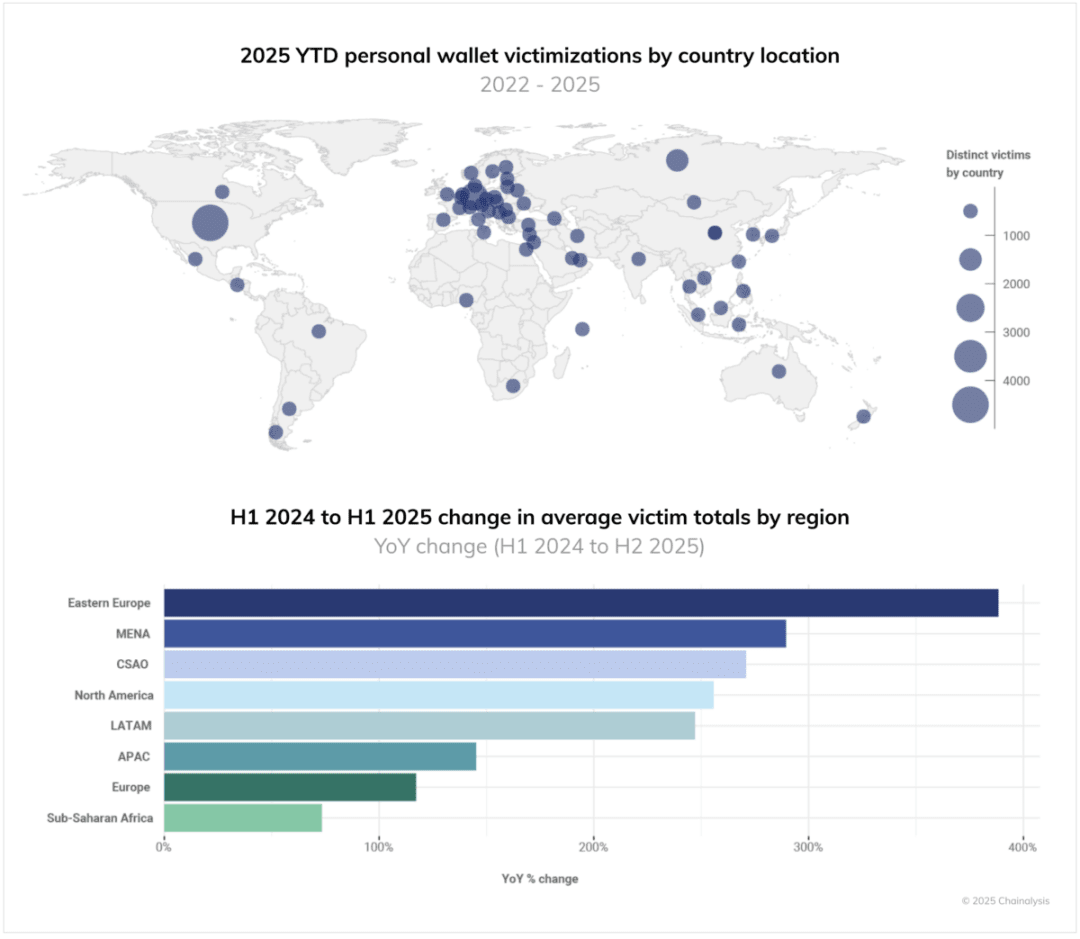
From 2025 to date, the United States, Germany, Russia, Canada, Japan, Indonesia, and South Korea have become concentrated areas of victims.
Regionally, Eastern Europe, the Middle East and North Africa, as well as Central Asia and South Asia, have seen the fastest growth in the number of victims from the first half of 2024 to the first half of 2025.
There are significant differences in the types of stolen assets by region, which may reflect the fundamental patterns of cryptocurrency adoption locally.
Money Laundering Behavior
There are differences in money laundering behaviors between thefts from service platforms and personal wallets. Overall, threat actors targeting service platforms typically exhibit higher technical complexity.
Money launderers often pay excessive fees to transfer funds, with average premiums fluctuating from 2.58 times in 2021 to 14.5 times from 2025 to date.
Interestingly, while the average dollar cost of transferring stolen funds has decreased over time, the multiples of on-chain average costs have increased.
Attackers targeting personal wallets tend to keep a large amount of stolen funds on-chain rather than laundering it immediately.
