On August 11, 2025, the Qubic platform announced a 51% attack on the Monero network, before later indicating its intention to target Dogecoin. Although this news raised concerns in the crypto community, the Monero network was not significantly affected, leading many to consider what happened as more of a media stunt than a real threat.
Project Background
* Qubic was founded in 2012 by Sergey Ivancheglo (known as Come-from-Beyond).
It positions itself as a platform based on *Useful Proof of Work (PoUW)*, where computational power is directed towards practical tasks like training AI models.

The *Quorum-Based Computation* protocol enables a standard processing speed of up to 15.5 million transactions per second.
Details of the attack on Monero
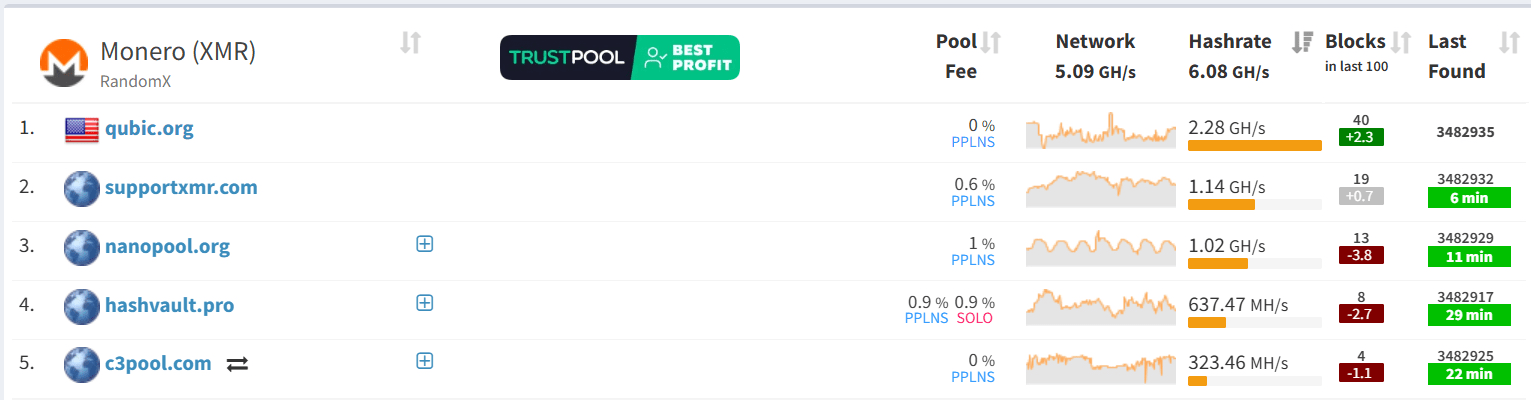
Initially, Qubic directed its resources toward mining *XMR* and training its artificial intelligence.
* The community sold mined XMR and bought QUBIC tokens to be burned, creating a deflationary effect.
* The mechanism was later adjusted to distribute half of the proceeds to the miners.
* The attack caused an increase in media interest in the Qubic project.
Meanwhile, the Monero network continued to operate normally without interruption.
