A large-scale malware campaign is using fake ads to trap cryptocurrency asset users, potentially targeting over 10 million users worldwide.
A sophisticated large-scale malware distribution campaign named 'JSCEAL' is quietly targeting cryptocurrency asset users by impersonating popular trading applications. According to a report released by the cybersecurity company Check Point on July 29, this campaign has been active since at least March 2024, continuously evolving and leveraging online ads to lure users into installing malicious software disguised as nearly 50 reputable trading platforms such as Binance, MetaMask, and Kraken.
Cybersecurity researchers warn that the impact of this campaign is very large. In the first half of 2025 alone, Meta's advertising platform displayed around 35,000 malicious ads, reaching at least 3.5 million users in the European Union.
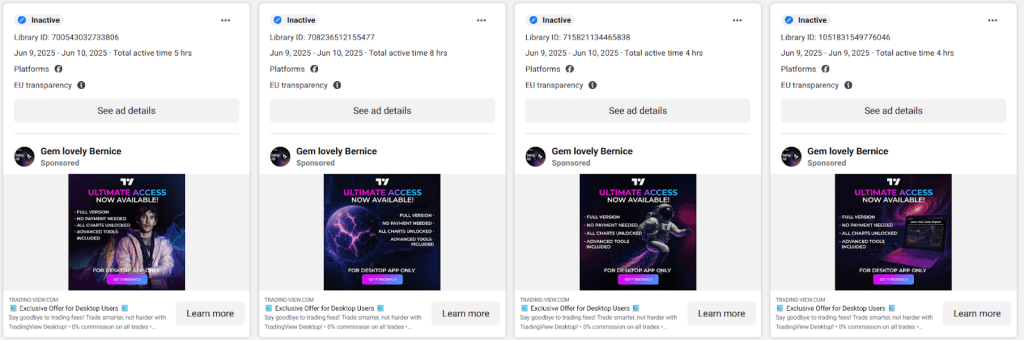 Malicious Facebook ads use the logo of the popular financial data site TradingView. Source: Check Point
Malicious Facebook ads use the logo of the popular financial data site TradingView. Source: Check Point
However, as the campaign also expands to impersonate financial institutions and exchanges in the Asia region – where a large number of social media users are concentrated – Check Point estimates that the number of targeted users globally could easily exceed 10 million. The company also notes that accurately determining the actual scale of the affected individuals is very difficult, and the number of ad impressions does not necessarily reflect the number of successfully attacked victims.
The danger of JSCEAL mainly comes from its ability to evade current security measures. When users click on fake ads, they will be redirected to websites designed with an interface identical to the real one to deceive the victim, while simultaneously activating malicious code. Because the components of the attack are closely coordinated and well-camouflaged, detecting and preventing the malware becomes increasingly complex.
After successful installation, the fake application will display an interface similar to the real application, making the victim believe that nothing unusual is happening, while the malware has been silently operating in the background.
Completely programmed in JavaScript, the JSCEAL malware does not require any additional user interaction to execute after installation. In addition to using compiled source code, JSCEAL also applies heavy obfuscation techniques, making it difficult and time-consuming for security experts to analyze and address.
The ultimate goal of this malware is to steal a large amount of sensitive information from the victim's device. JSCEAL collects all keystrokes to steal passwords, gain access to Telegram accounts, extract saved passwords and autofill data in the browser. Additionally, the malware also steals cookies, thereby identifying the websites that users frequently visit, while having the ability to take control of cryptocurrency wallet extensions like MetaMask.
In the face of these threats, Check Point recommends that users implement in-depth security solutions capable of detecting malware through behavior analysis to proactively prevent the execution of malicious JavaScript code.

