Solo is building a 'trusted anonymous' on-chain identity system based on its original zkHE architecture, hoping to break the long-standing 'impossible triangle' that has plagued Web3, achieving a balance among privacy protection, identity uniqueness, and decentralized verifiability.
Recently, the Web3 identity layer project Solo announced the completion of a $1.2 million Pre-Seed round of financing, led by Draper Associates, with Velocity Capital participating, and strategic angel investments from RISC Zero founder Brian Retford and Caldera founder Matt Katz. After this round of financing, Solo has further become a focal project in the Web3 identity track.
Focusing on the fundamentals of this project, on one hand, the core team's strength is impressive. CEO Edison studied at Yale School of Management, where he co-founded the Yale Blockchain Society and led the first Yale Blockchain Summit. To focus on advancing the Solo project, Edison chose to drop out and dedicate himself full-time to research and development. The other two co-founders, Stephen and Sissi, are both professors at Shenzhen University with deep accumulations in blockchain and artificial intelligence—Stephen is one of the early contributors to the Ethereum Foundation, while Sissi has achieved significant results in AI research and practical applications.
In terms of technical pathways, Solo centers on its unique zkHE (Zero-Knowledge Homomorphic Encryption) solution, constructing an identity architecture that achieves dynamic balance among privacy protection, identity uniqueness, and decentralized verifiability. Against the backdrop of frequent Sybil attacks, the lack of user reputation systems, and difficulties in compliance access in the current Web3 ecosystem, the solution proposed by Solo may have significant reference and leading significance.
This article will deeply analyze the new paradigm of the identity layer represented by Solo from multiple dimensions, including market structure, technical pathways, and narrative positioning.
01 Long-Term Absence of Identity Layer in the Web3 World
Although the infrastructure in the Web3 field is continuously improving at a rapid pace, the 'identity layer', as a key module supporting trust and participation, has long been in a state of absence.
In fact, from data labeling, behavior scoring to protocol interaction and community governance, a large number of key tasks in Web3 rely on 'human input' as an effective data source. However, from the perspective of on-chain systems, users are often just wallet addresses made up of letters and numbers, lacking structured individual characteristics and behavior labels. Without additional identity layer mechanisms for support, the crypto-native world can hardly establish a credible user profile, let alone achieve reputation accumulation and credit assessment.
The absence of an identity layer directly gives rise to one of the most common and challenging issues in Web3, namely Sybil attacks. In various incentive activities that rely on user participation, malicious users can easily forge multiple identities to repeatedly claim rewards, manipulate votes, and pollute data, rendering mechanisms that should be driven by 'real human participation' completely ineffective. For instance, Celestia faced an airdrop in 2023 where as much as 65% of the 60 million $TIA was obtained by bot or Sybil accounts, and similar phenomena were widely observed in the distribution processes of projects like Arbitrum and Optimism.
Although some projects attempt to introduce 'anti-Sybil' mechanisms to filter abnormal behaviors, the reality is that such means often misjudge real users, while real bots can easily bypass the rules. For example, the anti-Sybil rules for EigenLayer's airdrop previously sparked controversy, as some normal users were mistakenly identified as Sybil attackers and were excluded from the airdrop, causing disputes. Therefore, we see that in the absence of a strong identity foundation, on-chain incentive distribution is always difficult to achieve fairness, efficiency, and sustainability.
In other vertical scenarios of Web3, the issues brought about by the absence of identity are also significant.
For example, in the DePIN field, the phenomenon of fraudulent addresses submitting fake data to obtain incentives is common, disrupting the authenticity of data and directly affecting the usability and trust foundation of the network. Similarly, in GameFi, the behavior of multi-accounting to complete tasks and collect rewards in bulk severely disrupts the balance of the in-game economic system, leading to the loss of real players and the failure of project incentive mechanisms.
In the AI field, the absence of an identity layer has also brought profound impacts. Currently, large-scale AI model training increasingly relies on 'human feedback' (such as RLHF) and data labeling platforms, and these tasks are often outsourced to open communities or on-chain platforms. However, under the premise of lacking 'human uniqueness' protection, the phenomenon of scripts simulating behavior in bulk and robots forging input is becoming increasingly serious, not only contaminating training data but also severely weakening the model's expressiveness and generalization ability.