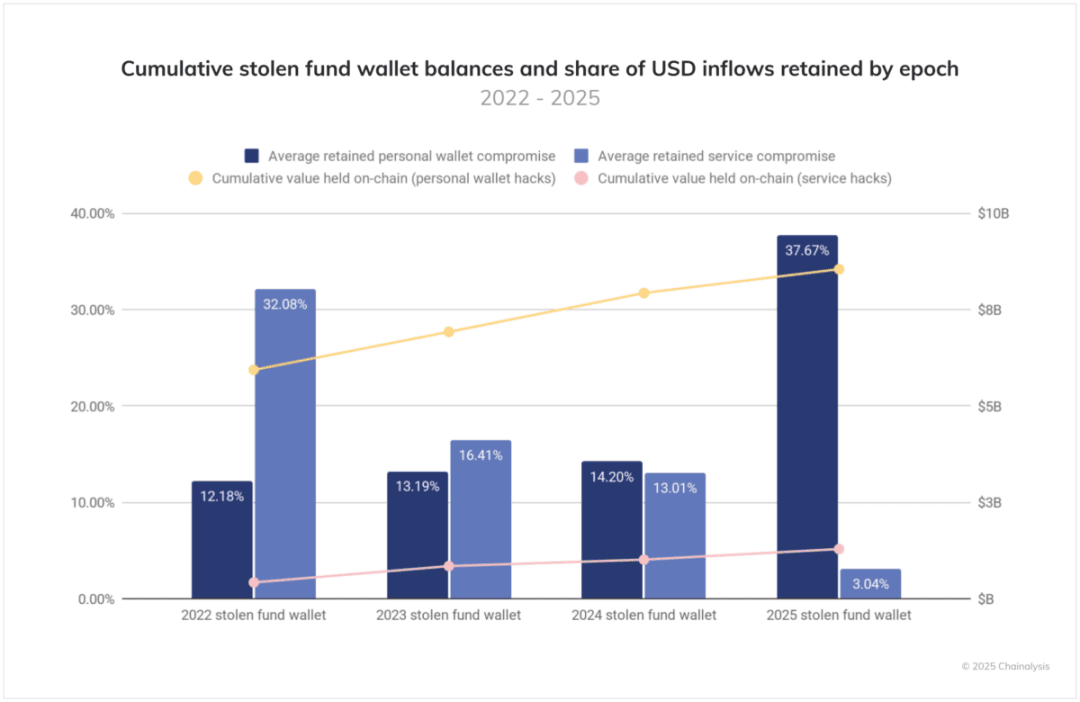
Currently, there are still $8.5 billion in cryptocurrency from thefts targeting personal wallets remaining on-chain, while funds stolen from service endpoints total $1.28 billion.
Changes in the environment of illegal activities
Despite significant changes in the cryptocurrency environment, the illegal transaction volume from 2025 to date is still expected to reach or exceed last year's estimated $51 billion. The closure of the sanctioned Russian exchange Garantex, as well as the potential designation of the Cambodian Chinese service provider Huione Group (which handles over $70 billion in inflows) as a special focus by the US Financial Crimes Enforcement Network (FinCEN), have reshaped how criminals move funds in the ecosystem.
In this changing situation, fund theft has become the primary issue of 2025. Other forms of illegal activities show mixed performances year-on-year, while the surge in cryptocurrency theft not only poses a direct threat to ecosystem participants but also presents long-term challenges to industry security infrastructure.
Funds stolen from service platforms: currently surging
The cumulative trend of funds stolen from service platforms paints a grim picture of the threat environment in 2025. The orange line representing activities from 2025 to date has risen at an unprecedented rate before June, having already surpassed $2 billion in the first half of the year.
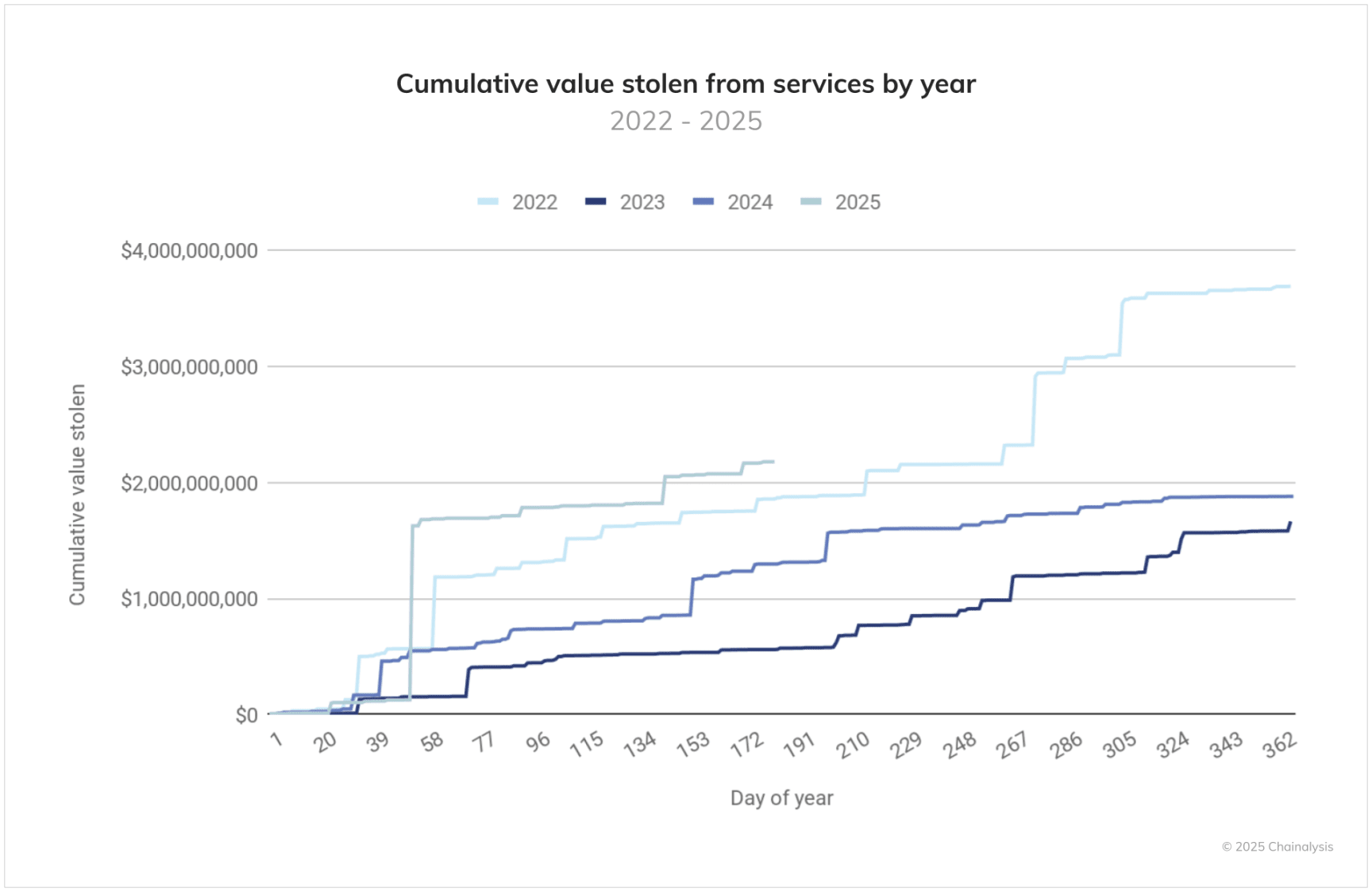
The remarkable aspect of this trend is its speed and persistence. The previous worst incident in 2022, where $2 billion was stolen from a service platform, took 214 days, while a similar scale was achieved in just 142 days in 2025. The trend lines for 2023 and 2024 show a more moderate accumulation pattern.
