The attack was carried out by exploiting a function called “sweepUnclaimed()” in the smart contracts that manage #Zksync ’s airdrop processes. This feature is normally designed to withdraw unclaimed $ZK tokens. However, the attacker exploited this function for a total of 111 million ZK token options from three different airdrop contracts. This amount corresponds to approximately 0.45 percent of the total token supply.
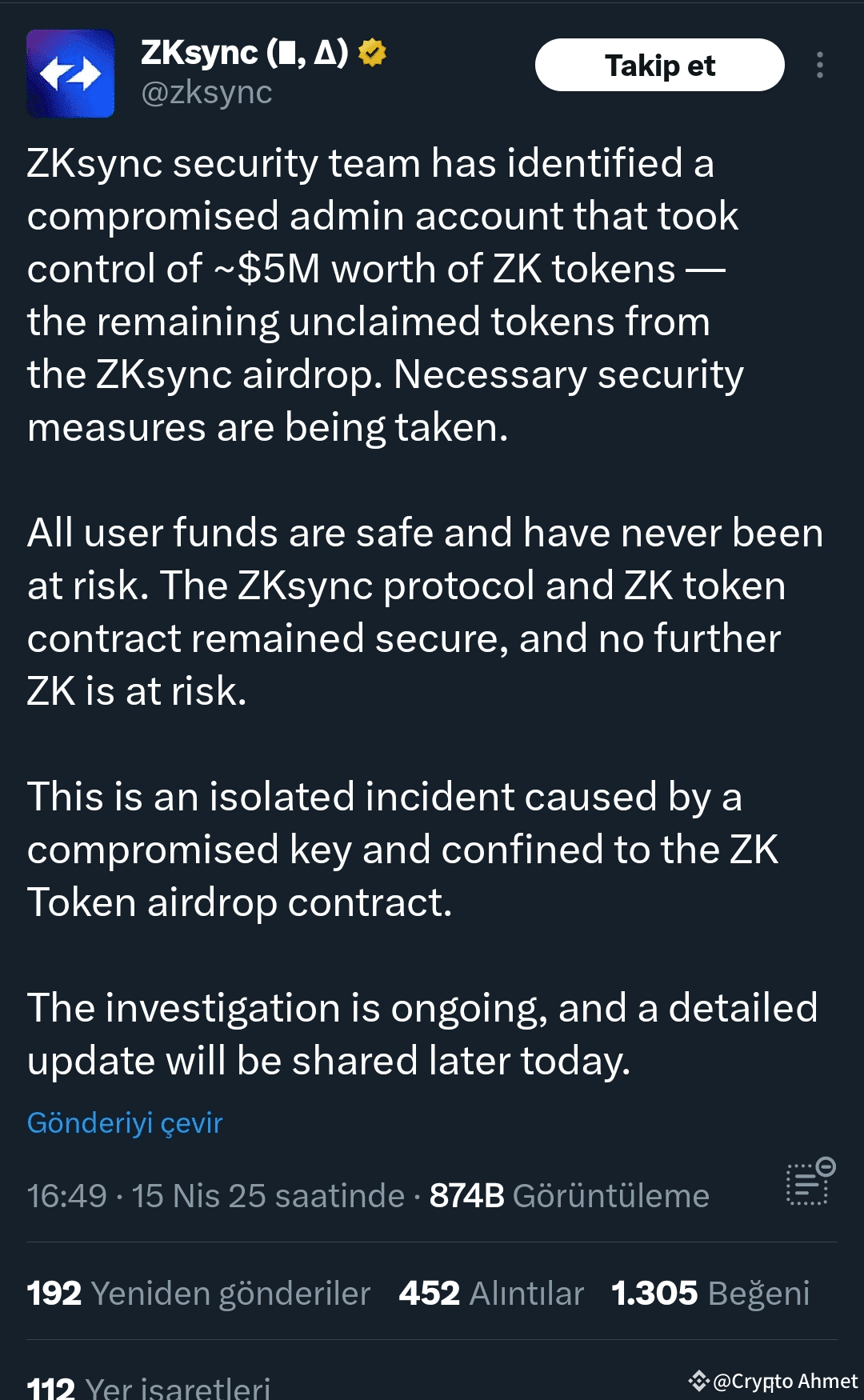
Following the incident, the zkSync development team launched a rescue operation together with its security partner SEAL. The team stated that the attack was limited to the administrative budget only and that user funds were directly affected. It was also emphasized that the “sweepUnclaimed()” function was disabled and the system did not contain any other vulnerabilities.
This incident once again demonstrated how critical security is not only in zkSync but also in Layer-2 solutions in general. How administrator-level access is structured, how airdrop results are controlled, and the distribution of smart contract usage possibilities are being re-evaluated across the industry.
On February 21, 2025, cryptocurrency exchange Bybit was subject to one of the largest crypto attacks to date. North Korea-related Lazarus Group hackers exploited vulnerabilities in Bybit's Ethereum cold vaults to withdraw approximately 401,000 ETH (approximately $1.5 billion). Bybit stated in its transactions that user funds were recovered and that losses would be covered by company reserves.




