We are very pleased to announce the successful completion of the Levitron milestone project, which represents an important step forward for the Internet Computer Protocol (ICP) in terms of transparency and insight.
With this milestone, API boundary node (API BN) access logs will be publicly available in real-time, providing unprecedented insights into the usage of the Internet Computer and its hosted containers.
The edge of the Internet Computer: API boundary nodes
API BNs serve as the public edge of the Internet Computer, they are the first point of contact for every incoming request, forwarding each request to the appropriate subnet, replica nodes, and ultimately to the target container, meaning they capture and log every external request to the Internet Computer.
Unlock new insights with public access logs
Public access logs are a valuable resource for container developers and the broader ICP community, providing a wealth of previously inaccessible information, for example, they allow for the following actions:
Tracking container usage: Developers can now observe the full range of container interactions, including previously invisible query calls.
Measuring network activity: The broader community can track popular dapps and overall network activity.
Providing data for analytical platforms: Ranking and analytical platforms can directly integrate these logs to provide accurate metrics straight from ICP.
Previously, these logs were not publicly accessible; however, in the spirit of Web3, the Levitron milestone has changed that: each API BN now exposes an endpoint that allows clients to directly subscribe and stream these logs.
Decentralized, direct, detailed
This new access method is completely decentralized, meaning no intermediaries; interested parties can directly transmit information from the Internet Computer's API boundary nodes.
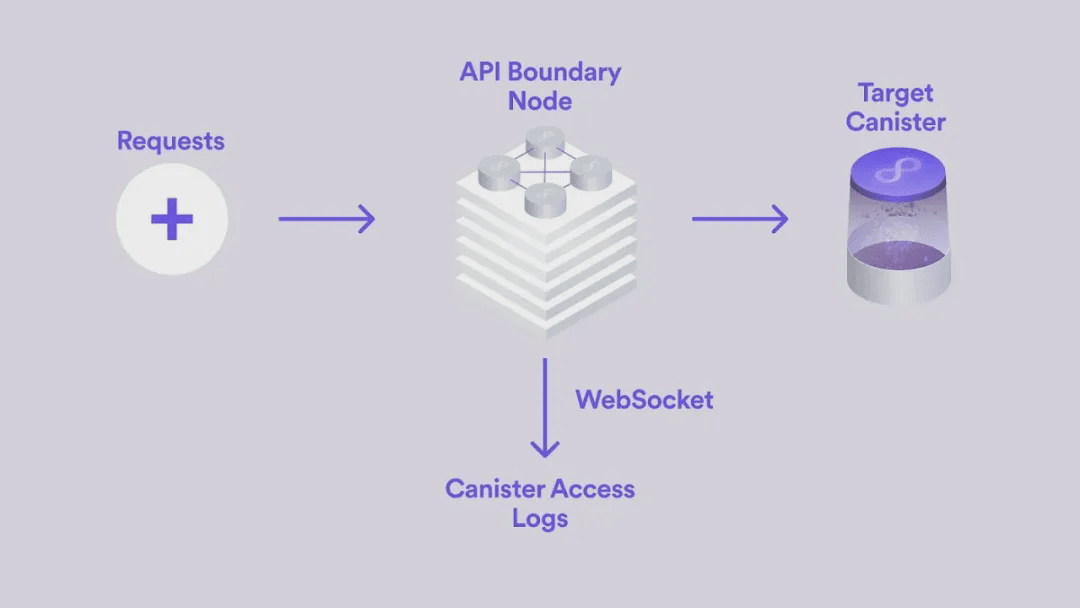
Log streams are per container, providing detailed information such as:
Called methods
Response status code
Client making the call
Response cache status (hit, miss, or bypass)
Error message (if any)
Size of request and response
And more
Prioritizing privacy
It is important to understand that these logs were designed with privacy protection in mind; they do not contain any information regarding the actual payload of the calls, IP addresses, or sender entities. The only user-related information is the client ID, which is a salt hash of the IP address and the sender.
This salt value is derived from the salt shared container, which is rotated monthly, and only API BNs can access it, meaning no other entities can know this salt value, ensuring that valuable usage data is still accessible without compromising user privacy.
Real-time streaming and future enhancements
Starting today, you can stream logs in real-time! It is important to note that this direct streaming mechanism does not provide historical data; if you want to analyze past activities, you will need to build your own database to store the streamed logs.
To help you get started, we provide instructions in the documentation, along with readily available example clients.
Looking ahead, once SEV-SNP is rolled out to API boundary nodes, clients will be able to prove these nodes, significantly enhancing the authenticity and integrity of these logs, giving you more confidence in the data.
For more in-depth information and technical details, be sure to check the official documentation and example clients:
internetcomputer.org/docs/building-apps/advanced/canister-access-logs
github.com/dfinity/ic-bn-logs

Content about IC that matters to you
Technical progress | Project information | Global events

Follow the IC Binance channel
Stay updated
