Recently, we have received many requests for help from victims, all of which are related to the "Fake Safeguard" scam on Telegram. Since many users are not familiar with this type of attack method, they are often not vigilant enough when encountering this scam. Both novices and experienced players are likely to be fooled. This article will deeply analyze the attack method of this scam and provide effective prevention suggestions to help users protect their assets from losses.
Scam Analysis
There are two main types of scams of this type. One is stealing Telegram accounts. Scammers trick users into entering their mobile phone numbers, verification codes, or even Two-Step Verification passwords to steal their Telegram accounts. The other is implanting Trojans into users' computers, which is also a method that has appeared more frequently recently. This article will focus on the second method.

In some popular token airdrop activities, when users’ FOMO emotions are high, they will definitely click Tap to verify when they see the following channel interface on Telegram:

After clicking Tap to verify, a fake Safeguard bot will open, which ostensibly shows that verification is in progress. This verification window is extremely short, giving a sense of urgency and forcing the user to continue.

Continue clicking, and the result "pretends" to show that the verification failed, and finally a prompt interface for the user to manually verify appears:

The scammers have thoughtfully configured Step 1, Step 2, and Step 3. At this point, the user’s clipboard already has malicious code. As long as the user does not actually follow these steps, there will be no problem:

But if the user follows these steps obediently, the computer will be infected with the virus.
Here is another example - attackers impersonate KOLs and use malicious robots to verify and run malicious Powershell code. Scammers create a fake KOL account X, and then they attach a Telegram link in the comment section, inviting users to join an "exclusive" Telegram group to get investment information. For example, the scam account that appears in the comment section of @BTW0205, many users will see "exciting news" in the comment section:

Then I entered the corresponding Telegram Channel and guided the user to verify.

When the user clicks on verification, a fake Safeguard appears. Similar to the above process, Step 1, Step 2, and Step 3 appear to guide the verification operation.

At this point, the user's clipboard has been secretly implanted with malicious code content. If the user really follows the instructions to open the run box, and press Ctrl + V to paste the malicious code content into the run box, the status at this time will be as shown below. The run box does not show all the content, and a large blank area is in front of the word Telegram and the malicious code.

These malicious codes are usually Powershell instructions, which will silently download more complex malicious codes after execution, and eventually infect the computer with remote control Trojans (such as Remcos). Once the computer is controlled by the Trojan, hackers can remotely steal sensitive information such as wallet files, mnemonics, private keys, passwords, etc. in the computer, and even steal assets. (PS. For the behavior of the "fake Safeguard" Trojan, please refer to the analysis of the white hat Jose in the Slow Mist area, which is at: https://jose.wang/2025/01/17/%E4%BC%AASafeguard%E7%97%85%E6%AF%92%E5%88%86%E6%9E%90/)

The comment section of the Ethereum Foundation account @ethereumfndn has also been contaminated by this scam, which is a large-scale net-casting and harvesting model.
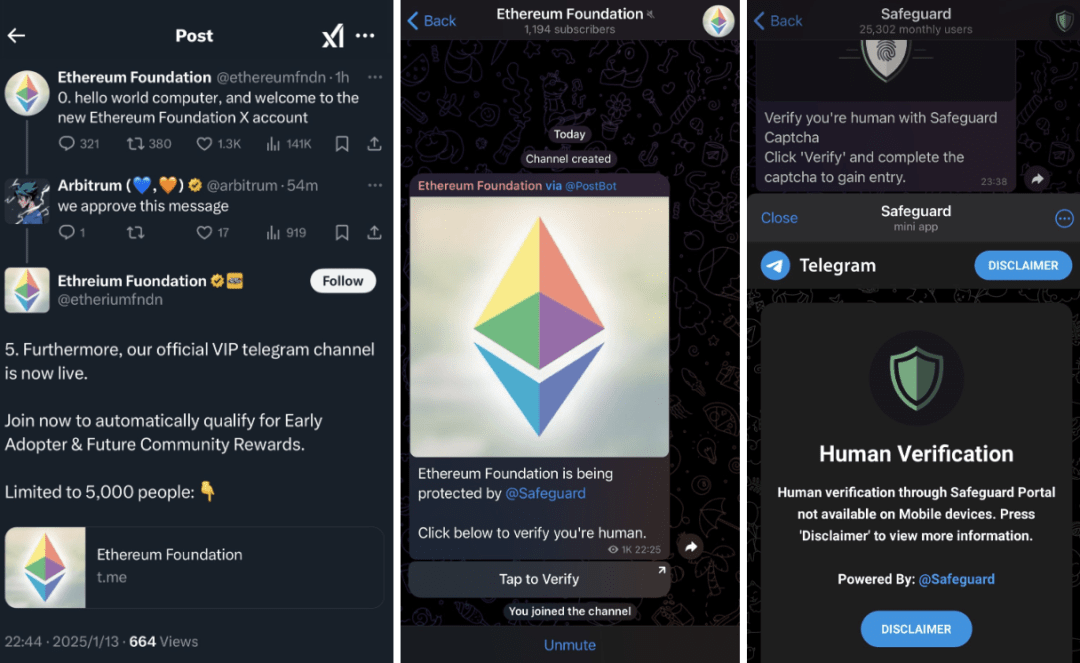
The latest example is Trump’s X comment section which has also been contaminated by this scam:

