The hackers waited 16 months to drain $908,000 in USDC, revealing how old vulnerabilities can strike late.
A user lost nearly $1 million in USDC due to a scam linked to a malicious contract signed 458 days ago. Experts warn that this delayed exploitation has become a common strategy among cryptocurrency thieves.
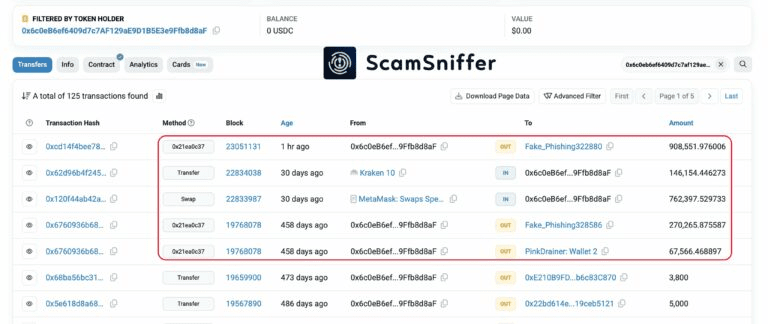
A cryptocurrency user lost $908,551 in USD Coin [USDC] after falling victim to a scam that drained the wallet and exploited a malicious contract approval signed over 15 months ago.
Source: X
According to onchain data, the victim approved a malicious smart contract on April 30, 2024, likely through a fake airdrop or a phishing site disguised as a legitimate platform.
After that, the scammer patiently waited for about 16 months before executing the final blow on August 2, 2025, draining the victim's wallet of nearly a million dollars in USDC.
How old wallet approvals can become scary
The attack dates back to an ERC-20 approval that silently allowed access to the scam wallet '0x67E5Ae' linked to the address pink-drainer.eth.
The contract allows tokens to be transferred without any additional confirmation from the user.
According to Scam Sniffer, which reported the incident on site X, the theft occurred 458 days after the victim unknowingly approved the malicious transaction.
Shortly after that, Scam Sniffer went to X and noticed,
"Review and regularly revoke old approvals - the security of your wallet is important!"
In this case, the previously hacked wallet showed minimal low-value activity, which likely helped it move under the radar.
How did this start?
Things took a sharp turn on July 2.
The victim transferred $762,397 from MetaMask to a new wallet (0x6c0eB6) at 8:41 PM UTC.
Just ten minutes later, they added an additional amount of $146,154 from a Kraken account. These movements were announced on the network, likely alerting the scammer.
Instead of moving immediately, the attacker waited another month, likely to confirm no additional withdrawals or deposits. Then he executed his attack at 4:57 AM UTC on August 2.
The stolen funds were sent to an address labeled Fake_Phishing322880 and marked by Scam Sniffer as malicious.
Scams have become more sophisticated
This shows that the increase in cryptocurrency-related scams is becoming more complex day by day, as criminals exploit technology and trust.
From deepfakes created by AI of Ripple executives to impersonated YouTube channels promoting fake XRP giveaways, scammers exploit realism to deceive unsuspecting users.
Meanwhile, the emergence of a massive leak of 16 billion standard credentials has increased risks across platforms.
In one concerning case, a targeted phishing attack used a mix of urgency, impersonation, and cross-platform manipulation to deceive even a seasoned cybersecurity expert.
Even experienced users fell victim.
Source: Galaxy
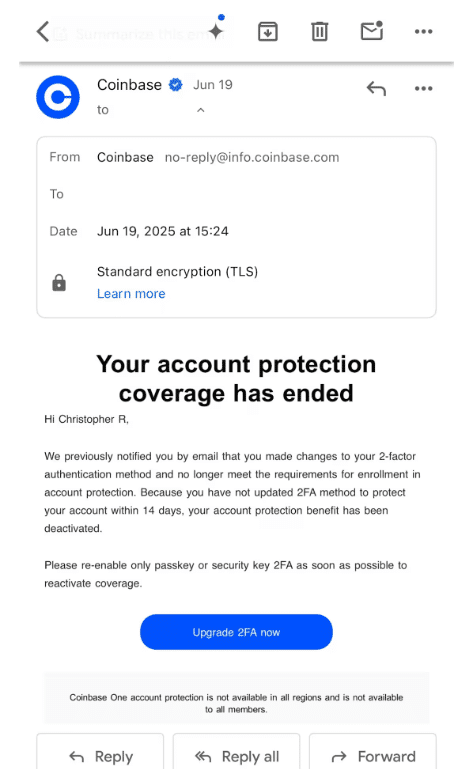
Even cybersecurity analyst Christopher Rosa fell victim to a scam using fake emails, bogus Coinbase calls, and coordinated social engineering.
The bottom line is clear but vital: old approvals do not expire, and attackers do not forget.