Author: 77
Editor: 77
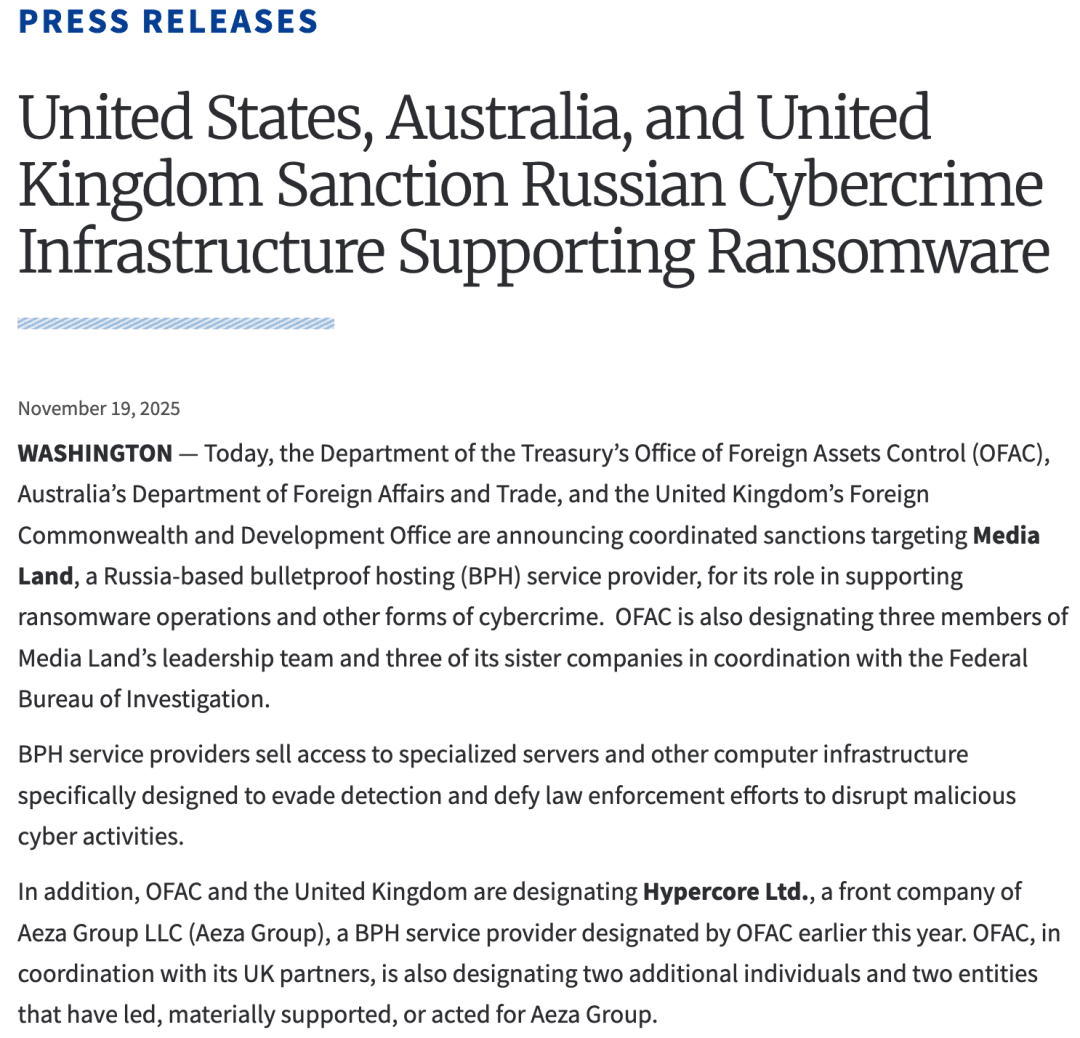
On November 19, 2025, the U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC), the Australian Department of Foreign Affairs and Trade (DFAT), and the UK Foreign, Commonwealth & Development Office (FCDO) jointly announced a new round of sanctions against several Bulletproof Hosting (BPH) service providers and related individuals in Russia. The reason is their support for cybercrime activities, including ransomware. The main targets of the sanctions include key figures from Media Land and its affiliated entities, as well as key members of Aeza Group and related shell companies.
 (https://home.treasury.gov/news/press-releases/sb0319)
(https://home.treasury.gov/news/press-releases/sb0319)
What is a 'bulletproof hosting' provider?
Bulletproof hosting providers are a type of internet infrastructure provider dedicated to cybercriminals, renting virtual or physical servers to host illegal content and conduct various malicious activities. The term 'bulletproof' is essentially a marketing tactic; these services are not truly unassailable but are difficult to shut down directly because their operators refuse to comply with law enforcement's takedown orders and deliberately ignore abuse complaints, content takedown notices, etc. This high tolerance environment allows cybercriminals to communicate, operate forums and illegal websites, deploy malware and phishing activities, and engage in money laundering operations on these infrastructures without fearing that services will be terminated due to law enforcement intervention. Therefore, bulletproof hosting providers play a highly critical role in the global cybercrime ecosystem, being difficult to tackle directly while having a profound impact on the scale and continuity of malicious activities.