Currently, data from the end of June 2025 shows a 17.27% increase compared to the same period in 2022. If the trend continues, the amount stolen from service platforms alone in 2025 may exceed $4.3 billion.
The ByBit Incident: A New Benchmark for Cybercrime
North Korea's hack of ByBit has fundamentally altered the threat landscape of 2025. This $1.5 billion single incident is not only the largest cryptocurrency theft in history but also accounts for about 69% of the funds stolen from service platforms this year. Its technical complexity and scale highlight the continuous escalation of state-supported hackers in the cryptocurrency space and mark a strong return after a brief lull in the second half of 2024.
This super attack aligns with North Korea's overall cryptocurrency operations, which have become a core part of the country's sanctions evasion strategy. Known losses related to North Korea reached $1.3 billion last year (the previously worst year), while 2025 has already far exceeded this record.
The attack methods are suspected to utilize advanced social engineering techniques (such as infiltrating IT personnel related to cryptocurrency services), similar to past North Korean operations. According to the latest UN report, Western tech companies have inadvertently employed thousands of North Korean employees, highlighting the destructive capability of such tactics.
Personal Wallets: The Overlooked Frontier of Cryptocurrency Crime
Chainalysis has developed new methods to identify and track theft activities originating from personal wallets. This type of illegal activity has a low reporting rate, but its importance is increasingly prominent. Enhanced visualizations reveal how attackers have diversified their targets and tactics over time.
