Written by: Tyler
Recently, I watched Jackie Chan's acclaimed new work (The Capture) and found an interesting segment—in which hundreds of billions of Hong Kong dollars in crypto assets are locked in a wallet protected by a 12-word mnemonic phrase, with only the last word unknown.
After watching, I tried it out and found that the 10th and 12th words were not in the standard mnemonic word list; it was clear that the screenwriter wrote it this way intentionally to prevent someone from replicating the wallet based on the plot, because similar scams on-chain are not uncommon.
Scammers will intentionally leak a "wallet address with a balance" (typically on the Tron chain, utilizing the Owner mechanism), luring people to deposit Gas, waiting for a catch; once the funds are deposited, they can never be retrieved.

But here’s an interesting point: the movie says there is only one word left unknown. In the real world, however, mnemonic phrases follow the BIP39 standard, which has a total of 2048 words. This means that brute-forcing the last word would yield at most 2048 possibilities. If we narrow it down further, for example, if the known starting letters are "es," the possibilities decrease even more, and it could be tested in a minute.
However, a more worthwhile question to reflect on beyond the movie is: what is the relationship between mnemonic phrases, private keys, and public keys? Why does losing the mnemonic phrase mean losing all assets?
One, mnemonic phrase: private key: public key/address = "keychain": "key": "house number"
A mnemonic phrase is a backup method that follows the BIP39 standard, consisting of 12, 18, or 24 words randomly selected and combined from a pool of 2048 English words through algorithms.
This set of mnemonic phrases is processed by the PBKDF2 algorithm to generate a seed, which then derives a series of private keys according to the BIP32/BIP44 path standards, thereby corresponding to a series of public keys/addresses.
A set of mnemonic words → Generate a series of private keys → Generate a series of public keys → Corresponding to a series of addresses
In other words:
Mnemonic phrase = keychain, and private keys are often in a one-to-many relationship; theoretically, a set of mnemonic phrases can derive thousands of private keys;
Private key = key, each private key corresponds to the usage rights of one address;
Public key/address = house number, can be made public, others can use it to transfer funds to you;
So mnemonic phrases can be viewed as your "keychain," and each private key is like a key that can open a door, used to sign and prove your control over a particular wallet address—when you initiate a transaction, you sign it with your private key, informing the entire network: "This transfer is authorized by me."
Two, can I pick mnemonic words myself?
So some friends might wonder: Can I assemble my own 12 words? For example, birthday, favorite English words, idol names, making it more personalized.
The answer is: yes, but it is extremely dangerous.
Because random numbers generated by computers are truly random, while humans tend to choose words with patterns (common words, preferred terms, order preferences), this significantly reduces the search space, making your mnemonic phrase easier to guess.
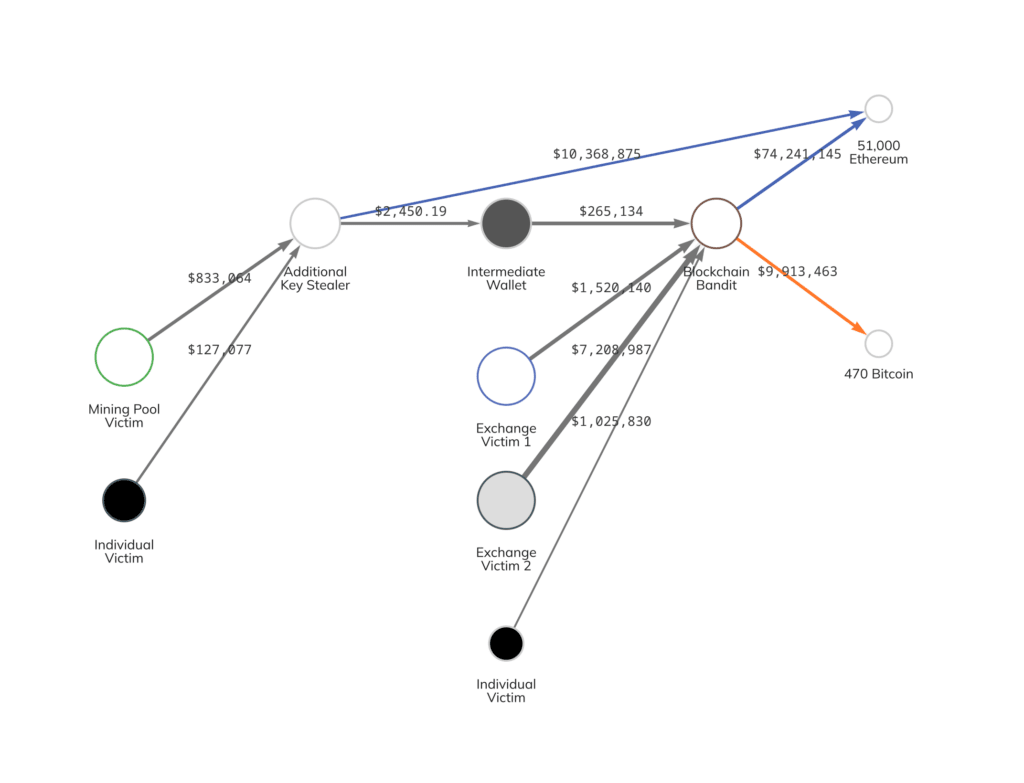
There have previously been security incidents regarding "pseudo-random wallets" where some wallets used pseudo-random algorithms to generate mnemonic phrases, resulting in vastly insufficient entropy. Hackers then brute-forced these wallets and systematically searched for weak private keys. In 2015, the hacker group Blockchain Bandit exploited faulty random number generators and code vulnerabilities to systematically search for weakly secured private keys, successfully uncovering over 700,000 vulnerable wallet addresses and stealing more than 50,000 ETH from them.