Details of sanctions
Media Land: A bulletproof hosting network led by Volosovik
Media Land LLC (Media Land) is headquartered in Saint Petersburg, Russia, and is a typical bulletproof hosting (BPH) provider, long providing dedicated servers and infrastructure for ransomware organizations such as LockBit, BlackSuit, and Play, and supporting multiple large-scale DDoS attacks. Its core figure, Aleksandr Volosovik (also known as 'Ohyeahhellno', 'podzemniy1', 'Yalishanda'), has been active in underground forums since 2010 and maintains close collaborations with several cybercrime groups, including Evil Corp, LockBit, and Black Basta. Under Volosovik's leadership, Media Land has built a hosting system covering multiple key links in the cyber attack chain, providing stable infrastructure support for underground exchanges, money laundering services, scam groups, hackers, and ransomware operators.
The US Department of the Treasury pointed out that Media Land was included in sanctions because it directly or indirectly participated in, or provided support to individuals located outside the US, for malicious cyber activities that may or have already posed a threat to US national security, foreign policy, economic health, or financial stability. The goal of these activities typically involves disrupting the availability of computers or networks or compromising the integrity of the information on them.
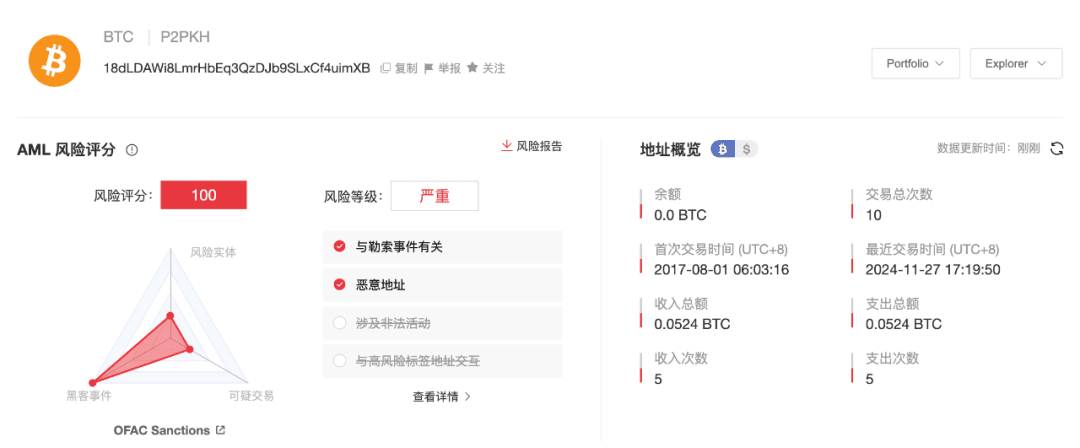
In this round of sanctions, a Bitcoin address directly controlled by Aleksandr Volosovik was also listed on the OFAC sanctions list:
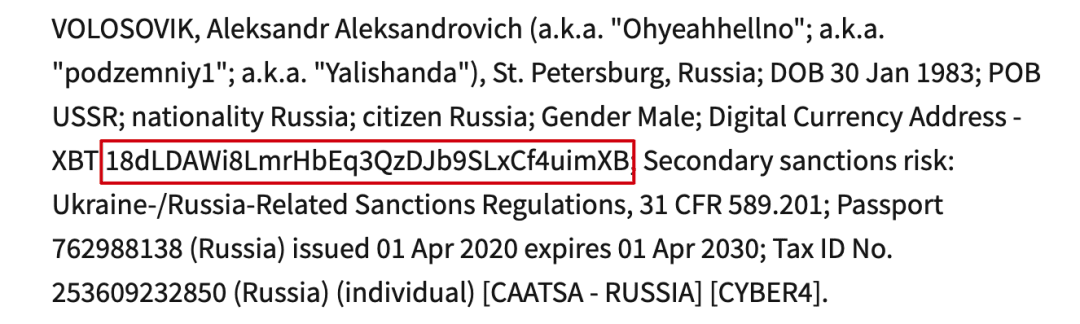
The anti-money laundering tracking and analysis system MistTrack under SlowMist shows that this Bitcoin address has been continuously active since August 2017 until November 2024, with a total of 5 inbound transactions, accumulating 0.0524 BTC.
UK officials pointed out that malicious infrastructures supported by Media Land pose a significant threat to national security. Official data shows that cyber attacks caused losses of up to £14.7 billion to UK businesses in 2024, accounting for 0.5% of GDP, and this is increasing every year.