Previously, in a study called Best-of-Venom, researchers successfully induced RLHF models to deviate during training and output significantly manipulated results merely by injecting 1–5% of 'malicious feedback comparison data'. Even a very low proportion of these forged human preference data is enough to compromise the robustness of the model and affect final generation quality. More importantly, due to the inability to effectively constrain participant identities, the system can hardly identify or block such cleverly disguised manipulation behavior from the source.
Furthermore, in the absence of an effective identity layer, the KYC mechanisms, credit scoring systems, and behavioral profiles widely used in the Web2 world can hardly be mapped to the on-chain environment in a native and trustworthy manner. This not only limits institutions' participation in Web3 while ensuring user privacy but also keeps the on-chain financial system in a state of identity vacuum. A representative example is that the DeFi lending model has long relied on over-collateralization mechanisms, making it difficult to touch broader uncollateralized credit lending scenarios, severely limiting user coverage capabilities and capital efficiency.
The same issues also arise in Web3 advertising, social, and other fields. Due to the lack of verifiable user identities and behavioral preferences, mechanisms such as precise recommendations and personalized incentives are difficult to establish, further limiting the deep operational capabilities and commercialization space of on-chain applications.
02 Exploring the Web3 Identity Layer
In fact, there are currently dozens of Web3 identity layer solutions on the market, such as Worldcoin, Humanode, Proof of Humanity, Circles, idOS, ReputeX, Krebit, and others. These solutions are all attempting to fill the gap in the Web3 identity layer, which we can roughly categorize into four types:
Biometric types
Biometric solutions are typically characterized by biometric technologies (such as iris, facial recognition, fingerprints) to ensure identity uniqueness. These solutions often possess strong resistance to Sybil attacks, with representative projects including Worldcoin, Humanode, Humanity Protocol, ZeroBiometrics, KEYLESS, HumanCode, and others.
We see that such solutions often violate user privacy due to the collection of biometric data, generation of hashes, and other paths, leading to relatively weak aspects in privacy protection and compliance dimensions. For example, Worldcoin has faced regulatory scrutiny in multiple countries due to iris data privacy issues, including EU GDPR compliance issues.
Social trust types
Social trust solutions usually place great emphasis on 'user sovereignty', focusing on social trust networks and open verification, often centering around elements like Web of Trust and reputation scoring. They establish trusted identity networks through social relationship graphs, community mutual recognition, and human recommendations. Representative projects include Proof of Humanity, Circles, Humanbound, BrightID, Idena, Terminal 3, ANIMA, and others.
Such solutions can theoretically achieve high decentralization, potentially expanding trust networks based on community consensus and incorporating reputation governance mechanisms. However, we see that these solutions often struggle to guarantee identity uniqueness, making them vulnerable to Sybil attacks, with poor scalability in familiar networks, and are thus easily limited by issues such as identity forgery or community cold start problems. Proof of Humanity had previously adjusted its verification mechanism due to bot issues.
DID aggregation types
DID aggregation solutions can usually further construct a composable on-chain identity structure by integrating Web2 identity/KYC data, Verifiable Credentials (VCs), and other external credentials. These solutions are highly compatible with existing compliance systems, and most solutions can also support users in controlling data sovereignty, making it easier for some institutions to adopt. Some representative projects include Civic, SpruceID, idOS, SelfKey, Fractal ID, and others.
However, for DID aggregation solutions, identity uniqueness is similarly weak. We see that most of them highly depend on external data sources, such as Web2 KYC or intermediary data providers, so the degree of decentralization is relatively limited, and the architecture is comparatively complex. Although some projects like SpruceID are exploring privacy protection through ZK-SNARKs, most solutions in this sector still have not resolved issues related to privacy verifiability.
Behavioral analysis types
Behavioral analysis solutions are typically based on on-chain address behavior, interaction trajectories, task records, and other data, using graph algorithms to build user profiles and reputation systems. Representative projects include ReputeX, Krebit, Nomis, Litentry, WIW, Oamo, Absinthe, and Rep3.
