#链上安全 #土狗套路 #Write2Earn #SecurityInitiatives #Onchain
Main problem: A local dog $PSY. From the chain, the code is open source, and the LP was thrown into a black hole and lost its permissions. But in fact, there is a third-party address with a huge amount of tokens (far exceeding the initial supply of tokens), and then all of them were sold at once. However, this third-party address only has the record of selling (transferring out) $PSY, and there is no record of transferring in. In other words, this third-party address has a huge amount of tokens "out of thin air".
Appearance:
- $PSY Contract:
0x12b71eAC1e4ca3FB62A980C5FAE1442dD3Ea91Ea
- LP enters black hole tx:
0xedb721e1ef43f60cb63341a7ba57f1c769da40c27db47b7c8c5c196fcfe81c2d
- $PSY deployer gives up privileges tx:
0xf13c902d597c96bc02592541b4cf3cc03149f80a8f293eb0c34dcf0d202c68c3
Everything looks normal



Strange phenomenon:
About 20 hours later, a third-party address 0x61de69b7fe583E4547e67b4D0DA0cd9ecf526DC6 appeared, dumping 10000000000B of tokens directly to zero, exchanging 2 e, while the supply of $PSY is only 100M, which is equivalent to this address dumping 100B times the Total Supply. What's even more strange is that this address only has transfer-out records, and no trace of $PSY transfer-in:




The address 6DC6 also has only 6 transaction records, and none of them is the transfer of $PSY to this address. So how is it possible that this address can inexplicably have such a huge amount of tokens under the premise that LP has entered the black hole and given up its rights?

Analysis 1:👇👇👇
Turning our attention back to the contract code of $PSY, router and taxwallet_ are defined in Constructor. _router is a variable of type IUniswapV2Router02. IUniswapV2Router02 is the router contract interface of Uniswap V2, but it is initialized here to the value of the router parameter. The value of the router parameter can be found in "Constructor Arguments" below the source code, as shown below:


Analysis 2: 👇👇👇
So here _router will point to the Uniswap router contract address, which is 0x96e7AFd8829b2Ae5cCDaABeA04B63cBDf4961Cd8, but this is not the standard address of the Uniswap V2 mainnet router ⚠️⚠️⚠️The standard address is 0x7a250d5630B4cF539739dF2C5dAcb4c659F2488D! ⚠️⚠️⚠️
Analysis 3: 👇👇👇
In the token contract, we can see that _router is used in various functions, such as in the _transfer function, _router.transfer(to) and _router.Path(from), which are functions that call the Uniswap router contract (here, the 1Cd8 address). transfer and Path are not standard functions of the Uniswap router contract, but are custom functions created by the fraudster:
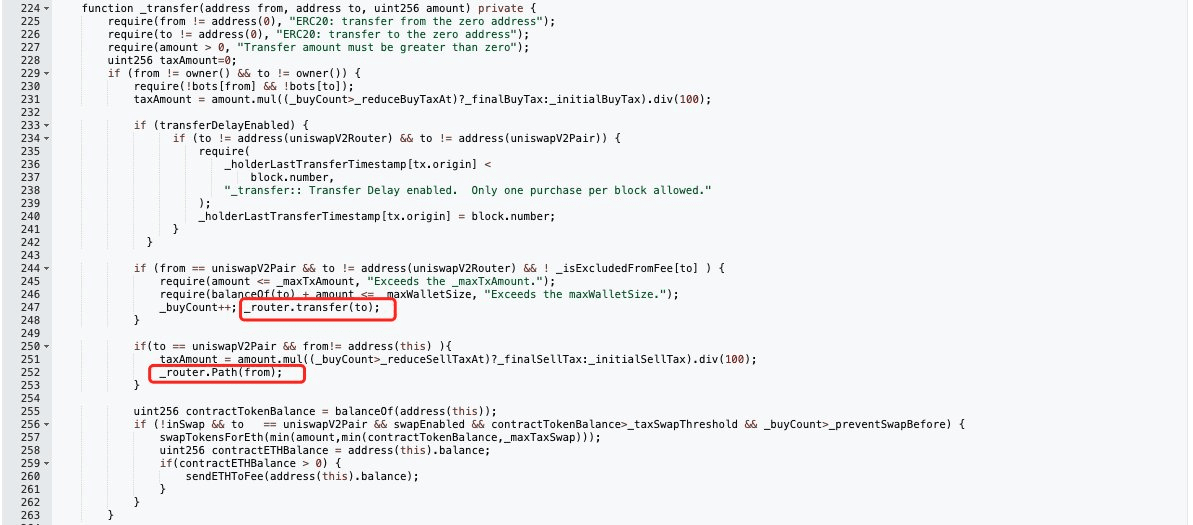
Analysis 4: 👇👇👇
So we traced back to the router contract address 0x96e7AFd8829b2Ae5cCDaABeA04B63cBDf4961Cd8, and found that the source code was not public. We found another contract with the same structure as this contract through byte codes, the address is 0x0D71773a5FD5E1Be5F28B8134797595B3E61e08b, the source code was not public either, and it was deployed by the same person. On July 8, $WPEPE was deployed to commit evil again:


Analysis 5: 👇👇👇
Going back to "Analysis 3", we can see that taxwallet_ is assigned the value 0x61de69b7fe583E4547e67b4D0DA0cd9ecf526DC6, which happens to be the address of the last large-scale sell-off. Going back to the source code of the $PSY contract, we can find that there are some malicious conditional statements and assignment operations after the _transfer function, such as setting the balance of the 6DC6 address to the maximum uint256 value in the red box:


Analysis 6: 👇👇👇
In addition, _router.transfer(to) and _router.Path(from) are called during the transfer process. The _router contract is not open source, so the deployer can arbitrarily modify it to achieve the purpose of concealing the truth. The above modification of the address balance and the call to _router caused the 6DC6 address to have an extra 10000000000B of $PSY:


Summary 1:👇👇👇
The deployer makes the token contract source code public on the surface, but in fact
1. Forge a closed-source router contract that you wrote and set it to the standard address of the Uniswap V2 mainnet router.
2. Secretly add malicious code after the Transfer function to modify the token balance of the tax address, and each time the _transfer function _router.transfer(to) and _router.Path(from) are executed, the malicious purpose is achieved.
Summary 2: 👇👇👇
This kind of routine cannot be identified by just observing the transaction path, and it is easy to be deceived by the seemingly open source token contract code. In fact, the real malicious router function is not open source, and there are many malicious code logics in the token contract. All we can do is to review the code more, but this will cost more time, and we may miss a lot of alpha, or we may escape. It is important to weigh the pros and cons!
Summary 3: 👇👇👇
For traders who don't understand the code, the risk of playing with the Earth Dog is really high. There are indeed too many chaotic market routines. I sincerely hope that everyone can be more cautious about the code. A friend DMed me and said that he was afraid that the questions he asked were too stupid, but there is no need to worry about this. If you have any questions, you can comment and study together!