Results
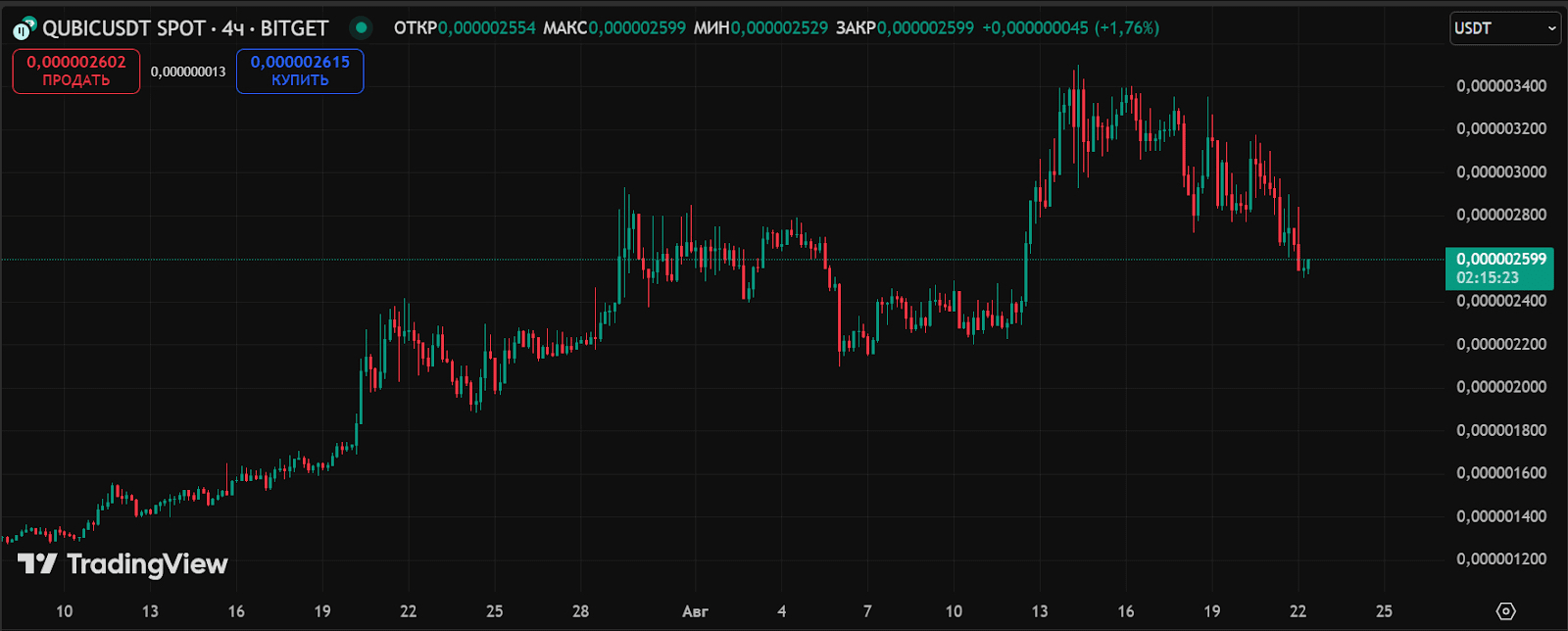
The price of *QUBIC* rose by 75% after the announcement, before declining slightly.
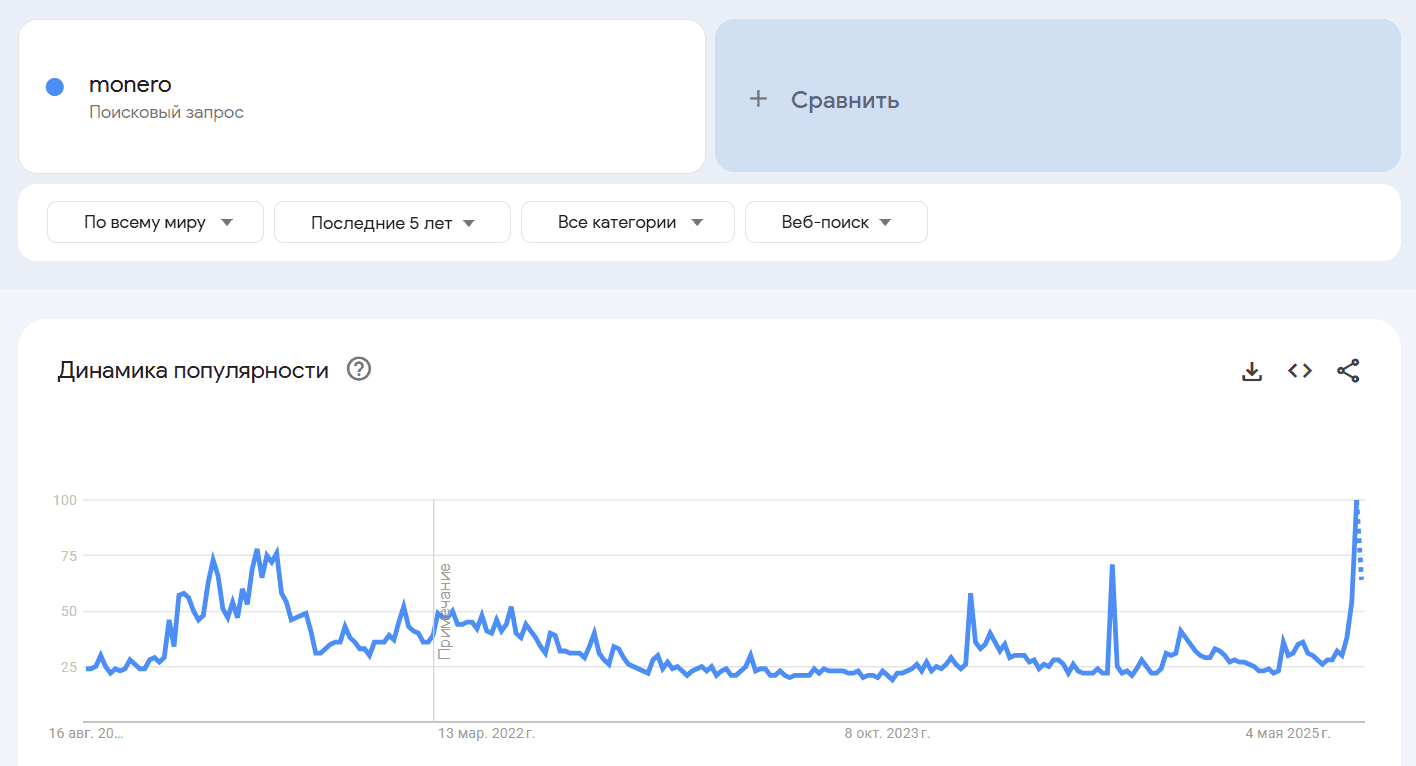
