Many people's first question is—'Is it really safe to put my$BTC into#Bitlayer ?'
To answer this question, one must first understand Bitlayer's security architecture, trust assumptions, and what actions can be taken when disputes or anomalies occur.
1. Sources of Bitlayer's Security
Bitlayer is built on the Bitcoin-native #安全 architecture as a #BitVM-style Rollup, with its security primarily derived from a three-layer design:
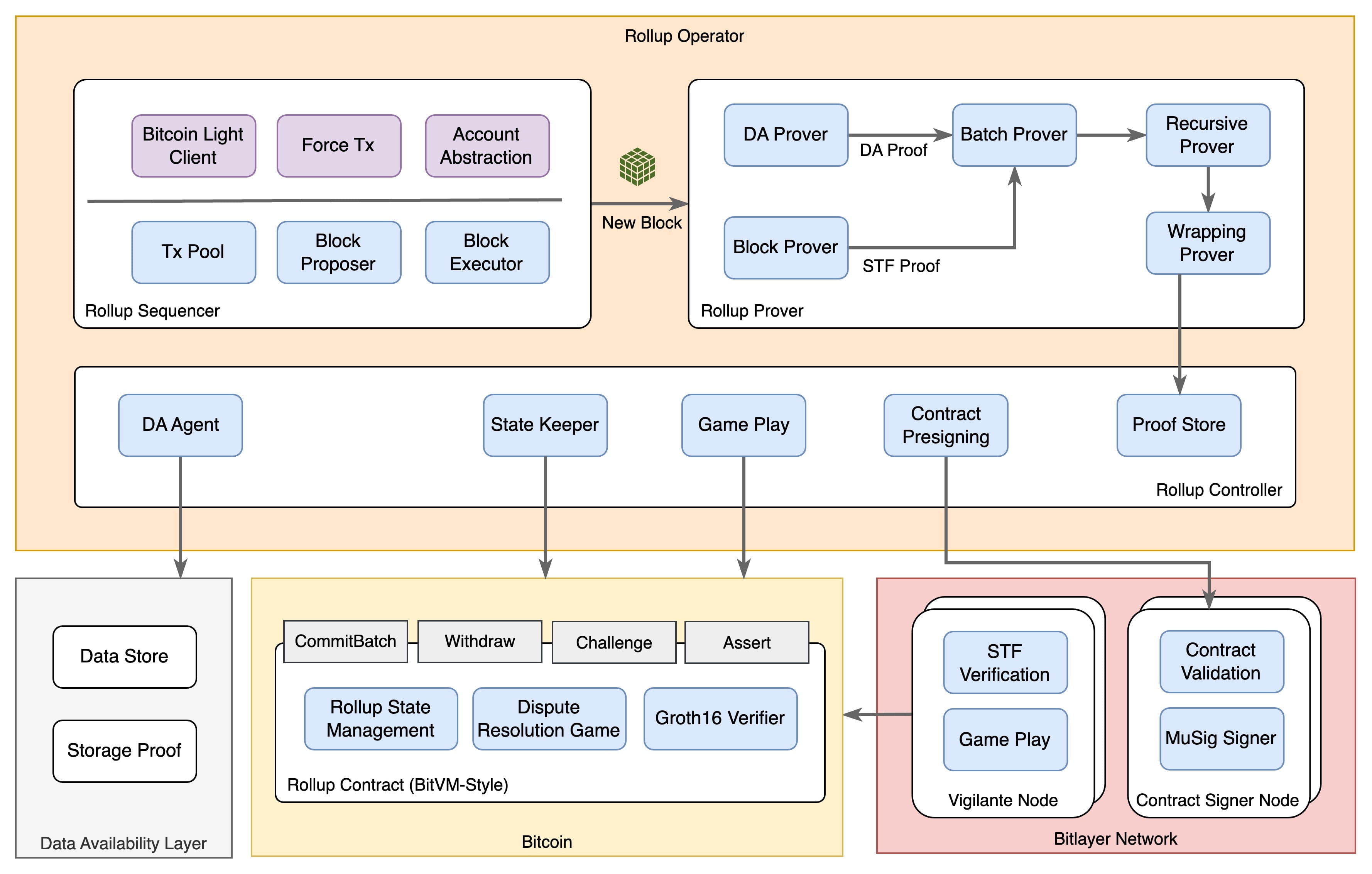
L1 Finality
All L2 state transitions are ultimately anchored in Bitcoin, utilizing Bitcoin's immutability and PoW consensus to ensure finality.