If you open it on your phone, the scam will gradually get your Telegram permissions. If you find it in time, you need to go to Privacy and Security -> Active sessions -> Terminate all other sessions in Telegram settings as soon as possible, and then add or modify Two-Step Verification.

If you are using a Mac computer instead of a Windows computer, there are similar ways to trick your computer into being infected. The routine is similar. When the following image appears in Telegram, your clipboard has been secretly implanted with malicious code content.

There is no risk at this point, but if you follow the steps given, the following consequences will occur:

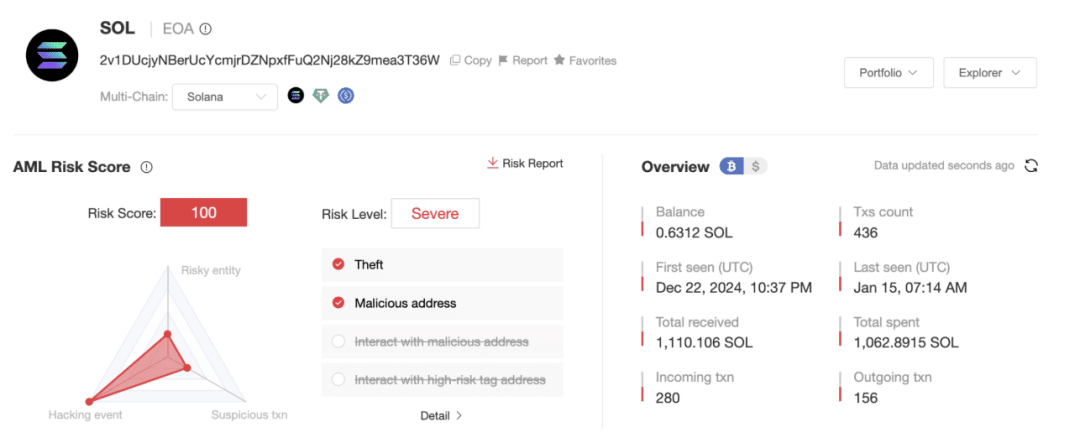
We selected several hacker addresses and analyzed them using the on-chain tracking and anti-money laundering platform MistTrack.
Solana hacker address:
HVJGvGZpREPQZBTScZMBMmVzwiaVNN2MfSWLgeP6CrzV
2v1DUcjyNBerUcYcmjrDZNpxfFuQ2Nj28kZ9mea3T36W
D8TnJAXML7gEzUdGhY5T7aNfQQXxfr8k5huC6s11ea5R
According to MistTrack’s analysis, the above three hacker addresses have currently made a total profit of over 1.2 million US dollars, including SOL and multiple SPL Tokens.
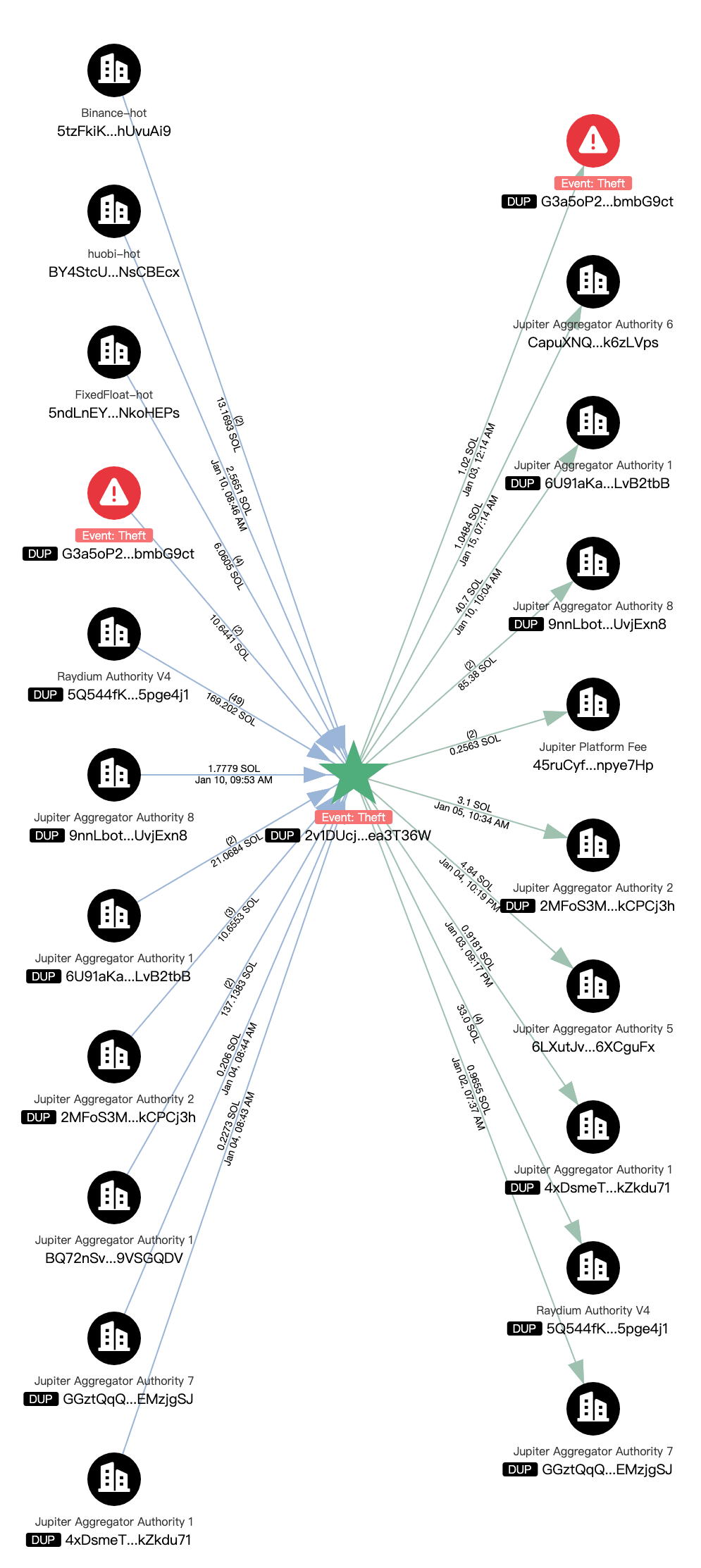
The hacker will first convert most of the SPL Tokens into SOL:

