Phishing groups are using a large number of addresses with leaked private keys for fraud, and the combination with EIP-7702 allows them to gain account management rights over addresses with leaked private keys. At the same time, these bait addresses have rich historical transaction records, making ordinary users easily let down their guard and transfer Gas due to the balance in the greedy bait addresses, leading to theft.
Case One

1. Address 0x000085bad5b016e5448a530cb3d4840d2cfd15bc has deployed multiple malicious Delegator contracts 0x930fcc, 0x1f0733, 0x9eece7 on ETH.
2. Afterwards, a large number of addresses with leaked private keys were authorized to a malicious Delegator contract via address 0x9d1ff3a11f7791c6bff9399aafd5a4eaffc83efb and automation scripts, completing the bait setup.
3. Spread these set bait addresses through various channels and social engineering methods to ordinary users, using accidental leaks of mnemonic phrases/private keys to induce users to think they only need to transfer a small amount of Gas to withdraw the remaining assets from the address.
 4. Due to unfamiliarity with the principles of 7702 and having directly obtained the address's private key, ordinary users often let down their guard, thinking that transferring a small amount of Gas isn't much of a risk, and are likely to be induced to transfer small amounts of Gas into the bait address. Since the bait address has already authorized the malicious 7702 Delegator, any small amount of Gas transferred will be immediately moved to address 0x000085.
4. Due to unfamiliarity with the principles of 7702 and having directly obtained the address's private key, ordinary users often let down their guard, thinking that transferring a small amount of Gas isn't much of a risk, and are likely to be induced to transfer small amounts of Gas into the bait address. Since the bait address has already authorized the malicious 7702 Delegator, any small amount of Gas transferred will be immediately moved to address 0x000085.
Case Two
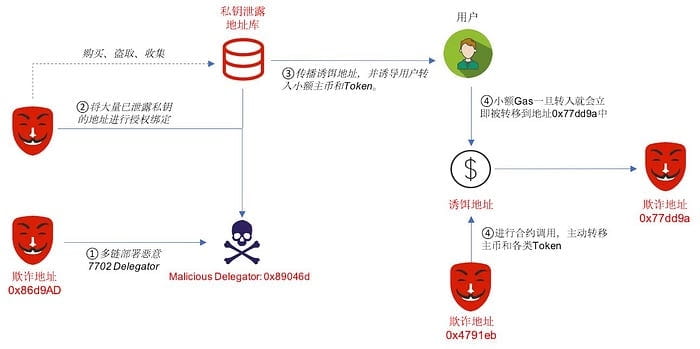
1. Address 0x86d9AD92FC3F69CC9C1a83aFF7834fEA27f1fFF2 has deployed malicious Delegator contracts on ETH, BSC, and Base.
0x89046d34E70A65ACAb2152C26a0C8e493b5ba629.
2. The malicious Delegator contract (0x89046d) in this case is more complex than case one; it can not only automatically transfer main coins but also call contracts through a third-party address (0x4791eb), actively transferring main coins and various tokens. Afterwards, the fraud gang used automation scripts to authorize a large number of addresses with leaked private keys to this malicious Delegator contract, completing the bait setup.
3. Spread these set bait addresses through various channels and social engineering methods to ordinary users, and induce users to transfer small amounts of main coins and tokens.
4. Because the bait address has authorized the malicious 7702 Delegator, any small amount of Gas and tokens transferred will be immediately moved to the address 0x77dd9a93d7a1ab9dd3bdd4a70a51b2e8c9b2350.
GoPlus Security Recommendations
1. Users need to remain vigilant; there is no free lunch. Any 'gifts' accompanied by private keys/mnemonic phrases should be regarded as risky. Do not easily sign authorizations out of curiosity or greed, and do not transfer to any unfamiliar addresses.
2. Similar to the Tron multi-signature scam and Solana permission change scam, fraudsters are expanding such scams based on EIP-7702 using addresses with leaked private keys to the EVM ecosystem.
For detailed information, please refer to:
https://academy.binance.com/en/articles/what-are-multisig-scams-and-how-to-avoid-them
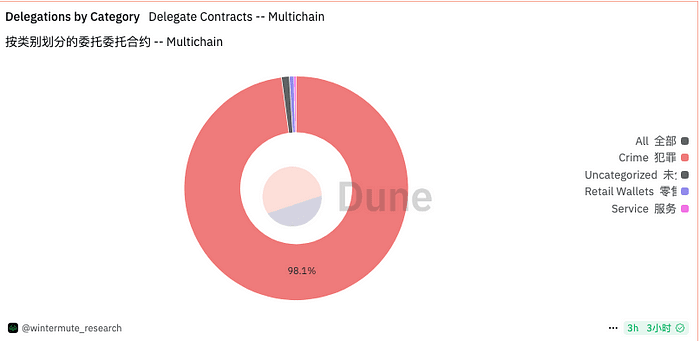
3. According to WinterMute, currently 98% of EIP-7702 authorizations point to multiple malicious Delegator contracts, from case one which can automatically transfer main coins, to case two which can automatically transfer main coins and tokens. The harm of such scams is rapidly expanding. GoPlus calls on all EVM ecosystem wallets, security, DEX, and related project parties to closely monitor 7702 security issues and timely intercept or remind users to avoid them in their products.
4. Learning about blockchain knowledge and maintaining a basic understanding of the operational mechanisms of different public chains can help you quickly identify similar scams. If you encounter problems, seek advice from GoPlus or professional security experts in a timely manner and do not act rashly.

