In the 1990s, MIT. Amit Sahai and Salil Vadhan raised a question that hardly anyone outside cared about:
"Is there a complete problem for statistical zero-knowledge?"
They eventually found the answer: the statistical difference problem (Statistical Difference, SD), also known as "Statistical Difference from Uniform" (SDU)
is one of the most core and representative problems in statistical zero-knowledge (SZK).

At that time, ZK was almost entirely 'computational':
✅ Built on mathematical challenges
❌ Security depends on the attacker's computing power
SZK is another model of privacy protection:
✅ Does not rely on computational assumptions
✅ Security comes from the information structure itself
✅ Immune to quantum attacks
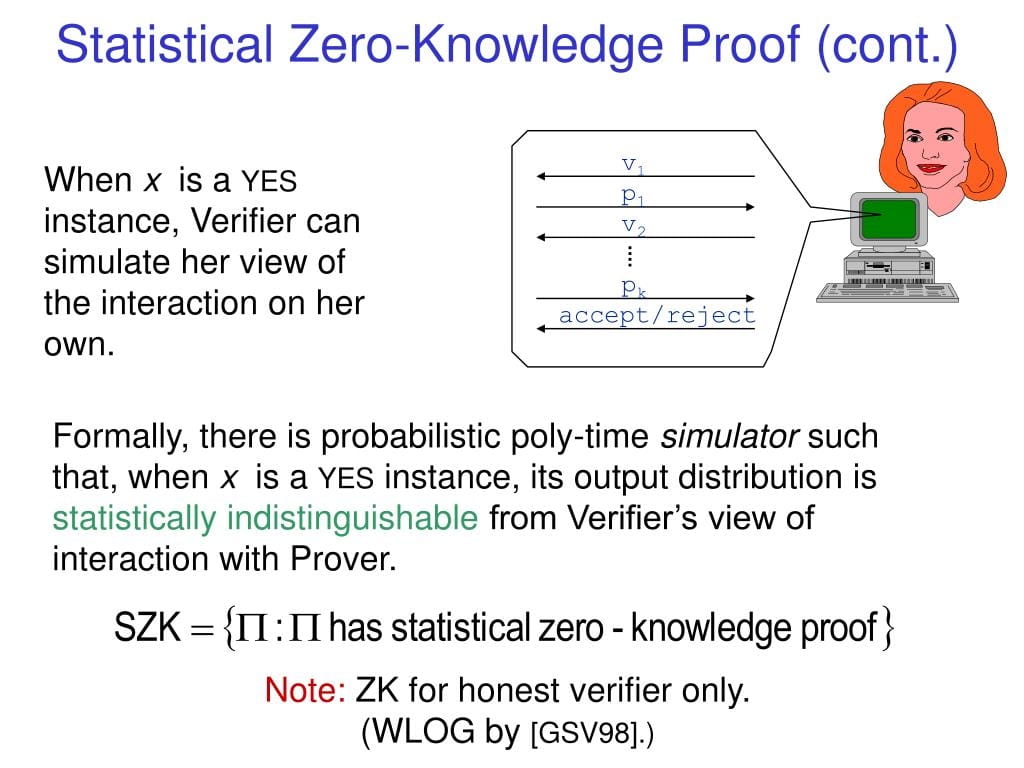
The classic paper by Sahai and Vadhan first proved: the statistical difference problem (SD) is a complete problem for SZK.
This means: all SZK problems can be reduced to SD
→ SZK has its own SAT
→ Zero-knowledge information security is no longer fragmented; theory and application are comprehensively unified.

SZK ≠ just theory
It does not rely on computational assumptions like RSA/ECC, but is based on information-theoretic security, making it more robust against quantum attacks.
From Zcash to zkSync, many privacy designs of ZK systems can be traced back to SZK/SD theory.
Quantum resistance, security analysis, cross-chain communication, MPC, DID—SZK is the universal language of modern zero-knowledge.

How far can the impact reach?
From zkRollup to zkML, wherever you see 'privacy + verifiable', there is a high probability that SZK is behind it.
Especially in cross-chain bridges, AI reasoning verification, and quantum-resistant protocols, SZK provides one of the few truly quantum attack-resistant privacy models.
Because: entropy does not lie.

At ZEROBASE, we believe:
Privacy should not rely on the algorithm being unbreakable, but should be based on provable mathematical mechanisms.
Protecting identity through authentication methods like zkLogin and zkEmail
Enhancing efficiency through TEE and off-chain computation
Using batch verification mechanisms to reduce on-chain costs
Sahai and Vadhan did not just solve a difficult problem.
They proved that even without encryption, we can still achieve true privacy protection.
This is not just a technical breakthrough, but a belief:
Where you can prove, there is no need for trust.