Author: Lisa & 23pds
Editor: Liz
Background
On May 21, 2025, the U.S. Department of Justice (DOJ), in collaboration with Microsoft and law enforcement agencies from multiple countries, successfully seized the notorious info-stealing malware LummaC2's core infrastructure. The five key domain names and their subdomains that were seized were all fundamental operational nodes of LummaC2, and law enforcement successfully located and controlled over 2,300 sites behind it, indirectly striking many downstream attack groups that relied on this tool.
According to disclosures from the FBI, LummaC2 has been used in over 1.7 million info-stealing attacks, targeting not limited to browser autofill data, email and bank account login credentials, cryptocurrency wallet mnemonic phrases, etc. This seizure operation was conducted in phases: on May 19, the government seized two domain names; on May 20, LummaC2 administrators notified users of three new alternative domain names; the next day, these three domain names were also seized.
What is LummaC2?
LummaC2 (also known as Lumma Stealer) is an active info-stealer malware written in C language that has rapidly gained favor among criminals since its emergence in 2022. It operates under the MaaS model, has a low technical threshold, strong dissemination capabilities, and has been used in various cyber attacks worldwide.
This malware is sold by a developer named 'Shamel' (alias 'Lumma') on Russian hacker forums and communicates with 'clients' through Telegram groups.
 (Image source: Cyble)
(Image source: Cyble)
Lumma Stealer maintains a robust C2 infrastructure, primarily targeting cryptocurrency wallets and two-factor authentication (2FA) plugins in browsers, with the aim of stealing various sensitive information from victims' devices.
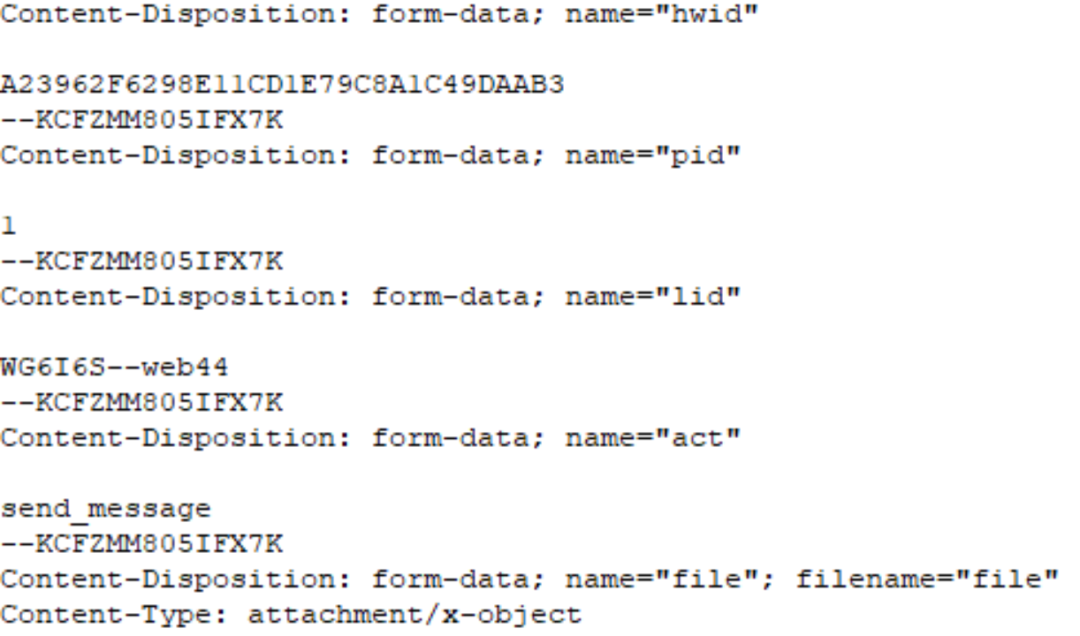 (Image source: ASEC)
(Image source: ASEC)
According to the joint disclosure by the FBI and the Cybersecurity and Infrastructure Security Agency (CISA), there were 21,000 LummaC2 logs appearing in the underground market from April to June 2024, an increase of 71.7% compared to the same period. As of May 2025, this trojan remains active in several critical infrastructure industries in the United States.
Its core dissemination methods include:
Phishing emails: Impersonating well-known brands or services to send emails with malicious links or attachments, tricking users into clicking and redirecting them to fake websites or malicious servers.
