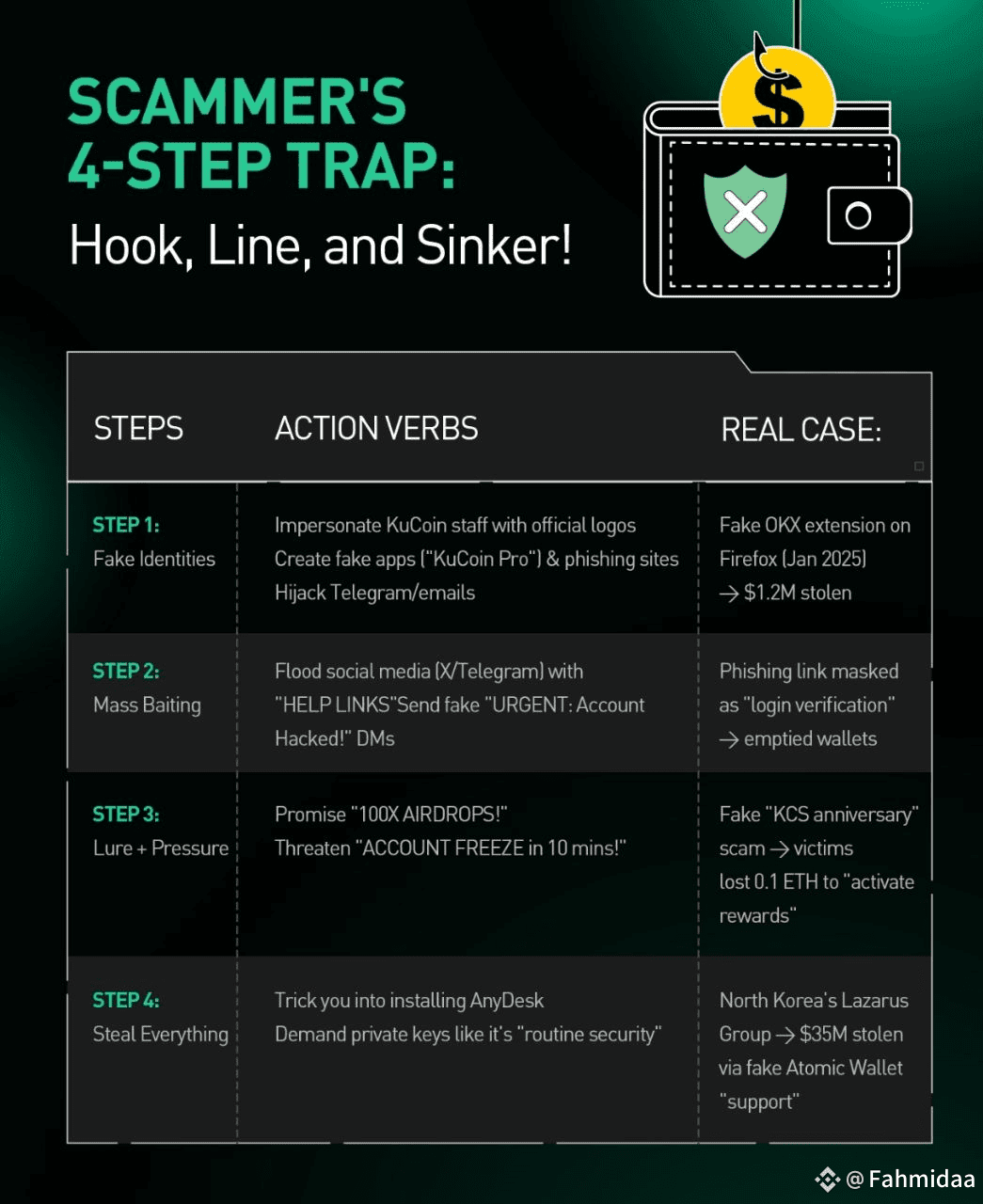
A Russian hacking group known as GreedyBear has stolen over $1 million in cryptocurrency by launching a wave of malicious Firefox browser extensions and fake MetaMask wallet apps. These scams are highly sophisticated and have been active for at least five weeks, targeting unsuspecting users across the crypto space.
🧠 What’s Happening?
GreedyBear has deployed 150+ fake browser extensions—many of which were available on Firefox’s official add-on store. These extensions are designed to look like helpful wallet tools or security apps, but they’re actually built to steal your seed phrase, private keys, and other sensitive data.
Once installed, these extensions silently collect your wallet info and send it to the hackers. Victims lose access to their funds instantly, and recovery is nearly impossible.
How They’re Tricking People
The group isn’t just relying on fake extensions. They’re also creating fake MetaMask wallet apps and phishing websites that mimic trusted platforms. One of their tactics includes fake savings ads that look like they’re from legit companies like Wise. These ads redirect users to cloned sites that ask for wallet access or seed phrases.
It’s a full-blown social engineering campaign, and it’s working.
Who Else Is Involved?
Authorities like the U.S. Department of Homeland Security have flagged GreedyBear as part of a larger network of Russian cybercrime groups. Others in this network include BlackSuit and Royal, both known for ransomware attacks and crypto theft.
These groups are evolving fast—using smarter tools, better branding, and more convincing scams.