As long as L1 is not reorganized, your final state will not be arbitrarily altered.
BitVM Challenge/Verification Mechanism
Rollup state changes must be verified through the BitVM contract; any malicious or erroneous state submissions can be detected by watcher nodes during the challenge period and counter-evidence can be submitted.Data Availability Layer (DA Layer)
All batch transaction data will be submitted to the DA layer to ensure data can be publicly verified.
If the operator wants to censor or hide transactions, users can directly submit 'Forced Transactions' to the DA layer.
2. Challenge Period
What is the Challenge Period?
The challenge period refers to the time after the L2 state is submitted to L1, allowing other nodes to check and raise objections.
What can users do during the challenge period?
Monitor L2 State: Through watchers or by running your own nodes, compare whether state transitions are correct.
Challenge Submission: If a state anomaly is detected, evidence can be submitted to L1 (the BitVM contract on Bitcoin) to request verification and rollback erroneous states.
Impact: A successful challenge can prevent malicious states from taking effect and protect asset security.
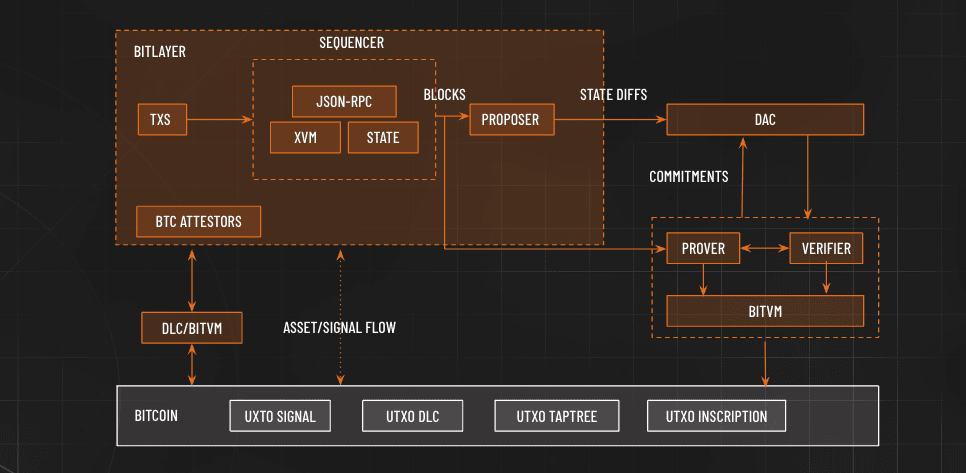
3. Data Availability (DA)
Why is it Important?
Even if the verification logic is correct, if the transaction data is not public, users cannot independently verify the status or present evidence during the challenge period.
Bitlayer's DA Design:
The operator submits L2 batches to the DA layer.
Users can directly send 'Forced Transactions' to the DA layer to bypass the operator and avoid censorship.
Risks of Poor Data Availability:
Users cannot verify the status of their assets and may miss the challenge period.
Data loss can hinder normal block production or exit from L2.
4. Exit Path is Extremely Important!!!
If there is an anomaly in L2 (such as the operator going offline, censorship, or malicious behavior), how should you safely exit?
Normal Exit: When L2 burns assets (such as YBTC), retrieve BTC from L1 after verification during the challenge period.
Emergency Exit: Submit the last available state directly through the DA layer and L1 contract's exit mechanism, bypassing the operator.
Phased Exit: When risks are elevated, gradually transfer assets back to L1 to reduce the amount of cross-chain transfers at once.
5. Risk Map + Yield Comparison Table

6. Impact on General Users
Enhanced Security: You don't have to fully trust a single operator; the challenge mechanism and DA layer provide you with an additional safety net.
Controllable Risk: Through small-scale testing, phased bridging, and exit path design, risks can be partially quantified and controlled.
Learning Cost: A basic understanding of the challenge period, DA layer, and exit mechanism is required; otherwise, it will be difficult to respond promptly in a crisis.
Yield Space: With safety ensured, YBTC can access L2 and cross-chain strategies, bringing potential returns higher than holding assets on L1.
So the question arises! If there is an anomaly in L2, would you prioritize 'normal waiting to exit' or 'immediate emergency exit'? Why?
#Bitlayer @BitlayerLabs
Key Focus of Security Model: Challenge Period, Data Availability, Exit Path