As shown in the figure below, the proportion of stolen personal wallets in total losses continues to grow. This trend may reflect the following factors:
Improvements in mainstream service security measures have forced attackers to turn to what are perceived as easier personal targets.
The number of individual cryptocurrency holders is increasing.
As mainstream crypto assets appreciate, the value of funds within personal wallets is rising.
More complex individual-targeted techniques are developing (possibly benefiting from easily deployable LLM AI tools).
Analyzing the stolen value from personal wallets by asset type (see figure below) reveals three key trends:
Bitcoin theft occupies a significant proportion.
The average loss amount for personal wallets storing Bitcoin has increased over time, indicating that attackers deliberately target high-value objectives.
The number of individual victims on non-Bitcoin and non-EVM chains (like Solana) is on the rise.
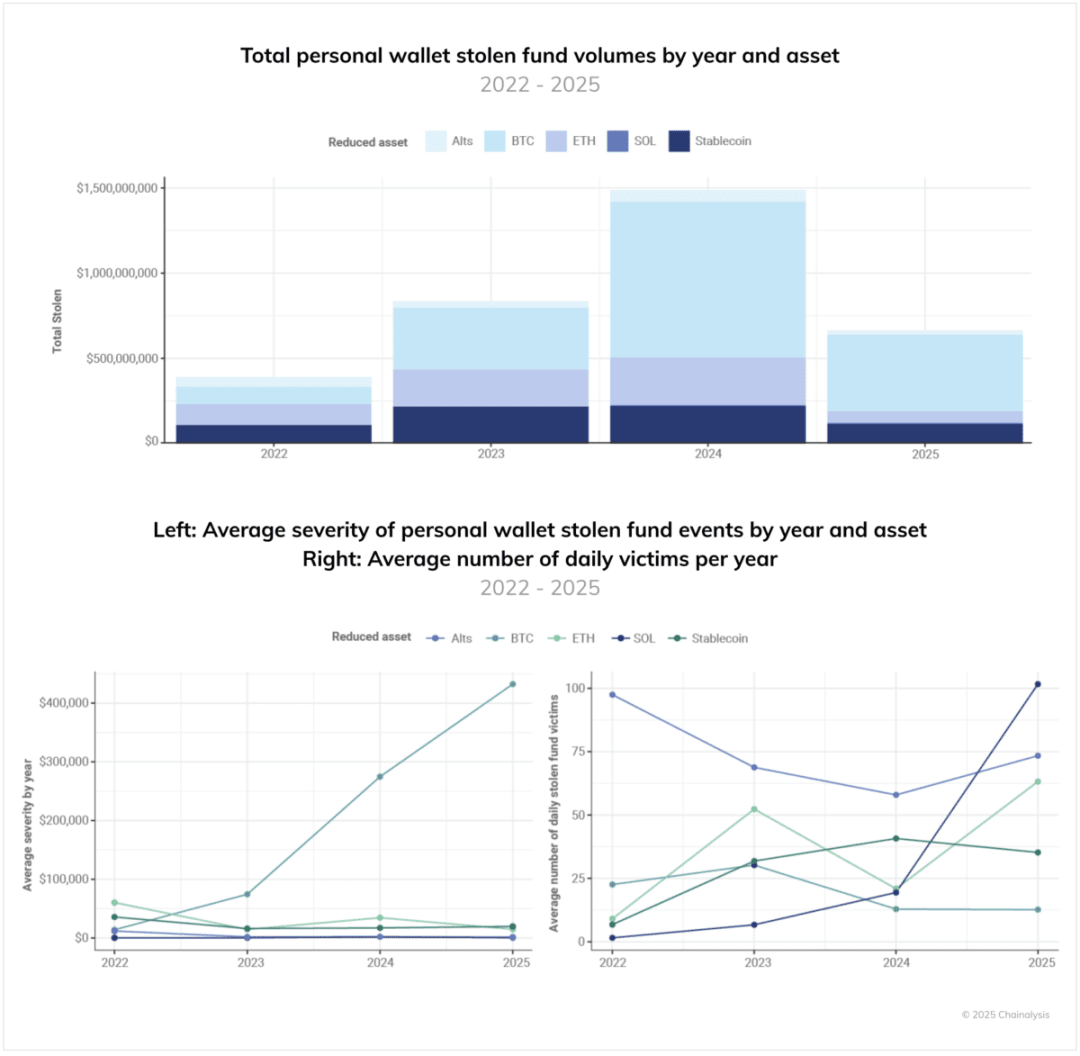
These factors indicate that while Bitcoin holders are less likely to become targets of targeted theft compared to holders of other on-chain assets, once victimized, their loss amounts are exceptionally large. The forward-looking inference is that if the value of native assets rises, the amounts stolen from personal wallets are likely to increase in tandem.
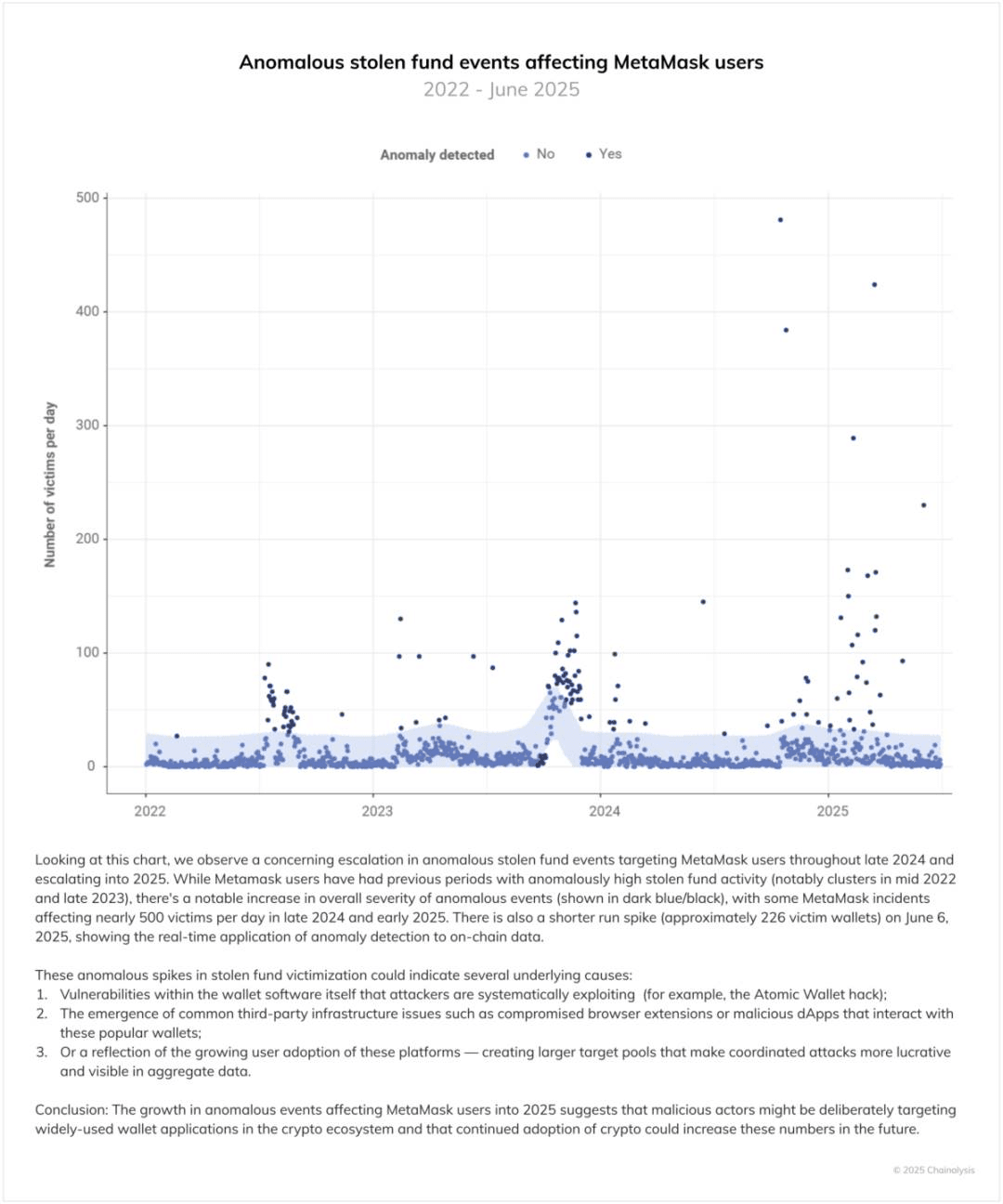
Violent Factors: When Digital Crimes Turn into Physical Harm
One disturbing example in personal wallet thefts is the 'wrench attack,' where attackers obtain the victim's cryptocurrency through violence or coercion. The figure below indicates that the number of such physical attacks in 2025 is expected to reach twice that of the second-highest year in history. It is important to note that, as many cases go unreported, the actual numbers may be even higher.