The price of *Monero* temporarily dropped but quickly recovered.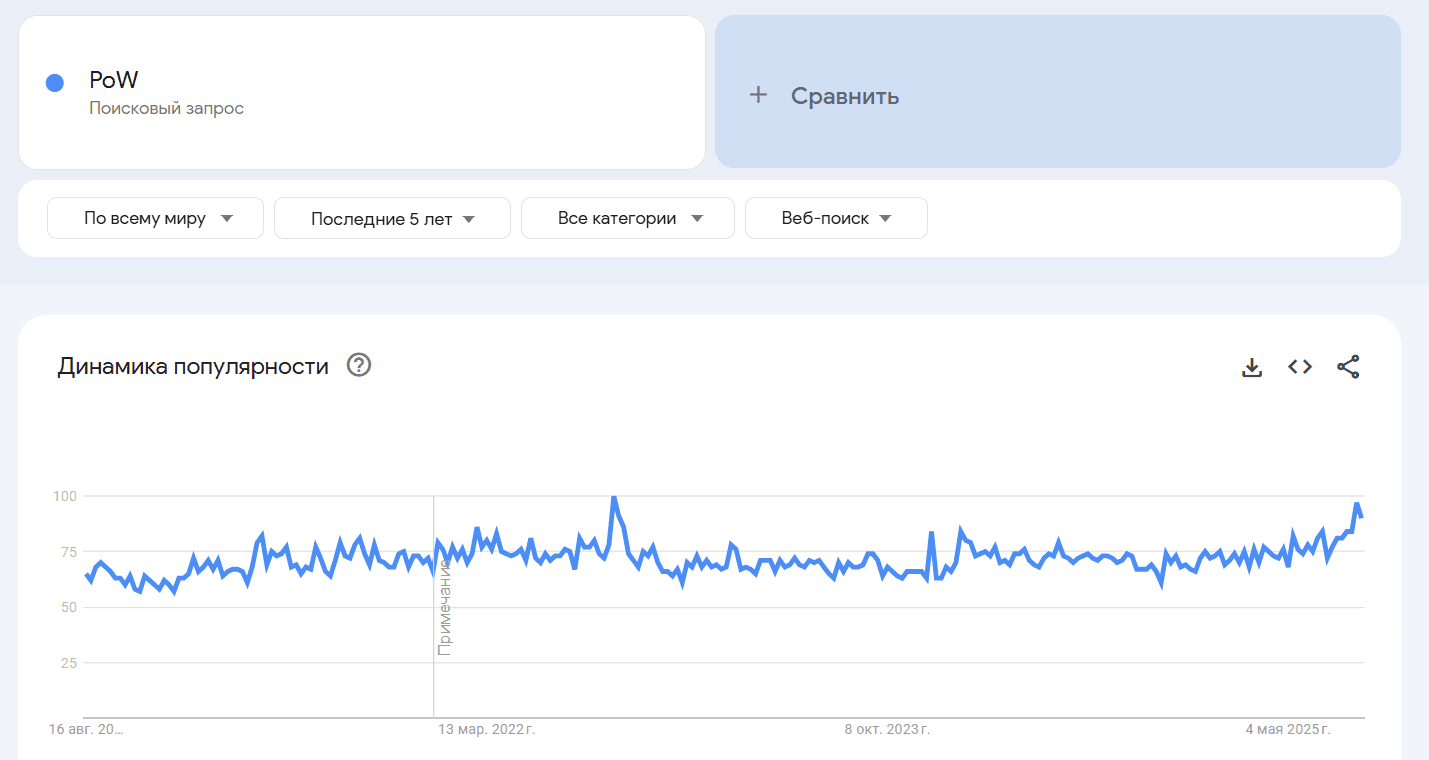
* Searches for Monero and PoW