Malicious ads: Inducing users to visit phishing websites disguised as Chrome updates or commonly used download pages through search engine ads.
Trojan bundling: Bundling Lumma Stealer into pirated software installation packages (like 'cracked' software), often executed silently without the user's knowledge, typically distributed via file-sharing platforms.
Obfuscation techniques: Using large amounts of obfuscated strings or cooperating with other malware to evade antivirus software or endpoint detection systems (EDR), increasing detection difficulty.
Additionally, LummaC2 can spread through fake CAPTCHA pages, tricking users into clicking the 'I am not a robot' button to execute malicious commands hidden in the clipboard.
 (Image source: ASEC)
(Image source: ASEC)
Attackers guide users to run the command in the system under the guise of a 'verification process'; in fact, this is a Base64-encoded PowerShell script designed to download and execute Lumma's malicious code.
 (Image source: ASEC)
(Image source: ASEC)
This malware also integrates the ClipBanker module, which automatically replaces the copied cryptocurrency wallet address with an address controlled by the attacker, thus transferring the user's assets.
Why should we combat LummaC2?
Mass infections and information theft: It was reported that between March and May 2025, approximately 394,000 Windows devices worldwide were infected with LummaC2. This malware was used to steal browser data, autofill information, banking service login credentials, and the mnemonic phrases for cryptocurrency wallets.
Threats to critical infrastructure: The activities of LummaC2 have expanded to multiple critical infrastructure sectors in the United States, threatening the cybersecurity of individuals and organizations.
Malware as a Service (MaaS) model: LummaC2 operates under a MaaS model, allowing cybercriminals to gain access to the malware through subscription services, further broadening its impact.
International cooperation to combat cybercrime: This operation was executed by the U.S. Department of Justice in collaboration with Microsoft, Europol, the Japan Cybercrime Control Center, and other international partners, aimed at combating transnational cybercrime activities through legal and technical means.
Operating mechanism
LummaC2's operating mechanism is highly automated, mainly divided into the following stages:
1. Infection deployment
Attackers spread the LummaC2 payload to users through phishing emails, disguised downloads, and exploiting vulnerabilities. When users are tricked into clicking the 'Yes' button in a pop-up window, the malicious program decrypts and connects to the preset C2 server.
 (Image source: CISA)
(Image source: CISA)
Once executed, LummaC2 quietly starts in the background and begins stealing information.
 (Image source: Microsoft)
(Image source: Microsoft)
2. Information collection
The content stolen by LummaC2 includes:
Local information: including Lumma version number, Lumma ID, hardware ID, screen resolution, system language, CPU information, and memory size, etc. This data is organized into a file named system.txt, which is stored in memory.
Cryptocurrency wallets: Focus on wallets like Binance, Electrum, Ethereum, etc. It scans the system for sensitive information related to these wallets and packages it for sending to the C2 server.
Browser data: LummaC2 checks whether the following browsers are installed on the system and attempts to steal sensitive data from them (such as accounts, cookies, etc.): Chrome, Chromium, Edge, Kometa, Vivaldi, Brave, Opera (stable/GX/Neon), Firefox. It then further searches for installed cryptocurrency wallet plugins and two-factor authentication (2FA) plugins in the browsers. Additionally, it can obtain users' browser history, login credentials, cookies, and other data.
User documents: LummaC2 scans the %userProfile% directory, extracts .txt files, marks them as 'important files', and uploads them to the server.
The key APIs called include: GetUserNameW, GetComputerNameW, cpuid, etc., used for collecting system information.
 (Image source: CISA)
(Image source: CISA)
3. Encryption and Upload
After the information collection is complete, LummaC2 compresses and encrypts the data and uploads it to the C2 for centralized processing via HTTP POST. It supports multiple backups and asynchronous upload mechanisms, ensuring that even if part of the data transfer fails, core information will still arrive. When not communicating, the program often only resides in memory to avoid leaving traces on disk. After connecting to C2, it may further deploy new malicious payloads or write files. It also has a built-in self-protection mechanism: if the current username and computer name match a specific hash value, it automatically terminates its operation (suspected to avoid infecting the developer's own environment).