These violent incidents show a significant correlation with the moving average of Bitcoin prices, indicating that rising asset values (or expected increases) may provoke physical attacks against known cryptocurrency holders. Although such violent cases are relatively rare, their nature of personal injury (including disability, kidnapping, and murder) elevates the social impact of these cases to an extraordinary level. The following cases will illustrate this specifically.
(Source: Jameson Lopp GitHub)
Case Study: How Blockchain Analysis Aided the Resolution of a High-Profile Kidnapping Case in the Philippines
Violent crimes involving money laundering through cryptocurrency present complex challenges for investigations, often requiring sophisticated analytical methods. A recent high-profile case in the Philippines demonstrated how blockchain analysis can provide critical clues, even in the most severe criminal investigations.
In March 2024, the kidnapping and murder of Elison Steel CEO Anson Que shocked the Philippine business community. On March 29, Que and his driver Armanie Pabillo were kidnapped in Bulacan province and later found dead in Rizal province, with obvious signs of abuse. Initially thought to be a 20 million peso kidnapping case, investigations revealed that the victim's family actually paid about 200 million pesos in ransom for Que's release.
The Philippine National Police (PNP) accused casino intermediary companies 9 Dynasty Group and White Horse Club of orchestrating complex money laundering operations: converting ransom originally paid in pesos and dollars into cryptocurrency through electronic wallets designed for casinos, shell accounts, and digital assets to obscure the flow of funds.
Through the Chainalysis Reactor tool, global service teams collaborated with PNP investigators to trace ransom flows. Blockchain analysis revealed how the ransom was aggregated through a series of intermediary addresses and further laundered through more intermediary addresses. With the assistance of the PNP, Chainalysis notified Tether and successfully froze a portion of the USDT funds.
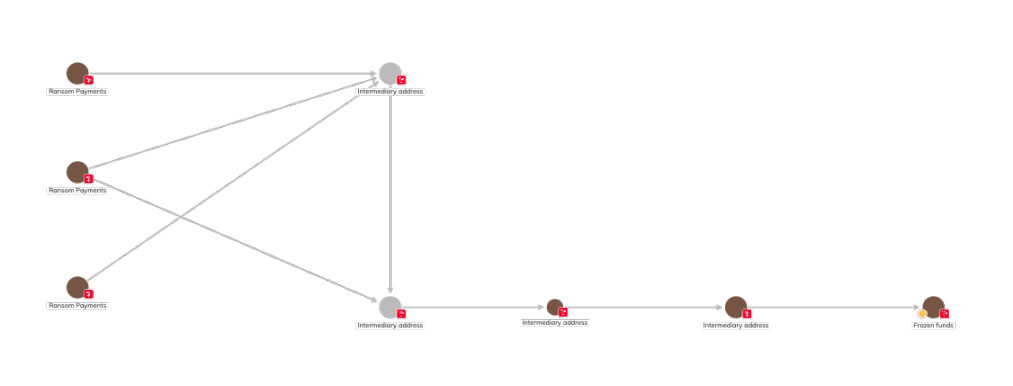
It is noteworthy that the money laundering methods in this case are relatively crude, consistent with the models of criminal groups that adopt cryptocurrencies for their speed and 'anonymity' but lack the professional technology. Unlike traditional financial investigations where evidence is scattered across various institutions, blockchain provides a single, authoritative, and immutable ledger that allows investigators to track fund flows in real-time, map networks, and generate cross-border leads.
The tragedy of Anson Que and Armanie Pabillo reminds us of the real human cost behind these crimes. However, this case also demonstrates that the immutability of blockchain technology can serve as a powerful tool for justice, ensuring that exploiters cannot easily hide in the shadows of the network.
Regional Patterns: Global Victim Distribution
By combining Chainalysis geolocation data with reports of stolen funds, the global distribution of personal wallet victim events can be estimated. Note: This data only includes personal wallet theft events with reliable geolocation information and does not provide a complete view of global theft activities in 2025.
From 2025 to date, the United States, Germany, Russia, Canada, Japan, Indonesia, and South Korea rank as the countries with the highest number of victims per capita; meanwhile, the total number of victims in Eastern Europe, the Middle East, North Africa, Central Asia, and South Asia grew the fastest from the first half of 2024 to the first half of 2025.