The advantage of modeling by address is good privacy protection, as it naturally adapts well to the on-chain ecosystem without requiring additional input. However, on the other hand, due to the inability to connect with users' real identities, the lack of identity uniqueness leads to the prominent problem of multiple addresses for one person, making it susceptible to Sybil behavior interference, and can only establish locally labeled identities, resulting in data quality distortion.
Therefore, in summary, the current practice of existing identity layer solutions generally falls into an impossible triangle dilemma:
That is, privacy protection, identity uniqueness, and decentralized verifiability are often difficult to balance simultaneously. At the same time, we find that other identity mechanisms, except for biometric solutions, generally struggle to effectively guarantee 'identity uniqueness'.
Thus, biometric features are often seen as the most definitive elements in identity layers and have been practically verified in multiple projects. However, to build a truly trustworthy identity system, relying solely on biometric recognition is indeed insufficient to solve the balance issue between privacy protection and decentralization.
In light of the above issues, Solo also chose biometric feature recognition as the fundamental means of ensuring user identity uniqueness and, based on cryptography, proposed a relatively unique technical path further addressing the balance dilemma of 'privacy protection' and 'decentralized verifiability'.
03 Deconstructing Solo's Technical Solutions
As mentioned above, using biometric feature recognition for the identity layer can effectively prove user uniqueness, but the biggest challenge is how to ensure data privacy and verifiability at any time and place.
Solo's solution is based on the zkHE architecture, which integrates Pedersen commitments, Homomorphic Encryption (HE), and Zero-Knowledge Proof (ZKP). Users' biometric features can undergo multi-layer encryption processing locally, enabling the system to generate verifiable zero-knowledge proofs and submit them on-chain without exposing any raw data, thus achieving both unforgeability of identity and verifiability under privacy protection.
zkHE Architecture
In the zkHE architecture of Solo, the authentication process consists of a dual encryption defense: Homomorphic Encryption (HE) and Zero-Knowledge Proof (ZKP). The entire process is completed locally on the user's mobile device to ensure that sensitive information is not leaked in plaintext.
Homomorphic encryption
The first layer of encryption defense is homomorphic encryption. Homomorphic encryption is a cryptographic scheme that allows calculations to be performed directly on encrypted data, and as long as the decryption result is completely consistent with the plaintext operation, it represents the correctness and availability of the data itself.
In zkHE, the system inputs the promised biometric features further in homomorphic encryption form into the circuit, executing matching and comparison logic operations throughout without the need for decryption.
The 'comparison' here essentially calculates the distance between the biometric feature vectors of the registered and current verification data to determine whether the two sets of data come from the same person. This distance calculation process is also completed in an encrypted state, and the system subsequently generates a zero-knowledge proof based on the comparison result, indicating 'whether the distance is less than the threshold', thus completing the judgment of 'whether it is the same person' without exposing the original data or distance values.
This processing method aims to achieve trusted computation under the premise of privacy protection, ensuring that the identity verification process is verifiable, scalable, and always confidential.
Zero-Knowledge Proof
After completing the aforementioned encryption computations, Solo generates a zero-knowledge proof locally for submission on-chain. This ZKP proves 'I am a unique and real human', but does not disclose any original biometric information or intermediate computation details.
Solo itself employs the efficient Groth16 zk-SNARK as the proof generation and verification framework, generating concise yet robust ZKP with minimal computational overhead. Verifiers simply need to verify this proof to confirm identity validity, and the entire process does not require access to any sensitive data. Ultimately, this ZKP is submitted to a dedicated Layer2 network, SoloChain, for verification by on-chain contracts.
In addition to privacy and security guarantees, Solo's performance in verification efficiency is also particularly outstanding. Thanks to the streamlined design of the cryptographic process and the introduction of high-performance primitives, Solo can achieve low-latency, high-throughput identity verification experiences on mobile devices, providing strong technical support for large-scale user adoption and on-chain integration.
Verification efficiency
The Solo solution itself possesses high verification efficiency, partly due to its high optimization and adaptation of cryptographic algorithms.