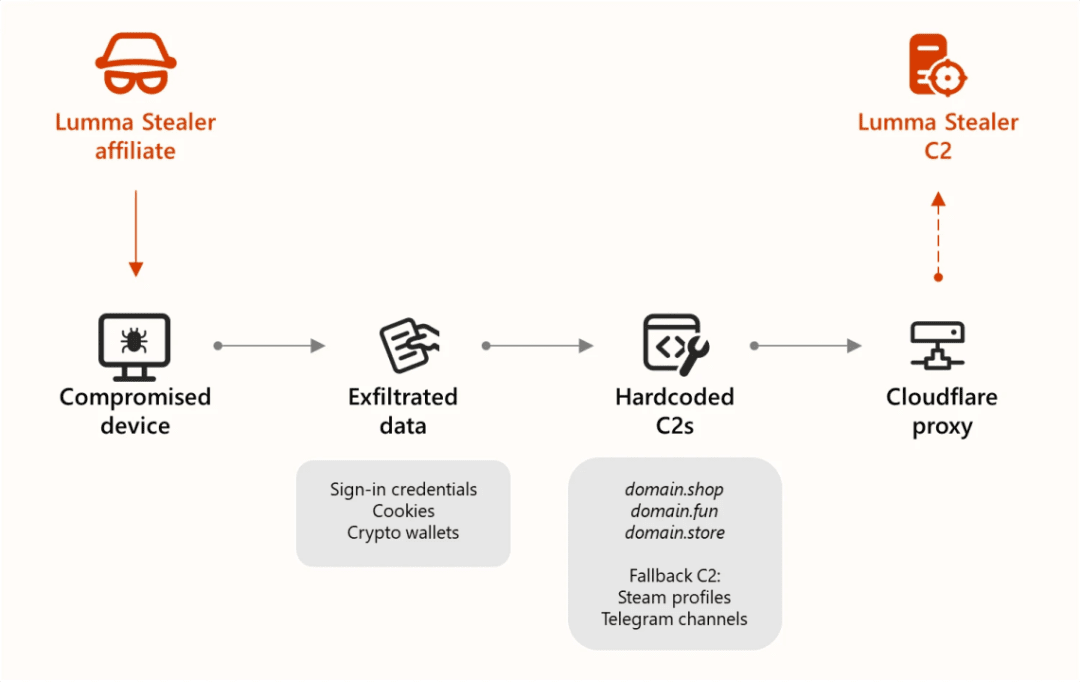 (Image source: Microsoft)
(Image source: Microsoft)
4. Data return and panel management system (C2 Dashboard)
LummaC2 receives JSON configuration commands from the C2, parses them, and sends targeted data back to the server. Attackers can view victim data in real-time through a web console, filtering, exporting, or selling, and support geographic filtering, automatic classification, and device fingerprint management functionalities.
Essentially, LummaC2 is a component of the 'Malware as a Service' (MaaS) ecosystem. Attackers only need to pay a monthly fee (starting at $250/month in 2024) to access continuously updated malware, management backend, technical support, and customized services.
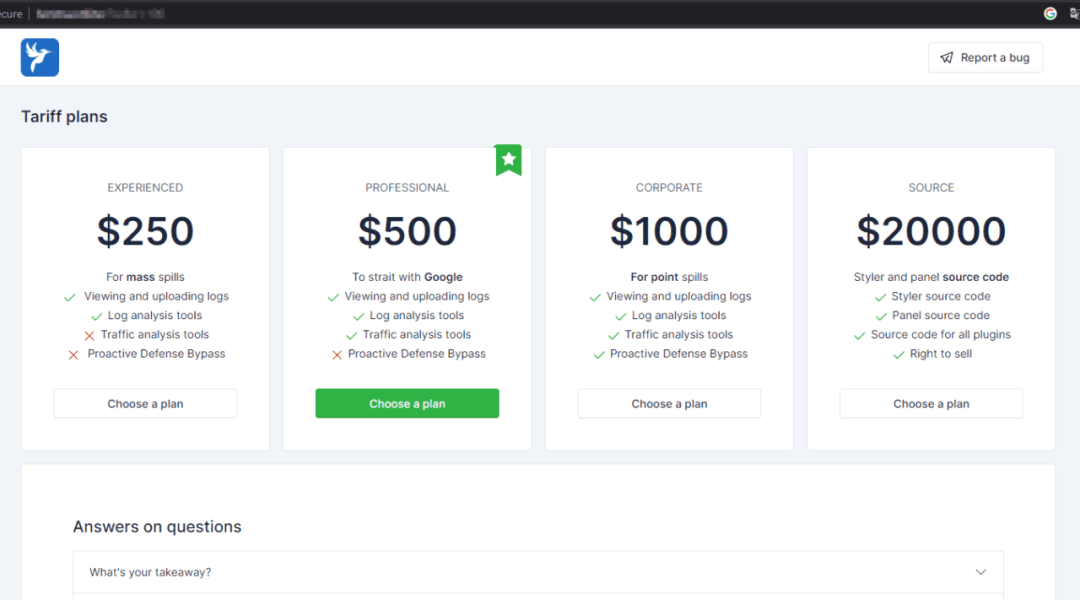 (Image source: Cyble)
(Image source: Cyble)
Service content includes:
Telegram rapid response group;
Automated deployment tools;
Encrypted communication and anonymous payments (mostly USDT, XMR, etc.).
