Overview
In May 2025, the total loss from Web3 security incidents was approximately $266 million. Among them, according to statistics from the SlowMist Blockchain Hacking Archive (https://hacked.slowmist.io), there were a total of 15 hacking incidents, resulting in losses of approximately $257 million, with $162 million frozen or returned. The causes of incidents include contract vulnerabilities, oracle attacks, and account hacks. Additionally, according to statistics from the Web3 anti-fraud platform Scam Sniffer, there were 7,164 victims of phishing incidents this month, with losses amounting to $9.63 million.
 (https://dune.com/scam-sniffer/may-2025-scam-sniffer-scam-report)
(https://dune.com/scam-sniffer/may-2025-scam-sniffer-scam-report)
Major Security Incident
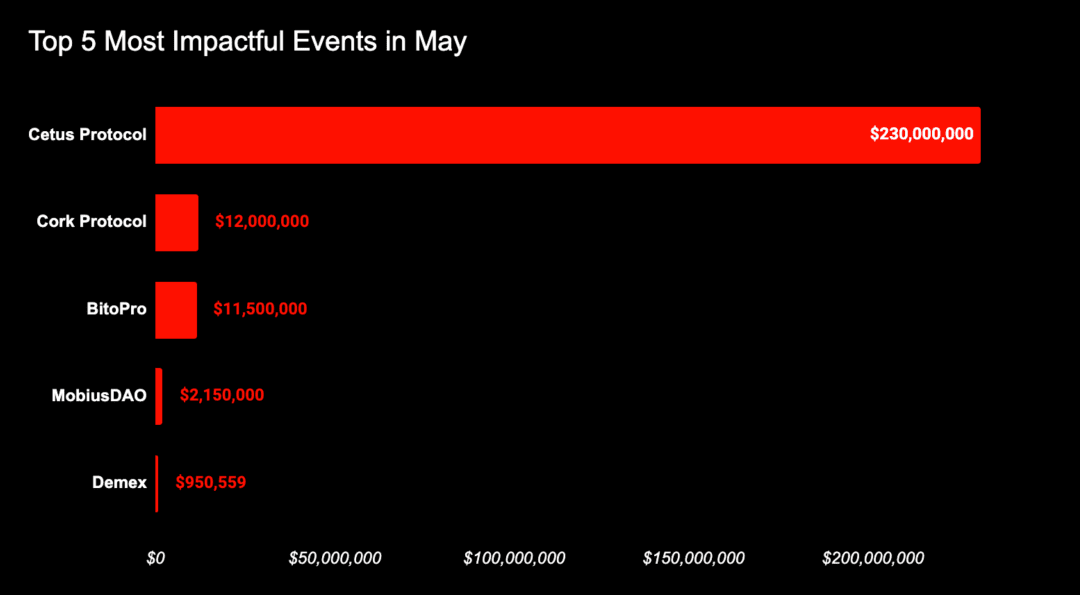 Cetus Protocol
Cetus Protocol
On May 22, 2025, the liquidity provider Cetus Protocol in the SUI ecosystem was attacked, resulting in a significant decrease in liquidity pool depth, with multiple token trading pairs on Cetus experiencing declines, leading to a loss of approximately $230 million.
After the incident occurred, the SlowMist security team intervened immediately to analyze and found that the core of the incident was that the attacker carefully constructed parameters to cause an overflow while bypassing detection, ultimately allowing a very small amount of Token to exchange for huge liquidity assets. For detailed analysis, see SlowMist: Analysis of the $230 million theft incident involving Cetus.
 (Attack Timeline)
(Attack Timeline)
Fortunately, according to Cetus, with the cooperation of the SUI Foundation and other ecosystem members, $162 million of the stolen funds on SUI have been successfully frozen.
 (https://x.com/CetusProtocol/status/1925567348586815622)
(https://x.com/CetusProtocol/status/1925567348586815622)
Cork Protocol
On May 28, 2025, SlowMist detected potential suspicious activities related to Cork Protocol. According to analysis by the SlowMist security team, the root cause of the attack was that Cork allowed users to create redemption assets (RA) using any asset through the CorkConfig contract, allowing attackers to use DS as RA. Additionally, any user could call the beforeSwap function of the CorkHook contract without authorization and pass in custom hook data for CorkCall operations, allowing attackers to manipulate and deposit legal market DS into another market for use as RA, gaining corresponding DS and CT tokens.