🛡️ What You Should Do Right Now
If you use Firefox or MetaMask, take action immediately:
- ✅ Audit your browser extensions
Go to your browser settings and check every installed extension. If you don’t recognize one, remove it.
- ✅ Delete anything suspicious
Even if it looks legit, if you didn’t install it yourself or it’s not from a verified source, get rid of it.
- ✅ Verify URLs carefully
Always double-check the website address before entering wallet info. Fake sites often use slight misspellings or extra characters.
- ✅ Use official wallet links only
Download wallets and extensions from the official websites—not from ads, social media, or random links.
- ✅ Never share your seed phrase
No legit company will ever ask for it. If someone does, it’s a scam.
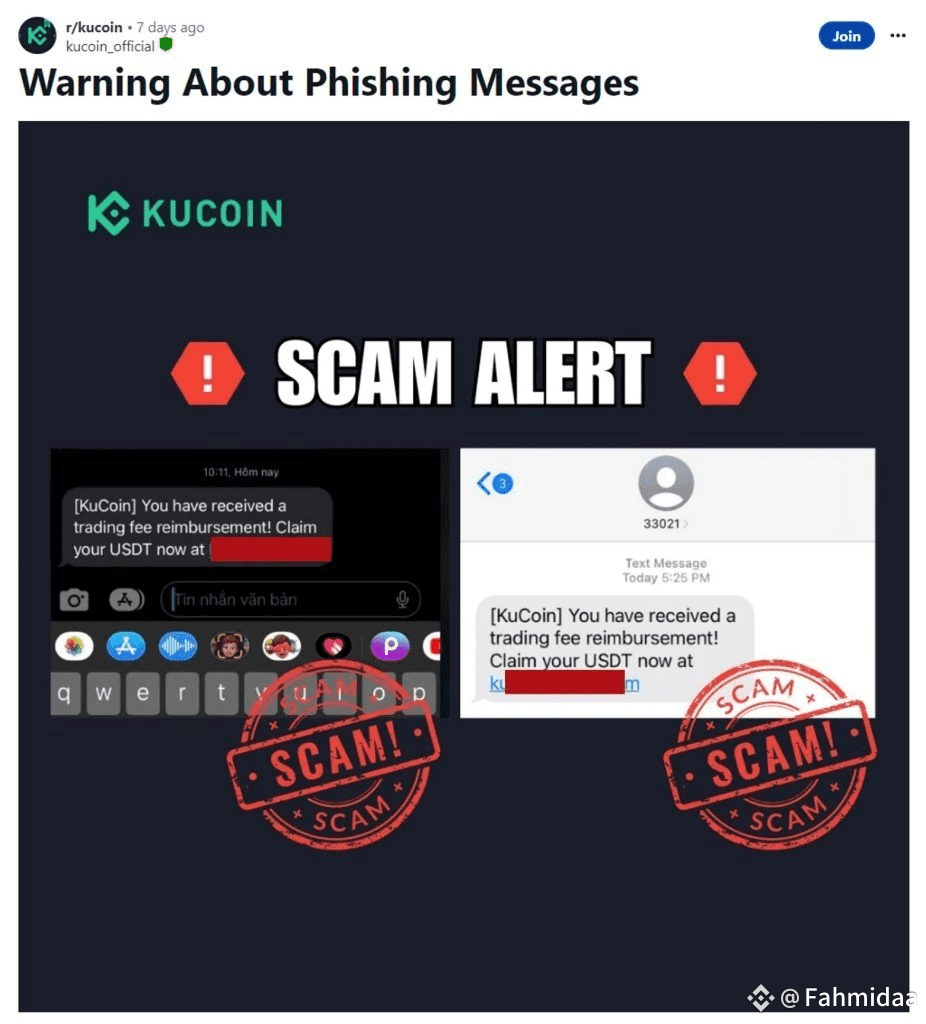
Warnings from the Crypto Community
Platforms like KuCoin and CoinMarketCap are sounding the alarm:
Think your browser extensions are safe? Think again. Dozens of fake wallet add-ons were recently found on Firefox’s official stores.” — @kucoincom
CoinMarketCap will NEVER DM you first. If you receive a message claiming to be from CMC & asking for funds, it's a scam!” — @CoinMarketCap
These warnings are part of a growing effort to educate users and prevent further losses.
🔍 Why This Matters
Crypto is built on trust and decentralization—but that also means you’re responsible for your own security. Hackers like GreedyBear exploit that trust by creating tools that look helpful but are actually dangerous.
The fact that these extensions made it onto Firefox’s official store shows how sneaky and convincing they are. It’s a wake-up call for everyone in the space.
🌐 Global Impact
This isn’t just a one-off attack. It’s part of a global surge in crypto-related cybercrime, especially from groups linked to Russia and Eastern Europe. These hackers are targeting:
- Retail investors
- NFT collectors
- DeFi users
- Crypto influencers
- Even institutional wallets
They’re using everything from browser exploits to fake customer support chats to drain wallets.
🧠 Stay Smart, Stay #SAFU
Here’s how to protect yourself and your community:
★Use hardware wallets for large amounts
★ Educate your friends and followers Clean up your browser regularly
★Test unknown tools in a sandbox wallet
★Follow trusted sources for updates
#CryptoScamAlert #MetaMaskHack #BrowserSecurity #PhishingScam