 (Image source: Cyble)
(Image source: Cyble)
This model has fueled the involvement of numerous 'non-technical' criminals in cyber attacks, further exacerbating rampant activities such as online fraud, cryptocurrency wallet theft, and corporate espionage.
Preventive recommendations
LummaC2 is just one of many typical info-stealing trojans, and users and businesses need to defend from multiple levels:
For ordinary users:
Do not click on links and attachments from unknown sources;
Enable two-factor authentication (2FA) to prevent account theft even if passwords are leaked;
Regularly clear browser cache and cookies, and try not to save sensitive data in the browser;
Install and regularly update antivirus software, and keep the system timely updated with patches.
For businesses:
Use complex passwords: When setting up passwords for servers or internal systems, enterprises should use complex login credentials, such as requiring numbers, uppercase and lowercase letters, special symbols, and a minimum length of 8 characters, and regularly change passwords.
Two-factor authentication: For sensitive information within enterprises, additional layers of defense should be added to password-based logins to prevent hacker attacks, such as installing biometric verification (fingerprint, iris, etc.) or using physical USB key authenticators on sensitive systems.
Four don'ts: Don't click on emails from unknown sources; don't browse malicious information websites; don't install software from unknown sources; be cautious when installing software sent by strangers; don't casually insert unknown USB drives, external hard drives, flash drives, etc. into devices.
Data backup protection: The real guarantee against data loss is always offline backup, so it is essential to back up critical data and business systems. Note that backups should be clear and labeled for each stage to ensure that a backup can be promptly retrieved in case of malware infection.
Regular antivirus scans and port shutdowns: Install antivirus software and regularly update the virus database; periodically perform full system scans; shut down unnecessary services and ports (including unnecessary remote access services like port 3389, port 22, and unnecessary LAN sharing ports like 135, 139, 445, etc.).
Enhance employee security awareness: The greatest risk in safety production lies with personnel. Phishing, social engineering, poisoning, weak passwords, etc. are all critical factors closely related to personnel's safety awareness. Therefore, to improve overall security fortification and defensive capabilities, it is essential to raise personnel's security awareness.
Timely patching of office terminals and servers: Timely patch the operating system and third-party applications to prevent attackers from exploiting vulnerabilities to invade the system.
In conclusion
The seizure of LummaC2 is not only a technical blow but also a model for global cybersecurity cooperation. As the MaaS (Malware as a Service) model continues to evolve, info-stealing trojans will continue to mutate, reminding us that in the security of encrypted assets, device and environmental security is equally critical. SlowMist will continue to monitor related dynamics and provide security support to users and platforms through threat intelligence networks and tracking capabilities, jointly building a safer and more transparent Web3 ecosystem.
References
[1] https://www.justice.gov/opa/pr/justice-department-seizes-domains-behind-major-information-stealing-malware-operation
[2] https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-141b
[3] https://asec.ahnlab.com/jp/85671/
[4] https://cyble.com/blog/lummac2-stealer-a-potent-threat-to-crypto-users/
[5] https://www.microsoft.com/en-us/security/blog/2025/05/21/lumma-stealer-breaking-down-the-delivery-techniques-and-capabilities-of-a-prolific-infostealer/