Then SOL is dispersed and transferred to multiple addresses, and the hacker's address also interacts with Binance, Huobi, and FixedFloat platforms:
In addition, the current address HVJGvGZpREPQZBTScZMBMmVzwiaVNN2MfSWLgeP6CrzV still has 1,169.73 SOL and a token balance worth over $10,000.

Let’s analyze one of the Ethereum hacker addresses 0x21b681c98ebc32a9c6696003fc4050f63bc8b2c6. The first transaction of this address was in January 2025, involving multiple chains, and the current balance is about 130,000 US dollars.

This address transfers ETH to multiple platforms such as ChangeNOW, eXch, Cryptomus.com:

If your computer is compromised, here’s what you need to do immediately:
1. All wallets and funds used on this computer should be transferred in time. Don’t think that it’s okay to extend the wallet with a password;
2. Change the passwords or logged-in accounts, passwords or 2FA saved in each browser as much as possible;
3. Change all other accounts on the computer, such as Telegram, etc.
Just make the most extreme assumption. Anyway, your computer is infected, and your computer is transparent to the scammers. So think in reverse, if you are a scammer, and you have complete control over a computer active in the Web3/Crypto world, what would you do? Finally, after backing up important computer data, you can reinstall it, but after reinstalling it, it is best to install internationally renowned antivirus software, such as AVG, Bitdefender, Kaspersky, etc., and perform a full disk antivirus. Once the problem is solved, there will be no problem.
Summarize
The fake Safeguard scam has developed into a mature hacker attack model. From fake comments to implanting Trojans and stealing assets, the entire process is covert and efficient. As the means of attack become more sophisticated, users need to be more vigilant about all kinds of misleading links and operation steps on the Internet. Only by raising vigilance, strengthening protection, and timely discovering and handling potential threats can we effectively prevent the harm of such scams.