 (https://x.com/SlowMist_Team/status/1927705256915333359)
(https://x.com/SlowMist_Team/status/1927705256915333359)
According to analysis by the on-chain anti-money laundering and tracking tool MistTrack, the attacker's address 0xea6f30e360192bae715599e15e2f765b49e4da98 profited 3,761.878 wstETH, valued at over $12 million. As of now, a total of 4,530.5955 ETH remains in the attacker's address, and we will continue to monitor the funds.
 BitoPro
BitoPro
According to on-chain detective ZachXBT, the Taiwanese cryptocurrency exchange BitoPro was allegedly attacked on May 8, 2025, with losses amounting to approximately $11.5 million. Abnormal outflows of funds were observed in the hot wallets of BitoPro across multiple chains, including Tron, Ethereum, Solana, and Polygon. Stolen assets were rapidly sold off through decentralized exchanges. Subsequently, these funds were transferred to Tornado Cash or cross-chain transferred to the Bitcoin network via Thorchain, and further deposited into Wasabi wallets for laundering.
 (https://x.com/zachxbt/status/1929417001296146868)
(https://x.com/zachxbt/status/1929417001296146868)
Demex
On May 16, 2025, Demex's lending market Nitron was attacked, resulting in a loss of approximately $950,000. According to the incident analysis report released by Demex, the root cause of the attack was that the attacker conducted a donation-based oracle manipulation attack on the abandoned dGLP vault.
 (https://blog.dem.exchange/nitron-post-mortem/)
(https://blog.dem.exchange/nitron-post-mortem/)
On May 19, Demex updated the incident progress, stating that with the support of partners, they have successfully recovered $78,000.
Zunami Protocol
On May 15, 2025, Zunami Protocol tweeted that it was attacked, with collateral assets of zunUSD and zunETH stolen, resulting in a loss of approximately $500,000. The attacker has transferred the stolen funds to Tornado Cash.
 (https://x.com/ZunamiProtocol/status/1922993510925435267)
(https://x.com/ZunamiProtocol/status/1922993510925435267)
On May 30, Zunami Protocol founder @kirill_zunami tweeted that an investigation into the attack incident is underway, considering two possible scenarios: the deployer's key was stolen, or the key holder engaged in malicious behavior.
 (https://x.com/kirill_zunami/status/1928131508117651725)
(https://x.com/kirill_zunami/status/1928131508117651725)
Feature Analysis and Security Recommendations
In this month's blockchain security events, contract vulnerabilities remain the primary cause of losses. Among them, 6 contract vulnerability-related incidents resulted in approximately $244 million in losses, accounting for 95% of the losses from hacking incidents this month. The SlowMist security team recommends that project parties maintain a high level of vigilance, regularly conduct comprehensive security audits, promptly identify and fix potential vulnerabilities, and stay updated on the latest attack techniques and security trends to effectively safeguard assets and user safety.
This month's account hacking incidents have once again attracted widespread attention, with a total of 6 incidents occurring. In addition to the official accounts of Web3 projects, media institutions and other high-profile accounts have also become targets of attacks. For example, on May 12, the X account of the British football club @SheffieldUnited was hacked, and the attacker used it to post false token addresses. The attacker also used Cointelegraph's X account to privately send phishing links to lure users into clicking. For information on how to strengthen X platform account security, refer to SlowMist's previously published guide: SlowMist: X Account Security Inspection and Reinforcement Guide.
It is worth noting that the North Korean hacker group Lazarus Group has recently begun shifting its attack targets from institutions to individual investors. On May 24, this organization stole over $5.2 million from a merchant via malware, marking a significant shift in its attack strategy. Therefore, ordinary users should also actively enhance their security awareness and refer to the Blockchain Dark Forest Self-Guard Handbook to improve their protective capabilities. (https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook)
This month, there has been new progress in investigating the reasons behind the frequent social engineering attacks on Coinbase users. According to information disclosed by Coinbase, attackers exploited the privileges of internal employees to obtain sensitive data from some users and launched precise social engineering attacks based on this. This finding reveals the significant hidden dangers of collusion within the security system and once again reminds various platforms to strengthen management of internal permissions. For more details, see 'Customer Service' in the Dark Forest: Social Engineering Scams Targeting Coinbase Users.
Finally, the incidents included in this article represent the major security events of this month. More blockchain security incidents can be viewed in the SlowMist Blockchain Hacking Archive (https://hacked.slowmist.io/).