The Media Land entities involved in this sanction include:
1. Individuals (3):
Aleksandr Volosovik (Volosovik): The general manager of Media Land, who promotes Media Land's illegal services under the pseudonym 'Yalishanda' on cybercrime forums and provides servers to ransomware and DDoS attackers, assisting with troubleshooting.
Kirill Zatolokin (Zatolokin): An employee of Media Land, responsible for customer collections and coordinating other cybercriminal activities, while closely cooperating with Volosovik to manage Media Land's overall operations.
Yulia Pankova (Pankova): An employee of Media Land, aware of Volosovik's illegal activities and assisting him with legal issues and financial matters.
2. Companies (3):
ML Cloud: A sister company of Media Land, whose technical infrastructure is often used in conjunction with Media Land to support ransomware activities and DDoS attacks.
Media Land Technology (MLT) and Data Center Kirishi (DC Kirishi): Wholly owned subsidiaries of Media Land, listed under sanctions by OFAC due to being controlled by or acting on behalf of Media Land.
Aeza Group: Covert expansion after sanctions
Aeza Group (Aeza) is also headquartered in Saint Petersburg, Russia, focusing on bulletproof hosting services, long-term providing infrastructure support for ransomware and information theft organizations such as Meduza, Lumma, BianLian, and RedLine, and hosting the Russian dark web drug platform BlackSprut, making it a critical infrastructure hub in the cybercrime ecosystem. Because its services have been used to attack the US defense industrial base, technology companies, and victims worldwide, the US Department of the Treasury's Office of Foreign Assets Control (OFAC) has listed Aeza and its affiliated entities on the sanctions list as of July 2025.

After being sanctioned, Aeza did not cease operations but initiated a series of covert expansions and evasion measures. Its leadership attempted to obscure actual control relationships and evade regulatory tracking by registering new shell companies, replacing brand names, setting up offshore shell companies, and migrating IP infrastructure. Some newly established entities continue to provide hosting support for similar malicious activities, serving ransomware gangs, information theft program operators, and the infrastructure operations of dark web markets.
In this round of sanctions, the US, UK, and Australia further clarified their targeting of Aeza's evasion system, including key individuals involved in related operations and assisting in evading regulation, as well as the shell entities they control, specifically including:
1. Individuals (2):
Maksim Vladimirovich Makarov (Makarov): Aeza's new director, responsible for making key decisions to facilitate Aeza's sanction evasion.
Ilya Vladislavovich Zakirov (Zakirov): Helped establish new companies and payment methods to cover up Aeza's ongoing activities.
2. Companies (3):
Hypercore Ltd. (Hypercore): A shell company set up by Aeza Group in the UK to migrate IP infrastructure and evade sanctions.
Smart Digital Ideas DOO (Smart Digital) and Datavice MCHJ (Datavice): Companies from Serbia and Uzbekistan, respectively, used by Aeza to evade sanctions and establish technology infrastructure without public association with the Aeza brand.
Summary and Recommendations
The joint sanction actions of the US, UK, and Australia clearly convey a message: as global cooperation against ransomware and high-risk cybercrime deepens, law enforcement is extending its focus from individual attackers to the critical infrastructure they rely on. The bulletproof hosting services provided by Media Land, Aeza Group, and their affiliated entities are secret support points for the continued operation of numerous cybercriminal activities. As the scope of sanctions expands, businesses and institutions need to simultaneously strengthen their internal compliance systems to avoid assuming additional risks due to contact with sanctioned infrastructure, contaminated funds, or affiliated entities.
In practical operations, on-chain risk monitoring and compliance management have become core aspects. Businesses can leverage technology to conduct real-time reviews of transaction addresses, sources of funds, and affiliated entities, thereby achieving proactive risk control. Based on years of blockchain security research and risk control practices, the anti-money laundering tracking and analysis system MistTrack under SlowMist has provided stable and reliable on-chain risk control support and robust AML compliance solutions for multiple exchanges, businesses, and developers, offering accurate data analysis, real-time risk monitoring, and comprehensive compliance support.
MistTrack can:
Detecting the source of funds to screen whether they come from sanctioned wallets or high-risk addresses, avoiding the acceptance of contaminated funds;
Conducting address reviews before transactions to prevent dealings with sanctioned or suspicious funds, reducing the risk of freezing.
Currently, MistTrack has accumulated over 400 million address labels, more than 1,000 entities, over 500,000 threat intelligence data, and over 90 million risk addresses, providing solid support for digital asset security and combating money laundering crimes. For more on on-chain anti-money laundering practical experience, refer to the case sharing article: Case Sharing|MistTrack assists virtual asset funds in achieving anti-money laundering compliance and risk control. For more information, please visit https://aml.slowmist.com, and click to read the original article for direct access.
Related links:
https://home.treasury.gov/news/press-releases/sb0319
https://www.cyber.gov.au/sites/default/files/2025-01/Bulletproof-hosting-providers.pdf