Of course, some geeks will use dice (making sure the dice are sufficiently fair) to roll random numbers and map them to the BIP39 word list, which is considered manually secure, but for most people, there's no need to complicate things, as it can lead to mistakes.
Three, can we brute-force V God or other whale wallets?
This is a question I also imagined back in the day, fantasizing about generating a wallet address and finding over a million ETH inside, instantly achieving financial freedom and directly stealing from some whale.
I have to say, just thinking about it is quite tempting. But the reality is: the probability is almost zero.
Why? Because the possible combinations of mnemonic phrases are so exaggerated that they exceed human imagination:
12 words: valid combinations approximately 2¹²⁸ ≈ 3.4 × 10³⁸
24 words: valid combinations approximately 2²⁵⁶ ≈ 1.16 × 10⁷⁷
What is the concept of this magnitude?
We all know that there is an uncountable amount of sand on Earth, but scientists have estimated an approximate value; assuming all the beaches and deserts on Earth combined, the total number of grains of sand is about 7.5×10¹⁸ grains, which also means:
The valid combinations for 12 words are equivalent to 4.5 × 10¹⁹ times the total number of sand grains on Earth.
The valid combinations for 24 words are even more, at 1.5 × 10⁵⁸ times the total number of sand grains on Earth.
In other words, it’s like every grain of sand on Earth becomes a "new Earth," and within each new Earth, there are beaches and sand, and then you have to randomly find the one grain of sand you marked among all these grains at once.
This has far exceeded what humans can imagine in scale.
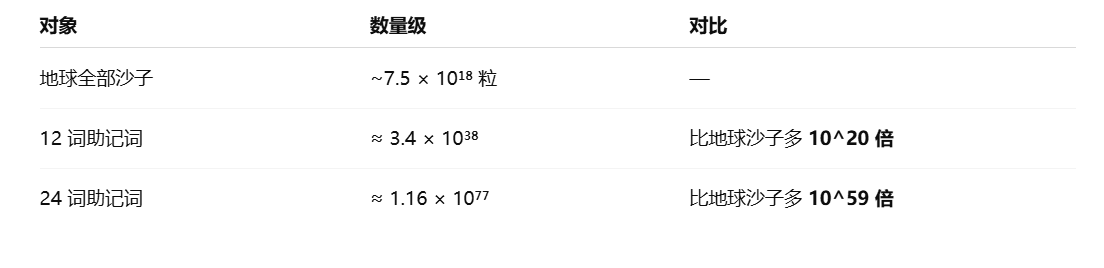
Therefore, the probability of brute-forcing a wallet is not "extremely low," but, under known physics and computing power, it is essentially zero. Relying on "brute-forcing" to get rich is worse than buying a lottery ticket, where the odds of winning are much higher.
Returning to the movie's setting: if someone really only lacks one mnemonic word, it is indeed possible to attempt to brute-force it.
Finally, here are some safety tips regarding wallets/mnemonic phrases/private keys:
Prioritize using unmanaged wallets that have been tested over time and by the market, and have undergone open-source code audits, such as MetaMask, Trust Wallet, SafePal, etc., and conditionally use hardware wallets directly;
Never screenshot, store in cloud storage, copy and paste, or send to others your mnemonic phrase and private key;
It is best to write it down on paper (consider using a stainless steel mnemonic board, moisture-proof, fireproof, and corrosion-resistant), keep it in a safe place, and have 2-3 backups in different locations;
Public keys/addresses can be safely made public; they are like your house number, but be cautious of phishing links;
It is recommended to manage wallets on clean devices, and do not casually install unknown plugins or apps;
Remember this: Anyone who asks you for your mnemonic phrase is 100% a scammer.