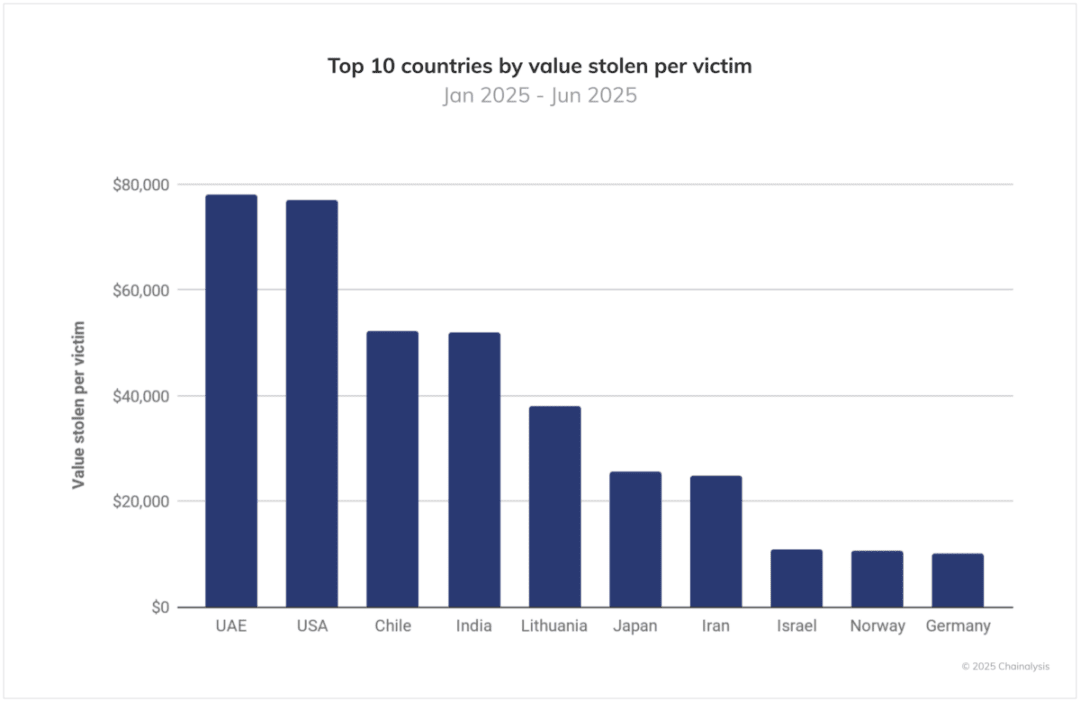
If ranked by per capita stolen amounts (see figure below), the United States, Japan, and Germany still rank among the top ten, but the severity of victims in the UAE, Chile, India, Lithuania, Iran, Israel, and Norway leads globally.
Regional Differences in Stolen Assets from Personal Wallets
Data from 2025 shows that cryptocurrency theft exhibits a regional concentration pattern. The figure below summarizes the total value stolen in various regions by asset type.
North America ranks first in both Bitcoin and altcoin thefts, possibly reflecting the high cryptocurrency adoption rate in the region and the activity of professional attackers targeting large personal assets. Europe is the global center for Ethereum and stablecoin thefts, which may indicate a high adoption rate of these assets locally or attackers' preferences for highly liquid assets.
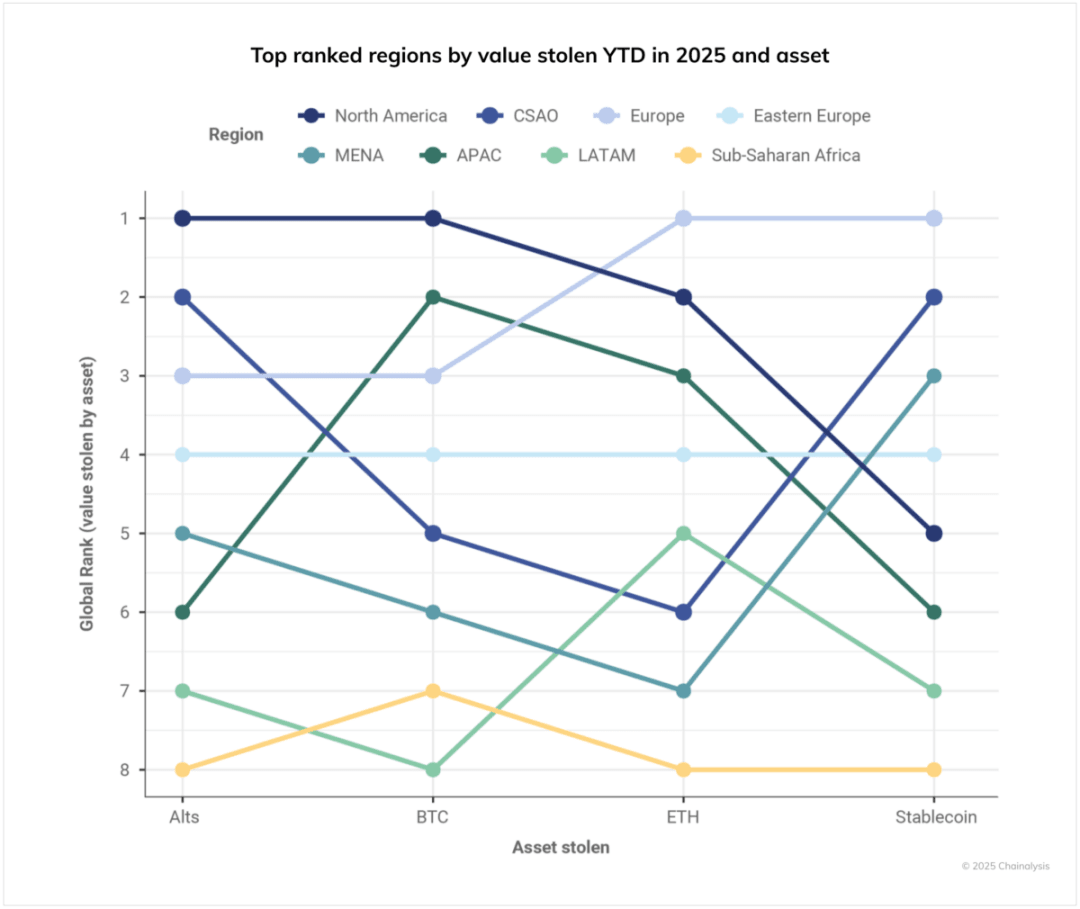
The Asia-Pacific region ranks second in the total amount of stolen Bitcoin, with Ethereum in third place; Central Asia and South Asia rank second in the amount stolen from altcoins and stablecoins. Sub-Saharan Africa ranks last in terms of stolen amounts (with Bitcoin theft ranks second to last), which is more likely to reflect lower wealth levels in the region rather than a lower victimization rate among cryptocurrency users.