saw significant jumps in Google Trends.
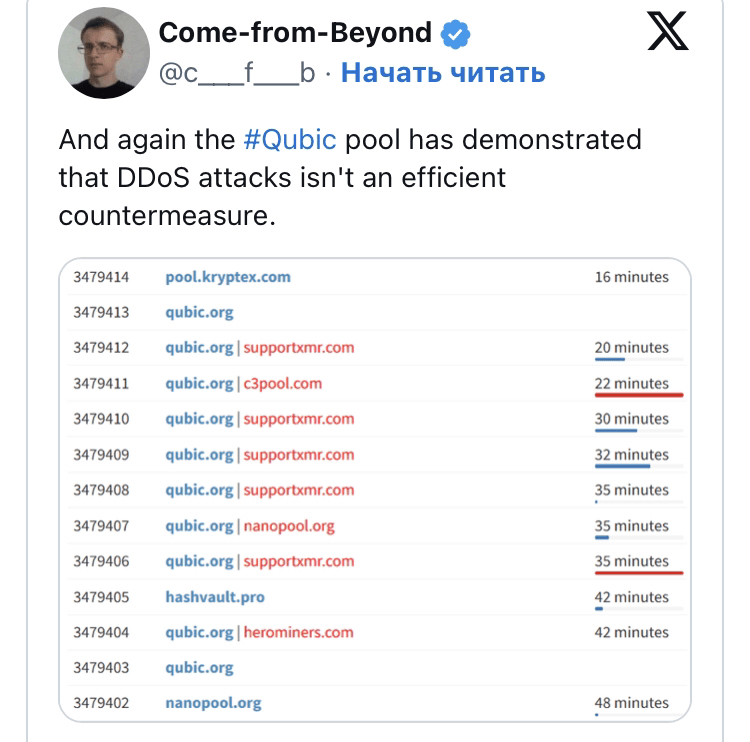
* Qubic itself was subjected to a DDoS attack that lasted over a week.