In fact, there are many cases of introducing cryptography to guarantee privacy and data security in the Web3 identity layer track, especially focusing on ZK, but currently, truly implementable solutions are rare, ultimately due to
In terms of zero-knowledge proof construction, Solo chose the highly efficient Groth16 zk-SNARK as the main framework. This system has a very small proof size (about 200 bytes) and can achieve millisecond-level verification on-chain, significantly reducing interaction latency and storage overhead.
Recently, the Solo team conducted experiments on its cryptographic model as shown in the figure below. When faced with higher-dimensional biometric feature data (Biometric Vector Length), the zkHE architecture adopted by Solo (HE + ZKP) significantly outperformed traditional ZKP solutions in proof generation time and total authentication duration. Under 128-dimensional data conditions, the authentication time for traditional ZKP exceeds 600 seconds, while the Solo solution remains virtually unaffected, consistently maintaining within seconds.
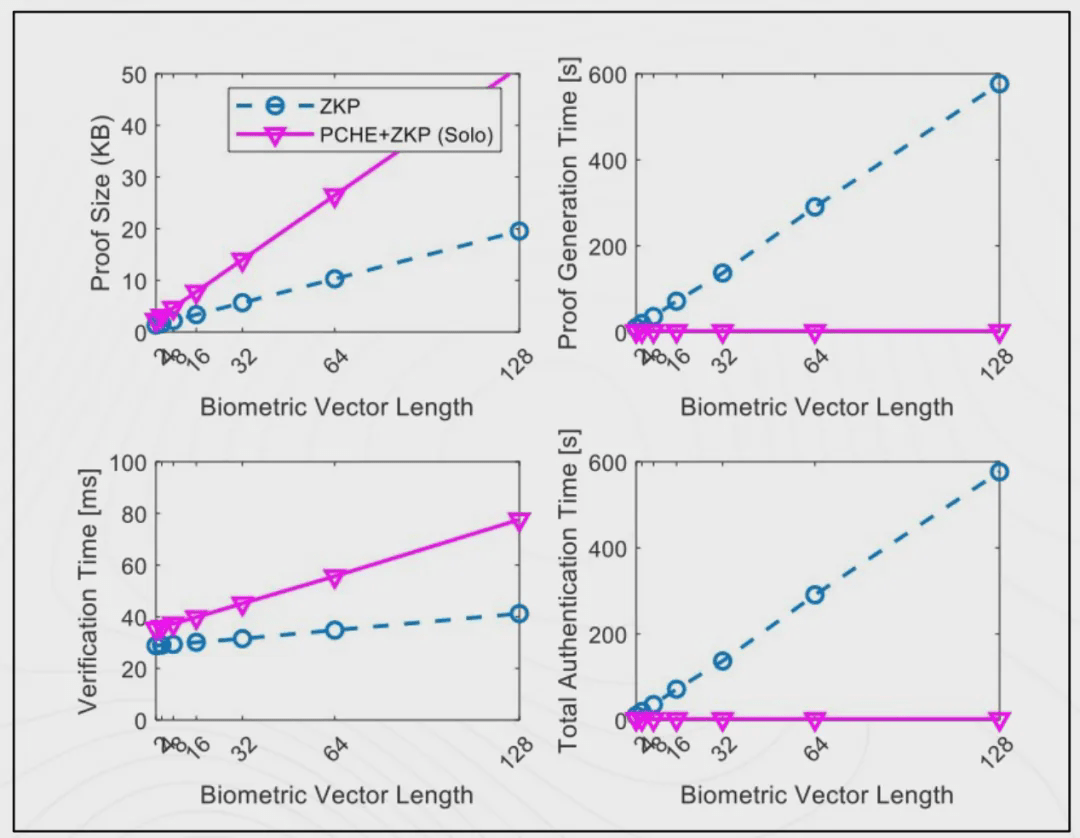
Furthermore, although the proof size of Solo is slightly larger than traditional solutions in some vector dimensions, its overall verification time remains controlled within the range of 30–70ms, which is sufficient to meet the latency and performance requirements of most high-frequency interaction scenarios (such as chain games, DeFi logins, L2 real-time authentication, etc.).
