
Reports indicate that holders of the World Liberty Financial (WLFI) token are having their tokens drained, while a security expert points to a phishing exploit related to Ethereum contracts.
Holders of governance tokens in the World Liberty Financial (WLFI) project are facing an exploitation attack based on the EIP-7702 vulnerability in the Ethereum network, according to what the founder of cybersecurity company SlowMist, Yu Shian, said.
The Pectra upgrade for the Ethereum network launched in May improved EIP-7702, which allows external accounts to temporarily act like smart contract wallets, enabling delegation of execution rights and performing batch transactions, features aimed at enhancing user experience.
Shian explained in a post on platform X on Monday that hackers exploit this update by planting a pre-controlled address within the victims' wallets, and then quickly 'hijacking' the tokens upon deposit, specifically targeting WLFI tokens in this case.
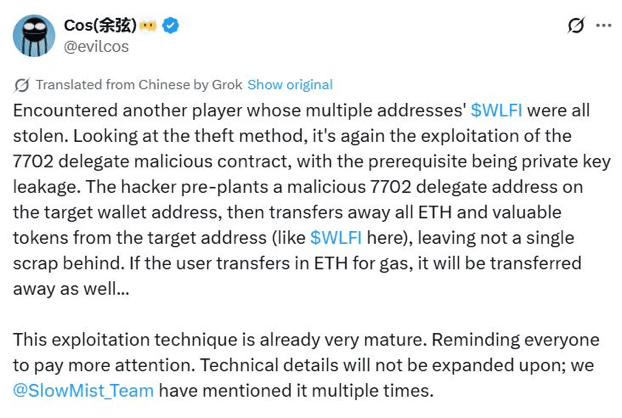
"We encountered another case where all WLFI tokens were stolen from multiple addresses of a single user. Given the method of the theft, it is clear that it is an exploit of a malicious delegation contract based on EIP-7702, with the prerequisite being the leakage of the private key." Yu Shian
The token World Liberty Financial (WLFI), backed by Donald Trump, began trading Monday morning with a total supply of 24.66 billion tokens.
How is the process done?
Before the official launch, a user on platform X reported on August 31 that his friend lost all his WLFI tokens after converting Ether (ETH) to his wallet.
In his response, Shian clarified that this is a typical case of what he described as a "classic EIP-7702 phishing exploit," where the private key is stolen, and the attacker plants a malicious delegation contract within the victim's wallet address linked to the key.
In a previous post, Shian noted that private keys are often stolen through phishing attacks.
He said:
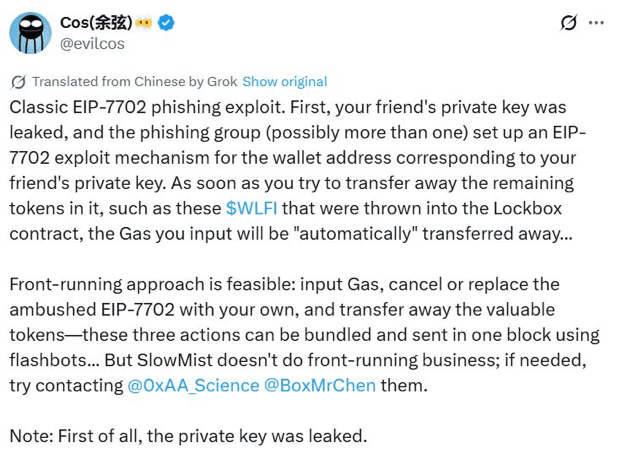
"As soon as you try to transfer what's left of the tokens in the wallet, such as WLFI locked in a Lockbox contract, the gas fees you pay will be automatically transferred to the attacker."
Shian suggested a solution consisting of "cancelling or replacing the planted EIP-7702 contract with one of your own," in addition to transferring tokens from the hacked wallet as quickly as possible.
WLFI users are discussing thefts in forums
Some users reported similar issues in WLFI forums.
A user named hakanemiratlas stated that his wallet was hacked last October, and he is now worried about his WLFI tokens.
"I was only able to transfer 20% of my WLFI tokens to a new wallet, and it was a stressful race with the hacker. Even sending Ether for gas fees was risky, as it could be stolen immediately."
He added:
"80% of my tokens are still stuck in the hacked wallet, and I am very concerned that the hacker will transfer them as soon as they are unlocked."
Another user named Anton stated that many are facing the same issue due to the way the initial offering was executed:
"The wallet used to join the WLFI whitelist is the same one required to participate in the presale. Once the tokens arrive, the bots will steal them before we can transfer them to a secure wallet."
Anton urged the WLFI team to consider a direct transfer option for tokens as an alternative solution.
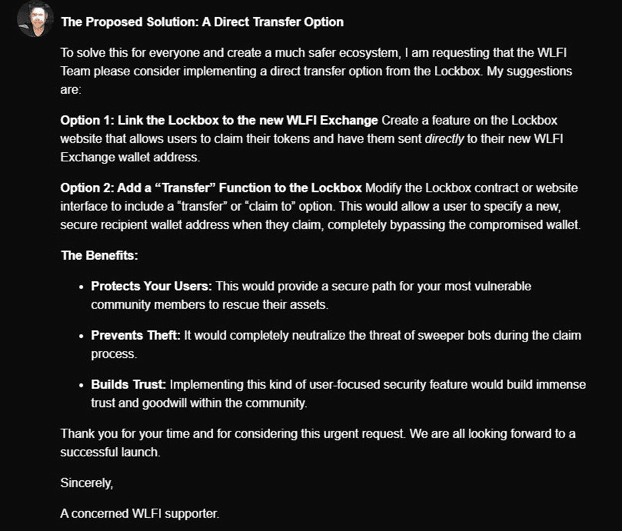
A user under the alias Anton mentioned that individuals who registered for the WLFI whitelist and had their wallets hacked later face the risk of losing their tokens.
Fraudsters target the WLFI launch
Numerous scams related to WLFI emerged before and after the token launch. The analytics company Bubblemaps identified several cloned smart contracts that mimic existing crypto projects.
Meanwhile, the WLFI team warned that they do not communicate with users via direct messages on any platform, and the only official support channels are via email:
"If you receive a direct message claiming to be from our team, it is fraudulent and should be ignored. If you receive an email, always verify that it is from one of our official domains before responding." WLFI Team
#WLFI #WLFCoin #WLFIfamily #BinanceSquareFamily #BinanceSquare