Summary
What happened with Monero was not an existential threat as much as it was a real-world experiment to test Qubic's capabilities and draw attention to its project.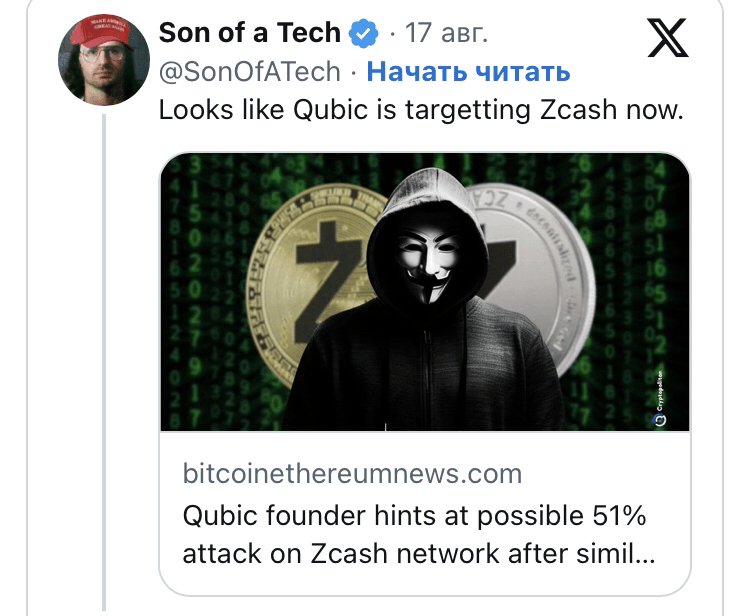
Despite the hype, Monero remained stable and secure, while Qubic bolstered its reputation.
But this move raises ethical questions about the limits of competition among blockchain projects, and whether "showboating" could become a recurring tool in the industry.
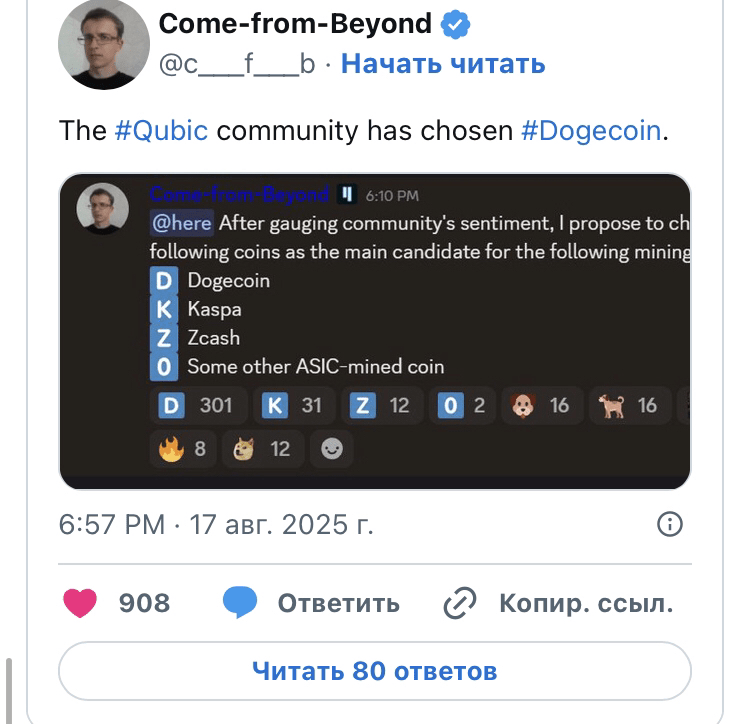
The Qubic community is set to turn its sights toward Dogecoin as the next "educational target," which means that the coming months may see broader discussions about the security of Proof of Work (PoW) networks and strategies to protect them.
Follow us for reliable and simplified information.
@kava _CHAIN