Moreover, Solo has also made significant optimizations in client performance.
Its zkHE verification process (including Pedersen commitment generation, homomorphic encryption processing, and ZKP construction) can all be completed locally on ordinary smartphones. Practical results show that the overall computation time on mid-range devices is 2–4 seconds, which is sufficient to support smooth interactions for most Web3 applications without relying on any proprietary hardware or trusted execution environments, greatly reducing the threshold for large-scale deployment.
04 A New Attempt to Break the 'Impossible Triangle' of the Web3 Identity Layer
From a global perspective, Solo actually provides a new path to break the 'impossible triangle' of the Web3 identity layer, achieving a technical balance and breakthrough among privacy protection, identity uniqueness, and usability.
At the privacy level, the zkHE architecture allows all users' biometric features to undergo homomorphic encryption and ZKP construction locally, without uploading or decrypting original data throughout the entire process, thereby completely avoiding the risk of privacy leakage and eliminating reliance on centralized identity providers.
In terms of identity uniqueness, Solo confirms whether the current verifier is the same person as the historical registration record through a feature vector distance comparison mechanism in an encrypted state, without leaking the data structure. This builds the foundational identity constraint of 'each address corresponds to a real unique human', which is the one account per person (1P1A) emphasized by Solo.
In terms of usability, Solo ensures that all computational tasks can be completed on ordinary mobile devices through fine optimization of the zk proof process—practical tests show that verification generation time is usually controlled within 2–4 seconds, while the on-chain verification process can be completed in milliseconds and is fully decentralized, meeting the real-time requirements of applications including chain games, DeFi, L2 logins, and more.
It is worth mentioning that Solo has reserved compliance docking interfaces within its system design, including an optional bridging module that supports integration with on-chain DID and KYC systems, as well as the capability to anchor verification statuses to a designated Layer1 network in specific scenarios. Therefore, in the future, when landing in the compliance market, Solo is expected to meet the requirements for identity verification, data traceability, and regulatory cooperation while maintaining privacy and decentralized characteristics.
From a broader perspective, we mentioned earlier that the current Web3 identity solutions can roughly be divided into several technical paths, including reputation profile systems based on on-chain behavior, VC/DID architectures based on centralized certification, zk identity solutions emphasizing anonymity and selective disclosure, and some lightweight PoH protocols based on social networks and group certification.
In the diversified evolution of the Web3 identity track, the path based on biometric features + zkHE adopted by Solo can naturally form a complementary relationship with other solution paths.
Compared to solutions that focus on upper-layer identity labels or behavioral credentials, Solo's advantage lies in building a fundamental identity network that can complete 'human uniqueness verification' at the lowest level, possessing characteristics such as privacy protection, trustlessness, embedment, and sustainable verification, providing the foundational 'human real experience verification' for higher-level VC, SBT, social graphs, and more.
In a sense, Solo is more like the base consensus module in the identity stack, focusing on providing Web3 with the foundational infrastructure for human uniqueness proof with privacy protection capabilities. Its zkHE architecture can not only serve as a plug-in module for various DID or application front ends but also form a combined force with existing VC, zkID, SBT, etc., establishing a verifiable and composable real identity foundation for the on-chain ecosystem.
Therefore, Solo itself can be seen as the most fundamental 'trusted anonymous layer' infrastructure within the identity system, filling the industry's long-standing gap in '1P1A (One Person, One Account)' capabilities, further supporting higher-level applications and providing a foundation for compliance.
Currently, Solo has established partnerships with multiple protocols and platforms, including Kiva.ai, Sapien, PublicAI, Synesis One, Hive3, GEODNET, covering multiple vertical tracks such as data labeling, DePIN networks, and SocialFi games. These collaborations are expected to further validate the feasibility of Solo's identity verification mechanism and provide a real-world demand calibration feedback mechanism for its zkHE model, helping Solo continuously optimize user experience and system performance.

Summary
By building a trusted anonymous identity layer system for the Web3 world, Solo is laying the capability foundation for 1P1A and is expected to become an important underlying facility driving the evolution of on-chain identity systems and the expansion of compliant applications.