Cryptocurrency Money Laundering Economics
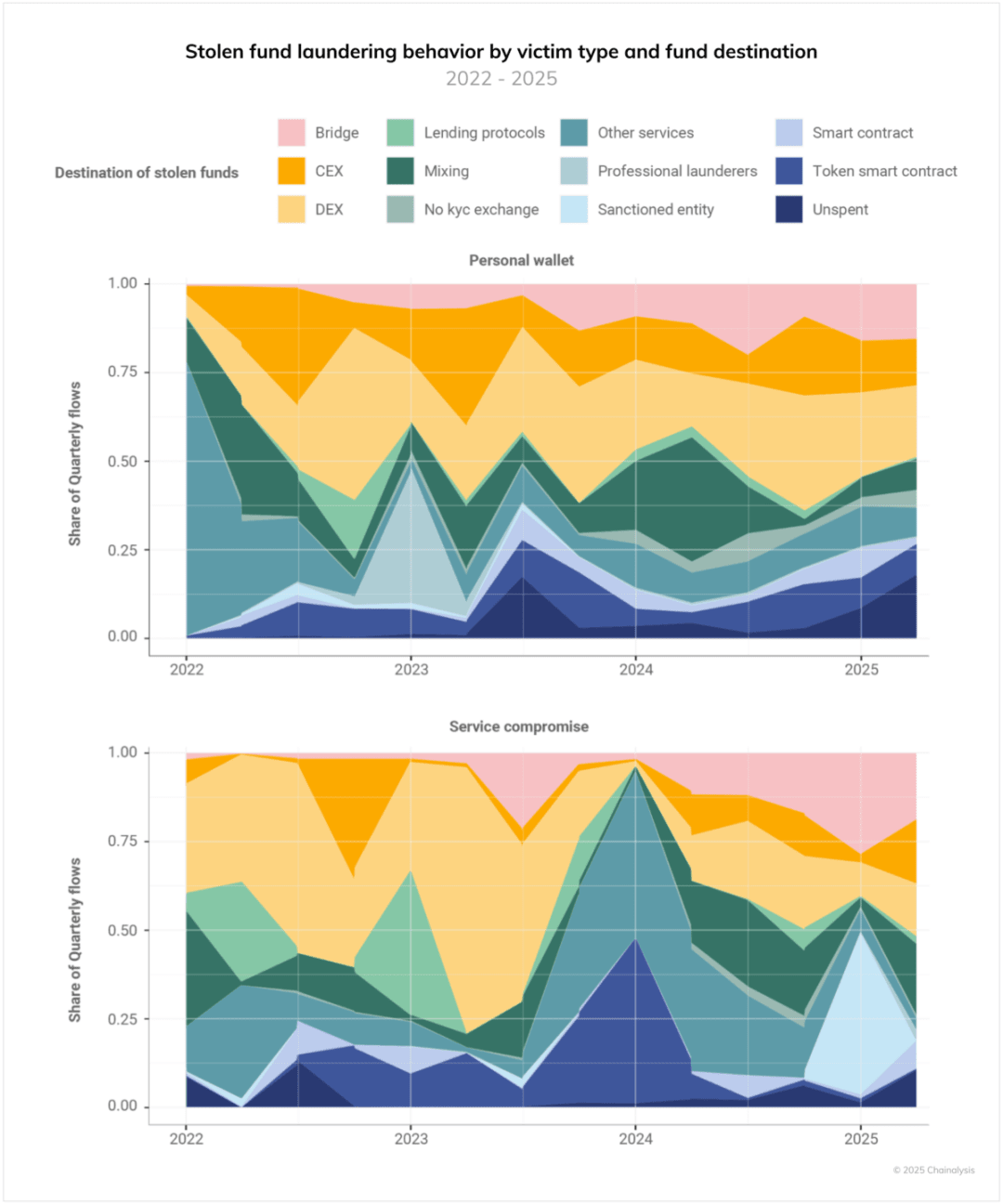
Understanding how stolen funds flow within the crypto ecosystem is crucial for prevention and law enforcement. Analysis shows that money laundering behaviors from personal wallets and service endpoint attacks exhibit significant differences, reflecting varying risk preferences and operational needs.
For example, from 2024 to 2025, attackers targeting servers extensively utilized cross-chain bridges for 'chain hopping' money laundering, and the use of mixers became more frequent. In contrast, funds stolen from personal wallets are more likely to flow into token smart contracts (potentially involving exchanges), sanctioned entities (especially Garantex, or indicating connections to Russian perpetrators), and centralized exchanges (CEXs), indicating relatively crude money laundering techniques.
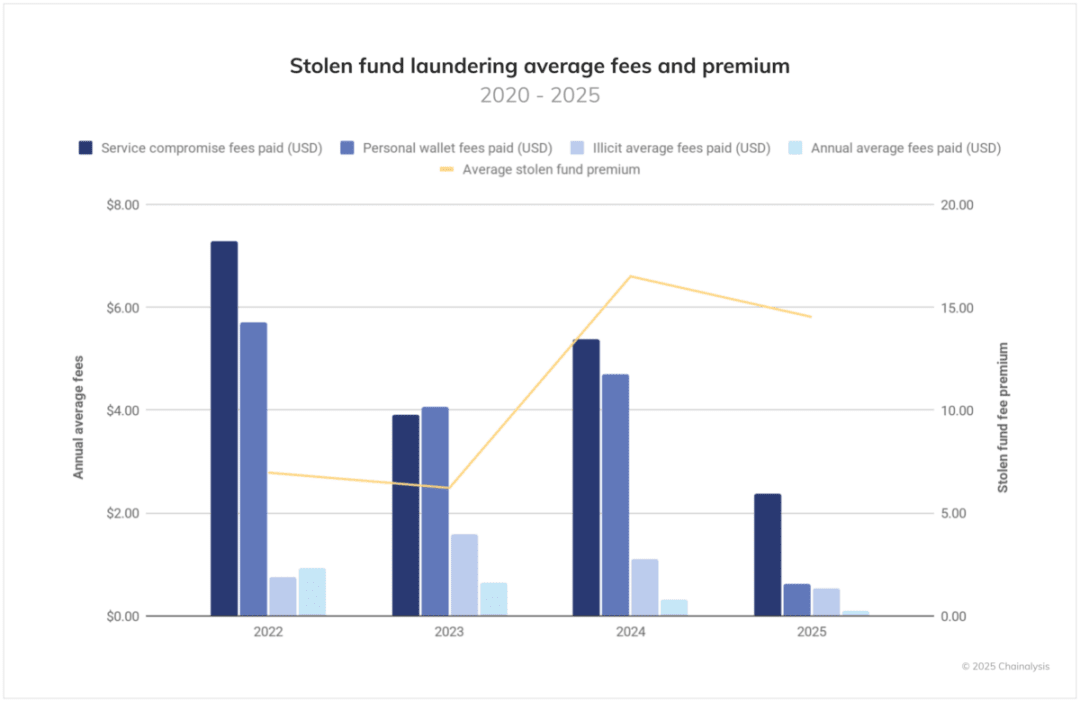
In the money laundering process, operators of stolen funds pay excessive fees, and costs fluctuate dramatically over time. Notably, although the popularity of blockchains like Solana and layer two networks has reduced average transaction costs, the premiums paid by operators of stolen funds have risen by 108% during the same period. Furthermore, attackers targeting service platforms typically pay higher premiums, which may reflect their urgency to quickly transfer large amounts of funds before they are frozen.
These patterns suggest that while the vast majority of hacking attacks are financially motivated (with some exceptions like the June 19 Nobitex attack), operators of stolen funds do not care about on-chain transaction costs but prioritize transaction speed.
Interestingly, not all stolen funds immediately enter the money laundering process. Stolen funds from personal wallets tend to remain on-chain, with large balances lingering in addresses controlled by attackers rather than being quickly laundered or cashed out. This behavior of criminals holding onto funds may reflect their confidence in operational security or mimic mainstream cryptocurrency investment strategies.
Prevention and Mitigation Strategies
The surge in thefts from service platforms and personal wallets requires multi-layered security mechanisms for response. For service providers, the lessons from significant events in 2025 reiterate the following key points:
Comprehensive Security Culture
Regular security audits
Employee screening processes that can identify social engineering attacks
Code audits are becoming increasingly important, as smart contract vulnerabilities are becoming the fastest growing attack vector. Improvements in technical wallet infrastructure (especially the implementation of multi-signature hot wallets) provide an additional layer of protection for institutional security, allowing timely damage control even if a single key is compromised.
For individuals, the escalating threats targeting wallets require a fundamental restructuring of security concepts. The correlation between violent attacks and Bitcoin prices indicates that protecting holding privacy (such as avoiding public disclosure of positions) may be equally important as technical measures (using privacy coins or cold wallets). Users in countries with high victim growth should be particularly vigilant about their digital footprints and personal safety.
As cryptocurrency-related kidnappings and violent crimes escalate, real-world personal safety becomes an urgent issue. Cases targeting wealthy cryptocurrency families indicate that digital asset holders need to consider traditional security measures, including:
Avoid flaunting wealth
Do not disclose holdings or trading activities on social media
Implement basic security protocols (such as changing daily routes, being vigilant against surveillance)
For large holders, professional security consulting may be necessary; as digital wealth increases, personal vulnerabilities create new risks that traditional security systems have yet to fully address.
Outlook: A Critical Turning Point
Data from 2025 to date illustrates the evolutionary trajectory of cryptocurrency crime. Although the crypto ecosystem is maturing in terms of regulatory frameworks and institutional security practices, the capabilities and target ranges of threat actors are also upgrading.
The ByBit incident proves that even leading entities in the industry still struggle to withstand advanced persistent threats; the surge in personal wallet thefts indicates that cryptocurrency holders face unprecedented risks. The expansion of crime geography and the correlation between asset prices and violent attacks add a new dimension to an already complex security environment.
The detailed blockchain analysis supporting this report lays the foundation for more effective countermeasures. Law enforcement equipped with comprehensive transaction analysis tools can track funds more efficiently than ever, while service providers can implement targeted defenses based on attack patterns.
The cryptocurrency industry is at a critical turning point. The same transparency that fosters criminal analysis also provides more efficient prevention and law enforcement tools. The challenge lies in how to rapidly deploy these capabilities to stay ahead of continuously evolving threats.
Entering the second half of 2025, the amount of stolen cryptocurrency is unprecedentedly high. If the stolen funds indeed break through $4 billion as predicted, the industry's responses in the coming months may determine whether the crime trend continues to deteriorate or stabilizes as the defense systems mature.


